
Best Firewalls with IDS for Enterprises USA

- Top Enterprise-Grade Firewalls with Integrated IDS for US Organizations
- Comprehensive Guide to the Best Firewalls with IDS for Enterprises USA
- How do integrated intrusion detection systems enhance firewall capabilities in enterprise environments?
- To what extent does Palo Alto Networks incorporate IDS functionality within its next-generation firewall offerings?
- What technical specifications distinguish enterprise-grade firewalls from standard network security solutions?
- Which firewall solutions with integrated IDS capabilities meet the stringent security requirements of U.S. Department of Defense networks?
- More information of interest
Best Firewalls with IDS for Enterprises USA, in today's complex cybersecurity landscape, enterprises require robust defense mechanisms to protect sensitive data and network infrastructure. A critical component of any enterprise security strategy is the implementation of advanced firewalls integrated with Intrusion Detection Systems (IDS).
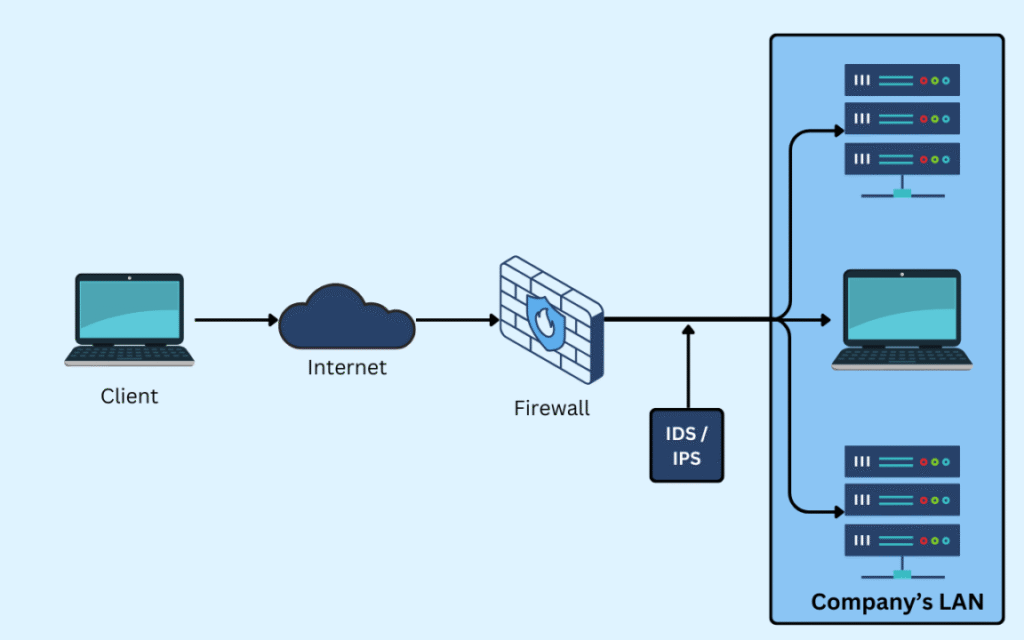
These solutions provide real-time threat monitoring, traffic analysis, and automated responses to potential breaches. For organizations operating in the United States, selecting the right protection involves evaluating performance, scalability, and compliance features. This article explores the top solutions available, focusing specifically on the , to help security leaders make informed decisions for safeguarding their digital assets.
You may also be interested in reading: Windows VPS with High Performance and RDP
Top Enterprise-Grade Firewalls with Integrated IDS for US Organizations
When selecting the Best Firewalls with IDS for Enterprises USA, organizations must prioritize comprehensive threat detection, scalability, compliance capabilities, and seamless integration with existing security infrastructure. These solutions combine traditional perimeter defense with intelligent intrusion detection to identify and mitigate sophisticated threats in real-time, providing layered protection for critical assets and data.
Key Features to Evaluate in Enterprise Firewall-IDS Solutions
Enterprise-grade firewall-IDS combinations should offer deep packet inspection, behavioral analysis, threat intelligence integration, and automated response mechanisms. Advanced solutions provide SSL/TLS decryption, sandboxing for suspicious files, and centralized management consoles. Compliance reporting features are particularly crucial for US enterprises subject to regulations like HIPAA, PCI DSS, and CMMC. The most effective platforms offer customizable security policies that adapt to specific organizational needs while maintaining performance standards.
