
Best Hardware Firewalls for DDoS Protection

- Top Hardware Firewall Solutions for Robust DDoS Protection
- Best Hardware Firewalls for DDoS Protection: A Detailed Guide
- Which hardware firewalls provide the most effective DDoS protection for enterprise networks?
- Among available hardware firewalls, which models are considered optimal for defending against DDoS attacks?
- What security prevention mechanisms do the top-rated hardware firewalls implement specifically for DDoS mitigation?
- Which hardware firewall solutions are most commonly deployed for DDoS protection in corporate environments?
- More information of interest
- What are the key features to look for in a hardware firewall for DDoS protection?
- Which hardware firewalls are considered top-tier for enterprise DDoS mitigation?
- How does a hardware firewall differentiate between legitimate traffic and DDoS attacks?
- Can hardware firewalls alone provide complete protection against all DDoS attack types?
Best Hardware Firewalls for DDoS Protection, in an increasingly interconnected digital landscape, Distributed Denial of Service (DDoS) attacks pose a significant threat to network integrity and business continuity. These attacks can cripple services, disrupt operations, and result in substantial financial losses. To counter such threats, deploying robust security infrastructure is paramount.

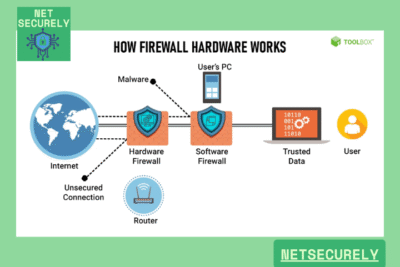
Among the most effective solutions are hardware firewalls, specifically engineered to identify, mitigate, and neutralize DDoS assaults in real-time. This article provides an in-depth analysis of the top-performing devices in the market, offering insights to help organizations select the most appropriate defense mechanisms. Discover the definitive guide to the , ensuring your network remains resilient against evolving cyber threats.
You may also be interested in reading: Best Home Firewalls for IoT Device Security
Top Hardware Firewall Solutions for Robust DDoS Protection
When selecting the Best Hardware Firewalls for DDoS Protection, it is essential to consider factors such as throughput capacity, advanced mitigation techniques, and scalability. These devices are engineered to inspect and filter traffic at the network perimeter, identifying and blocking malicious packets before they can impact services. Key features include deep packet inspection, behavioral analysis, and integration with threat intelligence feeds to ensure comprehensive defense against volumetric, protocol, and application-layer DDoS attacks.
Key Features to Look for in DDoS Protection Firewalls
Effective DDoS protection hardware firewalls must offer high availability, low latency, and real-time traffic analysis. Critical features include automatic attack detection, granular traffic shaping, and SSL/TLS inspection capabilities. Additionally, support for BGP (Border Gateway Protocol) integration and custom rule sets allows for adaptive responses to evolving threats, ensuring minimal service disruption during an attack.
Leading Hardware Firewall Models for Enterprise DDoS Defense
Prominent models in the category of Best Hardware Firewalls for DDoS Protection include offerings from vendors such as Fortinet, Cisco, and Palo Alto Networks. These appliances are designed for high-performance environments, with throughput rates exceeding 100 Gbps and specialized ASICs for efficient packet processing. Enterprises should evaluate models based on their network architecture and specific threat profiles.
Performance Metrics: Throughput and Latency Considerations
Throughput and latency are decisive factors in DDoS mitigation. Hardware firewalls must maintain line-rate performance even under attack conditions to avoid becoming bottlenecks. Metrics such as packets per second (PPS) and concurrent connection capacity directly impact the effectiveness of DDoS protection, ensuring legitimate traffic flows uninterrupted while malicious data is discarded.
Integration with Existing Network Infrastructure
Seamless integration is crucial for deploying hardware firewalls without disrupting current operations. Compatibility with existing routers, switches, and security information and event management (SIEM) systems enables centralized monitoring and coordinated responses. Features like virtual wire deployment and support for standard networking protocols facilitate straightforward implementation into diverse environments.
