
Enterprise Firewalls for Robust Network Defense

- Essential Components of Enterprise Firewalls for Robust Network Defense
- Enterprise Firewalls for Robust Network Defense: A Detailed Guide
- What constitutes a robust firewall in enterprise network defense?
- What are the best practices for implementing robust network architecture security with enterprise firewalls?
- How do enterprise firewalls contribute to robust network defense strategies?
- Which enterprise firewall solutions are utilized by the Department of Defense for robust network defense?
- More information of interest
Enterprise Firewalls for Robust Network Defense, in today's interconnected digital landscape, organizations face escalating cybersecurity threats that demand sophisticated protection mechanisms. Enterprise firewalls for robust network defense serve as the critical first line of protection against unauthorized access and malicious traffic. These advanced security solutions go beyond traditional perimeter defense by incorporating deep packet inspection, intrusion prevention systems, and application-aware filtering capabilities.

Properly configured enterprise firewalls create segmented security zones, enforce granular policies, and provide comprehensive visibility into network activities. Implementing these defenses is essential for maintaining data integrity, ensuring regulatory compliance, and safeguarding organizational assets against evolving cyber threats in complex enterprise environments.
You may also be interested in reading: Best Cheap VPS with High Performance
Essential Components of Enterprise Firewalls for Robust Network Defense
Enterprise Firewalls for Robust Network Defense represent a critical infrastructure component designed to monitor and control incoming and outgoing network traffic based on predetermined security rules. These sophisticated security systems establish a barrier between secured internal networks and untrusted external networks, employing multiple filtering methods including packet filtering, stateful inspection, and deep packet inspection. Modern enterprise firewalls incorporate advanced threat prevention capabilities such as intrusion prevention systems (IPS), application awareness, and integration with threat intelligence feeds to provide comprehensive protection against evolving cyber threats.
Core Functionality and Traffic Filtering Mechanisms
Enterprise firewalls operate through multiple filtering methodologies to ensure comprehensive network protection. Packet filtering examines individual packets based on source/destination IP addresses, ports, and protocols. Stateful inspection maintains awareness of active connections and makes decisions based on the connection state. Deep packet inspection analyzes the actual content of the traffic, enabling identification of malicious payloads disguised within legitimate protocols. Application-level gateways provide additional security by understanding specific applications and protocols, while proxy firewalls intercept and inspect all traffic before forwarding it to the destination.
Advanced Threat Protection Features
Modern enterprise firewalls incorporate sophisticated threat prevention capabilities that extend beyond traditional filtering. Intrusion Prevention Systems (IPS) actively monitor network traffic for signs of malicious activity and can automatically block detected threats. Integrated antivirus and anti-malware engines scan traffic for known malicious signatures. Sandboxing technology isolates and analyzes suspicious files in a safe environment before they reach the network. Threat intelligence integration provides real-time updates about emerging threats, while behavioral analysis detects anomalies that might indicate zero-day attacks or advanced persistent threats.
Architecture and Deployment Considerations
Enterprise firewall deployment requires careful architectural planning to ensure optimal performance and security. Organizations typically employ a defense-in-depth strategy with multiple firewall layers. Perimeter firewalls protect the network boundary, while internal firewalls segment the network into security zones. Distributed deployments might include branch office firewalls that connect to centralized management systems. Considerations include throughput requirements, redundancy configurations, high availability setups, and integration with other security components such as VPN gateways and web application firewalls.
Management and Monitoring Capabilities
Effective management is crucial for maintaining robust network defense through enterprise firewalls. Centralized management consoles provide unified control over multiple firewall instances across the organization. Real-time monitoring dashboards display network traffic patterns, security events, and threat detection statistics. Comprehensive logging capabilities record all security-relevant events for auditing and forensic analysis. Automated reporting tools generate compliance documentation and security posture assessments. Role-based access control ensures appropriate administrative privileges, while integration with Security Information and Event Management (SIEM) systems enhances overall security visibility.