Leading Vendors in the US Enterprise Market
The market for Best Firewalls with IDS for Enterprises USA is dominated by established cybersecurity providers with proven track records in large-scale deployments. Palo Alto Networks, Cisco, Fortinet, and Check Point consistently rank among top choices due to their comprehensive threat prevention platforms, regular signature updates, and advanced machine learning capabilities. These vendors offer specialized enterprise licensing models, 24/7 support, and dedicated threat research teams that continuously update protection mechanisms against emerging threats.
Performance Considerations for Large-Scale Deployment
Enterprise deployments require firewalls capable of handling multi-gigabit throughput without compromising security effectiveness. Performance metrics must include maximum threat prevention throughput, concurrent connections, and SSL inspection capabilities. Hardware-accelerated options are available for data center environments, while virtual editions suit cloud and hybrid infrastructures. Proper sizing considerations must account for peak traffic loads, encryption overhead, and the computational demands of deep learning algorithms used in modern intrusion detection systems.
Integration with Existing Security Architecture
Successful implementation requires seamless integration with security information and event management (SIEM) systems, endpoint protection platforms, and cloud security services. APIs should support automated workflow orchestration and centralized policy management across distributed environments. Compatibility with existing network infrastructure, including SD-WAN solutions and cloud access security brokers, ensures comprehensive visibility and control. Enterprises should prioritize platforms offering open integration frameworks rather than proprietary ecosystems that limit flexibility.
Cost-Benefit Analysis and ROI Considerations
While enterprise firewall-IDS solutions represent significant investments, their value must be measured through reduced breach risk, compliance cost avoidance, and operational efficiency gains. Total cost of ownership calculations should include hardware/software licensing, maintenance fees, staffing requirements, and training costs. Enterprises should evaluate solutions based on their ability to consolidate security functions, reduce alert fatigue through accurate detection, and minimize business disruption through reliable performance and high availability features.
| Vendor | Product Series | Threat Prevention Throughput | Key Differentiator |
| Palo Alto Networks | PA-Series | Up to 20 Gbps | Advanced WildFire malware analysis |
| Cisco | Firepower 4100 Series | Up to 40 Gbps | Integrated Talos threat intelligence |
| Fortinet | FortiGate 6000 Series | Up to 100 Gbps | Security Fabric integration |
| Check Point | Quantum Security Gateways | Up to 34 Gbps | Zero Trust network access |
Comprehensive Guide to the Best Firewalls with IDS for Enterprises USA
How do integrated intrusion detection systems enhance firewall capabilities in enterprise environments?
Integrated intrusion detection systems (IDS) significantly enhance firewall capabilities in enterprise environments by providing complementary layered security that addresses the limitations of traditional firewalls; while firewalls act as gatekeepers enforcing access policies based on predefined rules, IDS continuously monitors internal and external network traffic for anomalous behavior and known attack patterns, enabling real-time detection of threats such as malware, unauthorized access attempts, or policy violations that may bypass perimeter defenses, and when integrated, these systems allow for automated responses—such as dynamically updating firewall rules to block malicious IP addresses—thereby creating a more adaptive and proactive security posture that improves threat visibility, reduces false positives, and strengthens overall network resilience, which is why selecting the Best Firewalls with IDS for Enterprises USA is critical for robust cybersecurity.
Enhanced Threat Detection Through Behavioral Analysis
Integrated intrusion detection systems enhance firewall capabilities by incorporating behavioral analysis techniques that go beyond the static rule-based filtering of traditional firewalls; firewalls primarily control traffic based on IP addresses, ports, and protocols, but IDS analyzes packet payloads and network behavior to identify suspicious activities—such as unusual data transfers or communication patterns—that may indicate advanced threats like zero-day exploits or insider attacks, allowing organizations to detect and mitigate risks that would otherwise evade conventional firewall defenses, thereby providing a deeper security layer that is essential in complex enterprise networks.
Automated Response and Dynamic Policy Enforcement
By integrating intrusion detection systems with firewalls, enterprises enable automated response mechanisms that dynamically adapt to emerging threats; when an IDS identifies malicious activity—such as a brute-force attack or malware propagation—it can trigger immediate actions, such as instructing the firewall to block the offending IP address or suspend suspicious sessions, which reduces the window of exposure and minimizes manual intervention, thus transforming the firewall from a static barrier into an intelligent, reactive component that continuously refines its security policies based on real-time threat intelligence, significantly enhancing operational efficiency and incident response capabilities.