Cost Analysis and ROI of DDoS Protection Appliances
Investing in dedicated hardware for DDoS protection involves evaluating upfront costs, licensing fees, and maintenance expenses against potential losses from downtime. A well-chosen appliance can provide significant return on investment (ROI) by preventing revenue loss, reputational damage, and regulatory penalties. Organizations should consider total cost of ownership (TCO) alongside the solution’s efficacy and scalability.
| Vendor | Model | Max Throughput | DDoS Mitigation Techniques |
| Fortinet | FortiGate 6000 Series | > 100 Gbps | AI-Powered Threat Intelligence, IP Reputation |
| Cisco | Firepower 4100 Series | 60 Gbps | NetFlow Analysis, Anomaly Detection |
| Palo Alto Networks | PA-5200 Series | 50 Gbps | App-ID, Custom Signatures |
| Check Point | Quantum 15000 | > 90 Gbps | ThreatCloud, Behavioral Analysis |
| Juniper Networks | SRX5800 | 40 Gbps | Flow-Based Processing, Rate Limiting |
Best Hardware Firewalls for DDoS Protection: A Detailed Guide
Which hardware firewalls provide the most effective DDoS protection for enterprise networks?

Enterprise-grade hardware firewalls offering the most effective DDoS protection typically include models from Palo Alto Networks PA-7000 Series with advanced threat prevention, Fortinet's FortiGate 6000/7000 Series featuring dedicated security processors and AI-powered mitigation, Cisco Firepower 4100/9300 Series with integrated Cisco Talos intelligence and multi-layer inspection, and Check Point Quantum Security Gateways utilizing advanced IPS and behavioral analysis to detect and block volumetric, protocol, and application-layer attacks while maintaining high-throughput performance and low-latency operations essential for enterprise environments.
Key Features of Top-Tier Hardware Firewalls
The Best Hardware Firewalls for DDoS Protection incorporate high-capacity throughput (often 100Gbps+), dedicated DDoS mitigation hardware like ASICs or FPGAs, behavioral analysis for zero-day attacks, and integrated threat intelligence feeds; for example, Palo Alto's PA-7080 handles 1.2Tbps throughput with App-ID technology, while FortiGate 7060E uses SPU processors for 400Gbps mitigation, ensuring enterprises can withstand large-scale attacks without degradation.
Performance Comparison of Leading Models
| Firewall Model | Max Throughput | DDoS Mitigation Capacity | Key Technology |
|---|---|---|---|
| Palo Alto PA-7080 | 1.2 Tbps | Multi-vector inspection | App-ID, Threat Prevention |
| FortiGate 7060E | 400 Gbps | AI-powered detection | Security Processing Units |
| Cisco Firepower 9300 | 300 Gbps | Integrated Talos intelligence | Snort IPS, SSL decryption |
| Check Point 64000 | 238 Gbps | Behavioral threat modeling | ThreatCloud AI, IPS blades |
Implementation Considerations for Enterprises
Deploying these solutions requires assessing network architecture (inline vs. out-of-path), scalability for future growth, compatibility with existing infrastructure, and management overhead; enterprises should prioritize models with centralized management consoles (e.g., FortiManager, Panorama), automated response policies, and real-time analytics to minimize false positives and ensure seamless operation during attacks.
Among available hardware firewalls, which models are considered optimal for defending against DDoS attacks?

For enterprises seeking robust protection against distributed denial-of-service attacks, the Best Hardware Firewalls for DDoS Protection typically include models with high-throughput capabilities, dedicated mitigation hardware, and advanced behavioral analysis features; top contenders in this category are Fortinet's FortiGate 6000 and 4000 series, which offer specialized security processors and AI-powered threat intelligence, Palo Alto Networks' PA-7000 series with its single-pass architecture and hardware-accelerated threat prevention, and Juniper Networks' SRX Series Firewalls, particularly the SRX5800 and SRX5400 models, which integrate dynamic attack detection and scalable mitigation capacities to handle volumetric, protocol, and application-layer attacks efficiently while maintaining network performance.
Fortinet FortiGate Series Capabilities
Fortinet's FortiGate series, especially the 6000 and 4000 models, are engineered with custom Security Processing Units (SPUs) that offload DDoS mitigation tasks from the main CPU, enabling them to sustain multi-gigabit throughput even during large-scale attacks. These firewalls leverage FortiGuard AI-Powered Security Services for real-time threat intelligence and automated response mechanisms, effectively identifying and blocking sophisticated DDoS patterns such as DNS amplification, SYN floods, and HTTP/HTTPS exhaustion attacks through deep packet inspection and behavioral analysis.