Compliance and Regulatory Alignment
Enterprise firewalls play a vital role in meeting various regulatory compliance requirements across industries. They help organizations satisfy standards such as PCI DSS, HIPAA, GDPR, and SOX by providing necessary security controls and audit trails. Firewalls enforce access control policies required by compliance frameworks and generate documentation for regulatory audits. Data loss prevention features prevent unauthorized transmission of sensitive information, while detailed logging provides evidence of compliance efforts. Regular security assessments and vulnerability scanning integrated with firewall management help maintain ongoing compliance with evolving regulatory requirements.
| Firewall Type | Primary Function | Deployment Scenario |
| Next-Generation Firewall | Application awareness, integrated IPS, advanced threat protection | Network perimeter, data center protection |
| Web Application Firewall | HTTP/HTTPS traffic inspection, protection against web attacks | Application server front-end, cloud environments |
| Unified Threat Management | All-in-one security including firewall, antivirus, content filtering | Small to medium enterprises, branch offices |
| Cloud Firewall | Virtualized security for cloud infrastructure and applications | Public cloud environments, SaaS protection |
Enterprise Firewalls for Robust Network Defense: A Detailed Guide
What constitutes a robust firewall in enterprise network defense?
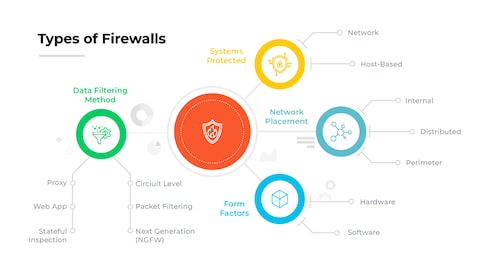
A robust enterprise firewall constitutes a multi-layered security system that integrates stateful packet inspection, deep packet inspection (DPI), application-level gateways, and intrusion prevention systems (IPS), all managed through centralized policy enforcement with real-time threat intelligence feeds and granular access controls segmented by user identity, device type, and application context, ensuring dynamic adaptation to emerging threats while maintaining comprehensive visibility and logging across all network traffic flows for continuous monitoring and forensic analysis.
Core Components of Enterprise Firewalls
Enterprise Firewalls for Robust Network Defense rely on several fundamental components working in unison, including stateful inspection to track active connections and enforce session-based rules, deep packet inspection (DPI) to analyze payload content for malicious patterns, and application-aware filtering to control specific software behaviors. These are complemented by integrated intrusion prevention systems (IPS) that actively block exploits, antivirus/anti-malware scanning engines, and SSL/TLS decryption capabilities to inspect encrypted traffic, all managed under a unified policy framework that ensures consistent security across the organization's network perimeter, internal segments, and cloud environments.
Advanced Threat Prevention Features
Modern enterprise firewalls incorporate advanced threat prevention mechanisms such as sandboxing for detonating suspicious files in isolated environments, behavioral analysis to detect zero-day attacks based on anomalous activities, and real-time threat intelligence integration from global security feeds to block known malicious IPs, domains, and signatures. These features are enhanced through machine learning algorithms that continuously adapt to new attack vectors, providing proactive defense against sophisticated threats like ransomware, advanced persistent threats (APTs), and polymorphic malware, while maintaining detailed logs and analytics for incident response and compliance reporting.
| Feature | Function | Benefit |
|---|---|---|
| Deep Packet Inspection (DPI) | Analyzes data payload beyond headers | Identifies hidden threats in application traffic |
| Intrusion Prevention System (IPS) | Monitors and blocks exploit attempts | Prevents vulnerability-based attacks |
| Application Control | Manages app-specific permissions | Enforces policies on SaaS and cloud apps |
| SSL/TLS Inspection | Decrypts and scans encrypted traffic | Eliminates blind spots in HTTPS flows |
Management and Integration Capabilities
Effective management of enterprise firewalls necessitates centralized administration consoles that provide unified policy deployment, real-time monitoring, and automated updates across distributed firewall instances, integrated with identity services (e.g., Active Directory, LDAP) for user-based access controls and SIEM systems for correlated security analytics. This is further strengthened through API-driven automation for orchestration with other security tools, scalable architecture to handle high-throughput traffic without performance degradation, and high availability configurations with failover mechanisms to ensure uninterrupted protection, all while maintaining compliance with regulatory standards through comprehensive auditing and reporting functionalities.
What are the best practices for implementing robust network architecture security with enterprise firewalls?