Comprehensive Visibility and Centralized Management
Integration of IDS with firewalls provides enterprises with unified visibility into network traffic and security events across all layers, consolidating data from perimeter defenses and internal monitoring into a centralized management platform; this holistic view enables security teams to correlate firewall logs with IDS alerts, identify attack patterns, and fine-tune policies for optimal protection, while also simplifying compliance reporting and forensic investigations, making it easier to manage complex environments and ensure consistent enforcement of security standards.
| Feature | Firewall Only | Firewall with Integrated IDS |
|---|---|---|
| Threat Detection Method | Rule-based filtering | Behavioral and signature-based analysis |
| Response to Unknown Threats | Limited | Dynamic and automated |
| Network Visibility | Perimeter-focused | End-to-end monitoring |
| Management Complexity | Moderate | Centralized and streamlined |
To what extent does Palo Alto Networks incorporate IDS functionality within its next-generation firewall offerings?
Palo Alto Networks incorporates intrusion detection system (IDS) functionality extensively within its next-generation firewall (NGFW) offerings through its Threat Prevention subscription service, which integrates deep packet inspection, application-aware signatures, and behavioral analytics to identify and block known and unknown threats in real-time; the IDS capabilities are not merely an add-on but are deeply embedded into the firewall's core processing, leveraging a single-pass architecture to efficiently analyze traffic for vulnerabilities, malware, and exploit attempts without compromising performance, making it one of the Best Firewalls with IDS for Enterprises USA due to its comprehensive threat visibility, automated responses, and continuous updates from the Unit 42 threat intelligence team.
Integration of IDS in Core Architecture
Palo Alto Networks seamlessly integrates IDS functionality into the core architecture of its next-generation firewalls, utilizing a single-pass software engine that processes packets once for all security functions, including intrusion detection, application control, and URL filtering; this design eliminates the performance bottlenecks typically associated with traditional IDS solutions and ensures that threat inspection occurs at line speed without requiring multiple decoding passes, thereby providing enterprises with efficient and scalable security that can handle high-volume network traffic while maintaining low latency and high throughput, which is critical for modern enterprise environments.
Advanced Threat Detection Capabilities
The IDS functionality within Palo Alto Networks' NGFWs employs advanced threat detection capabilities that go beyond signature-based matching to include heuristic analysis, machine learning, and anomaly-based detection for identifying zero-day exploits and sophisticated attacks; these capabilities are powered by regularly updated threat intelligence feeds from Unit 42, which provide real-time information on emerging threats, vulnerabilities, and malicious IPs, enabling the firewall to proactively block intrusions and minimize the attack surface, and this multi-layered approach ensures that enterprises are protected against a wide spectrum of cyber threats, from network-based exploits to application-layer attacks.
| Detection Method | Description | Benefit |
|---|---|---|
| Signature-Based | Matches traffic against known exploit patterns | Blocks known threats effectively |
| Behavioral Analysis | Monitors for deviations from normal traffic patterns | Identifies zero-day and unknown attacks |
| Machine Learning | Uses algorithms to predict and detect malicious activity | Enhances accuracy over time |
Enterprise Deployment and Management
For enterprise deployment, Palo Alto Networks' NGFWs with integrated IDS are designed for centralized management through the Panorama platform, which allows administrators to configure, monitor, and update intrusion detection policies across multiple firewalls from a single interface; this simplifies the complexity of managing security in large-scale environments and ensures consistent policy enforcement, while features like automated threat response and detailed logging provide actionable insights and reduce the mean time to detect and respond (MTTD/MTTR) to incidents, making it an ideal solution for organizations seeking to strengthen their security posture without increasing operational overhead.
What technical specifications distinguish enterprise-grade firewalls from standard network security solutions?
Enterprise-grade firewalls are distinguished from standard network security solutions through several critical technical specifications, including higher throughput capacities, often exceeding 100 Gbps, advanced threat prevention features such as integrated intrusion prevention systems (IPS), deep packet inspection (DPI), and application-aware filtering, support for large-scale rule sets and complex networking environments with features like virtual routing and forwarding (VRF), high availability with active-active or active-passive clustering, and centralized management platforms for unified policy administration across distributed deployments, whereas standard firewalls typically offer basic stateful inspection, limited scalability, and lack advanced security integrations required for large organizations.