Palo Alto Networks PA-7000 Series Features
The Palo Alto Networks PA-7000 series firewalls utilize a single-pass architecture combined with dedicated hardware-accelerated threat prevention, making them highly effective against application-layer DDoS attacks. These devices excel in decrypting and inspecting encrypted traffic without performance degradation, employing machine learning-based policies to distinguish legitimate user traffic from malicious bots. Key features include App-ID for application identification, automated signature updates, and granular control over traffic flows to mitigate attacks targeting specific services or protocols.
Juniper Networks SRX Series Performance
Juniper Networks' SRX Series, particularly the SRX5800 and SRX5400, are designed for high-availability environments requiring scalable DDoS defense. They integrate dynamic attack detection engines and flow-based monitoring to identify anomalies in real-time, with the ability to deploy countermeasures such as rate limiting, source-based filtering, and TCP reassembly checks. The SRX firewalls support integrated mitigation profiles that can be customized based on network traffic patterns, ensuring minimal false positives while maintaining uptime during sustained attacks.
| Model Series | Key DDoS Mitigation Features | Maximum Throughput |
|---|---|---|
| FortiGate 6000/4000 | SPU hardware acceleration, AI-based FortiGuard | Up to 1 Tbps |
| Palo Alto PA-7000 | Single-pass architecture, App-ID profiling | Up to 400 Gbps |
| Juniper SRX5800/5400 | Flow-based detection, dynamic rate limiting | Up to 200 Gbps |
What security prevention mechanisms do the top-rated hardware firewalls implement specifically for DDoS mitigation?
Top-rated hardware firewalls implement comprehensive DDoS mitigation mechanisms including stateful packet inspection to validate connection legitimacy, rate limiting to cap traffic volumes per source, and behavioral analysis to detect anomalies in real-time. They employ deep packet inspection (DPI) to identify malicious payloads, IP reputation filtering to block known malicious sources, and synchronized security with other network devices for coordinated response. Additionally, these firewalls utilize dedicated mitigation hardware such as ASICs for high-throughput processing without performance degradation, ensuring minimal latency during attacks while maintaining service availability for legitimate traffic, making them the Best Hardware Firewalls for DDoS Protection.
Stateful Inspection and Rate Limiting
Stateful inspection ensures only legitimate connections traverse the network by tracking active sessions and validating packet sequences, while rate limiting imposes thresholds on traffic volume from individual IPs or subnets to prevent overwhelming resources. These mechanisms work in tandem to filter out volumetric attacks like UDP floods or ICMP floods before they impact critical infrastructure, with granular controls allowing administrators to set policies based on protocol, port, or application type. For example, a firewall might permit 1000 packets per second from a trusted zone but only 100 from external sources, dynamically adjusting during suspected attacks.
Behavioral Analysis and Anomaly Detection
Behavioral analysis establishes baselines for normal network traffic patterns—such as bandwidth usage, connection rates, and protocol distribution—and flags deviations indicative of DDoS activity, like sudden spikes in DNS queries or HTTP requests. This proactive approach enables early detection of sophisticated attacks, including low-and-slow attacks that evade traditional thresholds, by using machine learning algorithms to refine models over time. Upon detection, the system can automatically trigger mitigation protocols, such as diverting traffic to scrubbing centers or applying stricter filters.
Hardware Acceleration and Scalability
Top-tier firewalls leverage specialized hardware like application-specific integrated circuits (ASICs) and field-programmable gate arrays (FPGAs) to perform resource-intensive tasks—such as encryption, decryption, and packet analysis—at multi-gigabit speeds without CPU overhead. This ensures mitigation scales linearly with attack size, maintaining performance even under massive traffic loads, and supports features like hardware-based SSL inspection to detect encrypted threats. The table below compares key scalability attributes:
| Feature | Benefit | Example Implementation |
|---|---|---|
| ASIC-Based Processing | Line-rate throughput for deep packet inspection | FortiGate 6000 series |
| FPGA Flexibility | Adaptable to new attack vectors via firmware updates | Palo Alto Networks PA-7000 series |
| Dedicated Mitigation Cores | Isolates DDoS processing from general firewall functions | Cisco Firepower 4100 series |
Which hardware firewall solutions are most commonly deployed for DDoS protection in corporate environments?