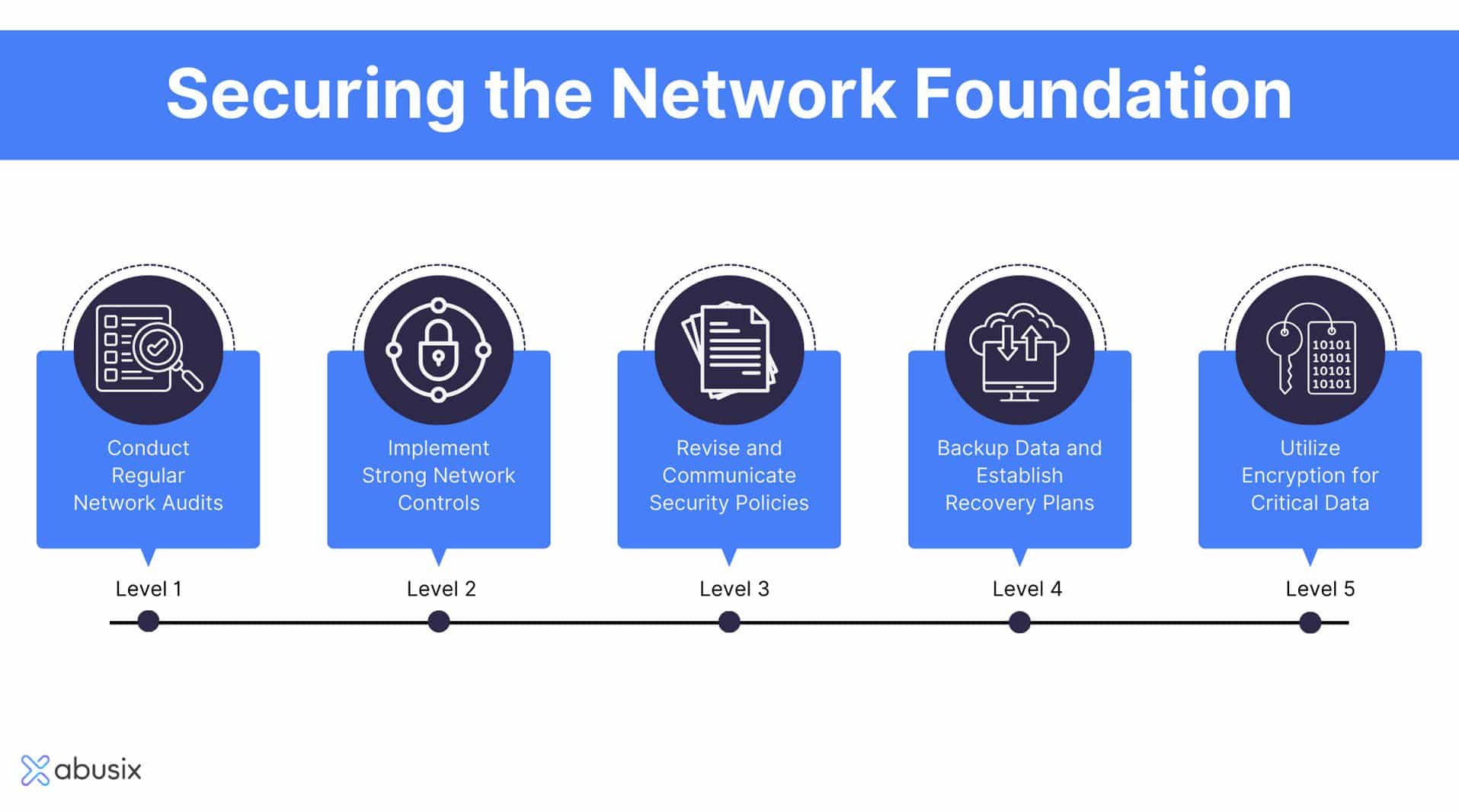
Implementing robust network architecture security with enterprise firewalls requires a multi-layered approach that begins with a defense-in-depth strategy, where firewalls are deployed at multiple network boundaries—including perimeter, internal segments, and cloud environments—to enforce strict access controls and segmentation. Best practices include adopting a zero-trust model, where all traffic is denied by default and only explicitly allowed based on the principle of least privilege; regularly updating firewall firmware and security policies to address emerging threats; employing intrusion prevention systems (IPS) and deep packet inspection (DPI) for real-time threat detection and mitigation; and continuously monitoring and logging traffic to identify anomalies and respond to incidents promptly. Additionally, integrating firewalls with other security tools—such as SIEM systems and threat intelligence platforms—enhances visibility and coordination, while regular security audits and penetration testing ensure policies remain effective and aligned with organizational risk posture, making Enterprise Firewalls for Robust Network Defense a cornerstone of modern cybersecurity infrastructure.