Performance and Scalability
Enterprise-grade firewalls are engineered for high performance and scalability, featuring multi-gigabit throughput, low latency, and the ability to handle millions of concurrent connections, which is essential for large networks with heavy traffic loads; they also support modular hardware expansion and virtualized instances for flexible deployment, unlike standard solutions that often struggle with scalability and are limited to smaller network segments. For example, the Best Firewalls with IDS for Enterprises USA typically offer throughput rates starting at 20 Gbps and can scale horizontally to accommodate growth without compromising security efficacy.
Advanced Security Features
These firewalls incorporate advanced security capabilities such as integrated intrusion detection and prevention systems (IDS/IPS), sandboxing for malware analysis, SSL/TLS decryption for encrypted traffic inspection, and application control to enforce policies based on specific apps rather than just ports and protocols; this depth of inspection and threat mitigation goes far beyond the basic packet filtering and stateful inspection provided by standard firewalls, ensuring comprehensive protection against sophisticated attacks. The following table highlights key advanced features:
| Feature | Enterprise-Grade Firewall | Standard Firewall |
|---|---|---|
| IDS/IPS | Integrated, customizable | Basic or absent |
| SSL Inspection | Full decryption support | Limited or none |
| Threat Intelligence | Real-time updates | Manual updates |
Management and Integration
Enterprise firewalls offer centralized management consoles, API support for automation, and seamless integration with security information and event management (SIEM) systems, enabling administrators to enforce consistent policies across distributed environments and respond quickly to incidents; in contrast, standard firewalls usually have standalone, web-based interfaces with minimal automation capabilities, making them unsuitable for large, complex networks requiring coordinated security measures.
Which firewall solutions with integrated IDS capabilities meet the stringent security requirements of U.S. Department of Defense networks?
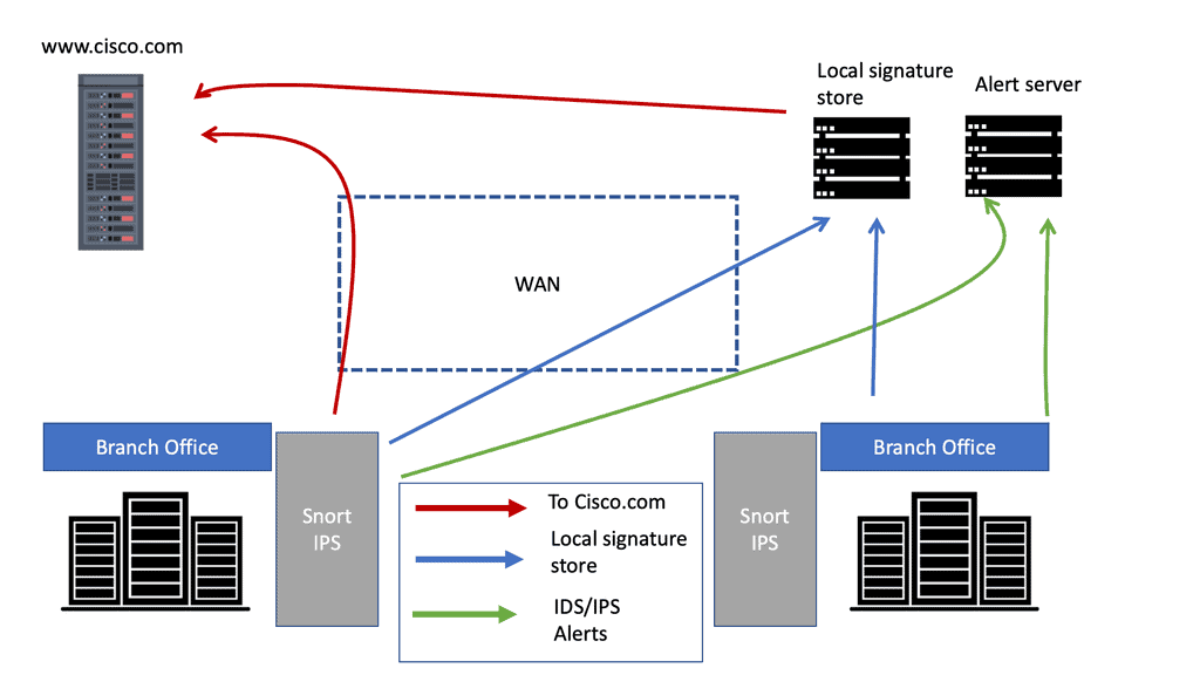
Several firewall solutions with integrated IDS capabilities meet the stringent security requirements of U.S. Department of Defense networks, including Palo Alto Networks Next-Generation Firewalls with Threat Prevention, Cisco Firepower Next-Generation Firewalls with Snort-based IDS, and Fortinet FortiGate utilizing FortiGuard IPS services; these platforms are validated against DoD's Security Technical Implementation Guides (STIGs), support Common Criteria Evaluation Assurance Levels, and often achieve NIAP compliance, making them suitable for environments requiring robust traffic inspection, real-time threat detection, and adherence to DFARS and NIST SP 800-171 controls, thus representing some of the Best Firewalls with IDS for Enterprises USA in high-assurance deployments.