The most commonly deployed hardware firewall solutions for DDoS protection in corporate environments include Fortinet FortiGate series with specialized ASIC-powered threat protection, Palo Alto Networks PA-Series firewalls leveraging advanced threat prevention and App-ID technology, Cisco Firepower Threat Defense (FTD) appliances integrating NGFW capabilities with dedicated DDoS mitigation modules, and Check Point Quantum Security Gateways featuring multi-layered security with real-time threat intelligence. These enterprise-grade solutions typically incorporate dedicated DDoS mitigation hardware, behavioral analysis engines, and high-availability clustering to withstand large-scale volumetric attacks while maintaining legitimate traffic flow, making them the preferred choice for organizations requiring robust perimeter security against sophisticated distributed denial-of-service threats.
Enterprise-Grade Firewall Platforms with Integrated DDoS Protection
Major corporate environments typically deploy comprehensive security platforms that combine next-generation firewall capabilities with specialized DDoS mitigation features. The Best Hardware Firewalls for DDoS Protection often include Fortinet FortiGate appliances utilizing Security Processing Units (SPUs) for accelerated threat detection, Palo Alto Networks PA-Series with advanced traffic normalization capabilities, and Cisco Firepower devices incorporating dedicated threat defense modules. These solutions employ deep packet inspection, rate-based filtering, and anomaly detection algorithms to identify and mitigate various DDoS attack vectors while maintaining legitimate business traffic.
| Firewall Model | Maximum Throughput | DDoS Protection Features |
|---|---|---|
| FortiGate 6000F | 1.2 Tbps | ASIC-accelerated mitigation, AI-powered detection |
| Palo Alto PA-7000 | 400 Gbps | App-ID technology, behavioral threat protection |
| Cisco Firepower 4100 | 80 Gbps | Multi-vector attack protection, TLS/SSL inspection |
| Check Point 6000 | 200 Gbps | IPS protection, threat emulation |
Specialized DDoS Mitigation Appliances for Large Enterprises
Large corporations frequently deploy dedicated DDoS mitigation appliances that work in conjunction with their existing firewall infrastructure. These specialized systems include Radware DefensePro devices offering real-time attack mitigation with behavioral-based detection, F5 Silverline hybrid solutions providing cloud-scale protection with on-premises hardware components, and Arbor Networks APS systems delivering multi-layer DDoS protection. These appliances feature high-capacity scrubbing centers, custom ASIC processors, and global threat intelligence networks that can handle volumetric attacks exceeding several hundred gigabits per second while maintaining sub-second response times.
Hybrid and Cloud-Integrated Hardware Solutions
Modern corporate deployments often utilize hybrid approaches where on-premises hardware firewalls integrate with cloud-based DDoS protection services. This architecture combines local hardware appliances from vendors like Juniper Networks SRX Series or SonicWall NSA platforms with cloud scrubbing services from providers such as Cloudflare Magic Transit or AWS Shield Advanced. The on-premises hardware performs initial filtering and attack detection while automatically rerouting malicious traffic to cloud-based scrubbing centers during large-scale attacks, creating a layered defense strategy that provides both low-latency protection for legitimate traffic and massive scalability during extreme DDoS events.
More information of interest
What are the key features to look for in a hardware firewall for DDoS protection?
When selecting a hardware firewall for DDoS protection, prioritize features such as high throughput capacity, real-time traffic analysis, behavioral-based detection, and the ability to mitigate various attack types including volumetric, protocol, and application-layer attacks. Scalability and integration with existing network infrastructure are also critical considerations.
Which hardware firewalls are considered top-tier for enterprise DDoS mitigation?
Top-tier hardware firewalls for enterprise DDoS mitigation include solutions from Fortinet (FortiGate series), Cisco (Firepower Threat Defense), Palo Alto Networks (PA-Series), and Juniper Networks (SRX Series). These devices offer advanced threat intelligence, automated response mechanisms, and robust performance under heavy attack loads.
How does a hardware firewall differentiate between legitimate traffic and DDoS attacks?
A hardware firewall distinguishes legitimate traffic from DDoS attacks using techniques such as deep packet inspection, rate limiting, IP reputation filtering, and anomaly detection algorithms. By establishing baselines for normal traffic behavior, the firewall can identify and block suspicious patterns in real time while allowing genuine requests to pass through.
Can hardware firewalls alone provide complete protection against all DDoS attack types?
While hardware firewalls are highly effective against many DDoS attacks, they are often most successful when deployed as part of a multi-layered defense strategy. Combining on-premises hardware with cloud-based DDoS protection services ensures comprehensive coverage, especially for extremely large volumetric attacks that may exceed local bandwidth capacities.





Deja una respuesta