Firewall Deployment and Segmentation Strategies
Effective deployment and segmentation are critical for maximizing the security benefits of enterprise firewalls; this involves placing firewalls at strategic points—such as between internal networks, at the internet gateway, and within data centers—to create isolated security zones that limit lateral movement in case of a breach. Implementing micro-segmentation further refines access controls by applying policies at the workload or application level, reducing the attack surface and containing potential threats. A well-designed architecture also includes redundant firewall setups for high availability, ensuring uninterrupted protection, and utilizes virtual firewalls in cloud environments to extend security policies consistently across hybrid infrastructures. Regular reviews of segmentation rules help maintain alignment with business needs while minimizing unnecessary exposure.
Access Control and Policy Management
Robust access control and policy management form the foundation of firewall security, requiring organizations to adopt a zero-trust approach where all traffic is denied by default and only permitted through explicitly defined rules based on the principle of least privilege. Policies should be granular, specifying allowed sources, destinations, ports, and protocols, and must be reviewed and updated regularly to remove obsolete rules and adapt to new threats or business changes. Automating policy management—through tools that provide visibility into rule usage and risk—reduces human error and ensures consistency, while role-based access control (RBAC) limits administrative privileges to authorized personnel only, preventing unauthorized modifications.
Monitoring, Logging, and Incident Response
Continuous monitoring and comprehensive logging are essential for detecting and responding to security incidents in real time; enterprise firewalls should be configured to generate detailed logs of all traffic, policy violations, and threat detections, which are then aggregated into a SIEM system for analysis and correlation. Automated alerting mechanisms notify security teams of suspicious activities—such as unauthorized access attempts or anomalies in traffic patterns—enabling swift investigation and response. Integrating firewalls with incident response workflows ensures that detected threats are contained and mitigated promptly, while regular log reviews and audits help identify gaps in policies or coverage, maintaining a proactive security stance.
| Practice | Description | Key Benefit |
|---|---|---|
| Zero-Trust Policy | Deny all traffic by default; allow only explicitly permitted communications | Minimizes attack surface and prevents unauthorized access |
| Regular Firmware Updates | Apply patches and updates to firewall software promptly | Protects against known vulnerabilities and exploits |
| Deep Packet Inspection (DPI) | Analyze packet contents for malicious patterns or anomalies | Enhances threat detection beyond basic filtering |
| Integration with SIEM | Correlate firewall logs with other security data sources | Improves visibility and accelerates incident response |
How do enterprise firewalls contribute to robust network defense strategies?

Enterprise firewalls serve as the foundational component of robust network defense strategies by establishing a secure perimeter that filters incoming and outgoing traffic based on predefined security rules, thus preventing unauthorized access, blocking malicious payloads, and mitigating threats such as DDoS attacks and intrusions; they enforce granular access control policies, segment networks to limit lateral movement, and integrate with other security systems like intrusion detection systems (IDS) and security information and event management (SIEM) platforms to provide comprehensive visibility, real-time monitoring, and coordinated response mechanisms, thereby ensuring the confidentiality, integrity, and availability of critical organizational assets through a layered defense approach that is essential for Enterprise Firewalls for Robust Network Defense.
Traffic Filtering and Access Control
Enterprise firewalls enforce granular traffic filtering and access control by inspecting data packets against a set of security policies to allow or deny transmissions based on parameters such as IP addresses, port numbers, and protocols; this prevents unauthorized users and malicious entities from gaining entry to the network while ensuring that only legitimate, business-critical communications are permitted, thereby reducing the attack surface and maintaining a secure operational environment. For example, they can block traffic from suspicious geolocations or restrict access to non-essential services, enhancing overall network hygiene and compliance with regulatory standards.
Threat Prevention and Intrusion Mitigation
By incorporating advanced threat prevention features such as deep packet inspection (DPI), intrusion prevention systems (IPS), and application-aware filtering, enterprise firewalls identify and neutralize sophisticated threats like malware, ransomware, and zero-day exploits in real time; they analyze traffic patterns to detect anomalies, block known attack signatures, and even employ behavioral analysis to thwart emerging risks, thus serving as a proactive barrier that safeguards sensitive data and infrastructure from compromise. This capability is critical for minimizing the impact of cyber incidents and ensuring business continuity.
| Feature | Function | Benefit |
|---|---|---|
| Deep Packet Inspection (DPI) | Examines data content beyond headers | Detects hidden malware and policy violations |
| Intrusion Prevention System (IPS) | Monitors and blocks suspicious activities | Prevents exploits and unauthorized access |
| Application Control | Manages app-specific traffic | Reduces risks from vulnerable applications |
Network Segmentation and Monitoring
Enterprise firewalls facilitate network segmentation by dividing the network into isolated zones or subnetworks, each with distinct security policies that contain potential breaches and limit lateral movement by attackers; this segmentation ensures that even if one segment is compromised, the damage does not propagate across the entire infrastructure. Additionally, firewalls provide continuous monitoring and logging of all network activities, generating detailed audit trails and alerts that enable security teams to analyze trends, investigate incidents, and refine defense strategies dynamically, thereby enhancing situational awareness and operational resilience.