Key Compliance Standards for DoD Firewall Solutions
Firewall solutions intended for U.S. Department of Defense networks must adhere to rigorous compliance standards, including the Security Technical Implementation Guides (STIGs) which provide configuration benchmarks, NIST SP 800-171 for protecting controlled unclassified information, and Common Criteria certifications ensuring evaluated assurance levels; additionally, solutions often need to support FIPS 140-2 validated cryptography and demonstrate compatibility with DoD's Risk Management Framework (RMF) to achieve Authority to Operate (ATO) in classified environments.
Top Vendors and Their Integrated IDS Offerings
Leading vendors providing firewall solutions with integrated IDS capabilities for DoD networks include Palo Alto Networks with its advanced Threat Prevention subscription leveraging machine learning and global intelligence, Cisco Firepower platforms incorporating Snort-based intrusion detection with real-time blacklisting and file trajectory analysis, and Fortinet FortiGate series using AI-powered FortiGuard IPS services with automated threat response; these systems are designed for high-throughput inspection, encrypted traffic analysis, and seamless integration with Security Information and Event Management (SIEM) tools to maintain continuous monitoring as mandated by DoD policies.
| Vendor | Product Series | Key IDS Feature | DoD Compliance Support |
|---|---|---|---|
| Palo Alto Networks | PA-Series NGFW | Threat Prevention with WildFire | STIGs, NIST SP 800-171, FIPS 140-2 |
| Cisco | Firepower NGFW | Snort 3 IPS with Talos Intelligence | Common Criteria, RMF, DFARS |
| Fortinet | FortiGate | FortiGuard IPS with AI Analysis | STIGs, NIAP, USGv6 |
Critical Technical Capabilities and Performance Metrics
To meet DoD requirements, firewall solutions must exhibit critical technical capabilities such as high-availability clustering for failover reliability, multi-gigabit throughput under full threat inspection loads, and deep packet inspection (DPI) for encrypted traffic using TLS 1.2/1.3; performance metrics often include low latency for real-time communications, high connection rates for large-scale networks, and scalable rule sets that can handle complex access control policies without degradation, ensuring operational effectiveness in dynamic and high-threat environments.
More information of interest
What are the top enterprise firewalls with IDS capabilities available in the USA?
Some of the leading enterprise firewalls with integrated Intrusion Detection Systems (IDS) in the USA include Palo Alto Networks Next-Generation Firewalls, Cisco Firepower Threat Defense, Fortinet FortiGate, and Check Point Quantum Security Gateways. These solutions offer advanced threat detection, real-time monitoring, and robust security features tailored for large-scale organizational needs.
How does an IDS enhance enterprise firewall security?
An Intrusion Detection System (IDS) enhances firewall security by monitoring network traffic for suspicious activities and known attack patterns, providing an additional layer of defense. It helps identify potential threats that may bypass traditional firewall rules, enabling quicker incident response and reducing the risk of data breaches or system compromises.
What should enterprises consider when selecting a firewall with IDS?
Enterprises should evaluate scalability, performance under load, compliance with industry standards, ease of integration with existing infrastructure, and the vendor’s support and update policies. Additionally, the effectiveness of the threat intelligence and customizability of security policies are critical factors for ensuring comprehensive protection.
Are there any compliance benefits to using firewalls with IDS in the USA?
Yes, deploying firewalls with IDS capabilities can help enterprises meet regulatory requirements such as HIPAA, PCI DSS, and GDPR by providing detailed logging, real-time alerts, and robust network monitoring. These features assist in demonstrating due diligence in protecting sensitive data and maintaining audit trails.




Deja una respuesta