Which enterprise firewall solutions are utilized by the Department of Defense for robust network defense?

The Department of Defense employs a multi-layered and classified approach to network defense, utilizing a combination of enterprise-grade firewall solutions from leading vendors such as Palo Alto Networks, Cisco Systems, and Fortinet, often integrated within the Joint Regional Security Stacks (JRSS) architecture; these systems are rigorously tested and certified against stringent security requirements like the Department of Defense Information Network (DoDIN) Approved Products List (APL) to ensure they meet standards for advanced threat prevention, deep packet inspection, and segmentation critical for protecting sensitive data and infrastructure across disparate environments, forming a cornerstone of Enterprise Firewalls for Robust Network Defense.
Primary Firewall Vendors and Technologies
The DoD leverages next-generation firewalls from established industry leaders, with Palo Alto Networks platforms being extensively deployed for their advanced threat intelligence and application-aware capabilities, Cisco Firepower solutions providing integrated intrusion prevention and malware defense, and Fortinet FortiGate appliances valued for high-performance throughput and centralized management; these technologies are selected for their ability to enforce granular security policies, support zero-trust architectures, and seamlessly interoperate within the DoD's complex network ecosystems, ensuring comprehensive protection against evolving cyber threats.
| Vendor | Key Product Series | Primary Capability |
|---|---|---|
| Palo Alto Networks | PA-Series | Application-ID & Threat Prevention |
| Cisco Systems | Firepower | Integrated IPS & AMP |
| Fortinet | FortiGate | High-Performance UTM |
Certification and Compliance Requirements
All firewall solutions operational within DoD networks must undergo rigorous evaluation and achieve certification against strict criteria outlined in the DoDIN APL, which validates compliance with security technical implementation guides (STIGs), support for necessary cryptographic standards like Suite B algorithms, and compatibility with mandated network management protocols; this process ensures that every deployed firewall meets the department's uncompromising standards for reliability, security robustness, and interoperability in critical mission environments, forming a foundational element of the infrastructure's defensive posture.
Integration with DoD Network Architectures
Enterprise firewalls are not standalone components but are deeply integrated into overarching DoD network frameworks, primarily the Joint Regional Security Stacks (JRSS), which consolidates security services across multiple agencies to provide standardized, scalable, and centrally managed defense-in-depth; this integration enables unified threat visibility, consistent policy enforcement, and automated response coordination across classified and unclassified networks, significantly enhancing the department's ability to detect, isolate, and mitigate sophisticated cyber attacks in real-time while optimizing operational efficiency and reducing administrative overhead.
More information of interest
What are the key features of an enterprise firewall for robust network defense?
Enterprise firewalls for robust network defense include advanced threat prevention, intrusion detection and prevention systems (IDPS), deep packet inspection, and application-layer filtering. These features help protect against sophisticated cyber threats, enforce security policies, and monitor network traffic in real time to prevent unauthorized access and data breaches.
How do enterprise firewalls differ from standard firewalls?
Enterprise firewalls are designed for large-scale networks and offer higher performance, scalability, and advanced security capabilities compared to standard firewalls. They support complex rule sets, integrate with other security systems, and provide centralized management for comprehensive network defense across multiple locations.
What are the best practices for configuring an enterprise firewall?
Best practices for configuring an enterprise firewall include implementing the principle of least privilege, regularly updating firewall rules and firmware, segmenting the network to limit breach impact, and conducting ongoing security audits and monitoring. Proper configuration ensures optimal protection while minimizing vulnerabilities and performance issues.
How can an enterprise firewall help with regulatory compliance?
An enterprise firewall assists with regulatory compliance by enforcing data protection policies, maintaining detailed audit logs, and ensuring secure transmission of sensitive information. It helps organizations meet requirements for standards like GDPR, HIPAA, or PCI DSS by preventing unauthorized access and providing evidence of security measures.





Deja una respuesta