
Dedicated Hosting for Secure Scalable Sites
- Unlocking Robust Performance: The Power of Dedicated Hosting for Secure Scalable Sites
- Dedicated Hosting for Secure Scalable Sites: A Detailed Guide
- What are the primary limitations of dedicated hosting for secure and scalable websites?
- How does dedicated hosting provide the most secure environment for website deployment?
- Which dedicated hosting solutions are considered optimal for secure and scalable site performance?
- Why is dedicated hosting often regarded as the most secure option for hosting websites?
- More information of interest
Dedicated Hosting for Secure Scalable Sites, in today's digital landscape, businesses require robust infrastructure to ensure both security and performance under growing traffic demands. offers a tailored solution, providing exclusive server resources that eliminate the risks and limitations of shared environments.
This approach guarantees enhanced data protection, full administrative control, and the flexibility to scale resources seamlessly as your online presence expands. Ideal for e-commerce platforms, enterprise applications, and high-traffic websites, dedicated hosting ensures optimal uptime, fortified security protocols, and reliable performance—making it the definitive choice for organizations prioritizing long-term growth and uncompromised safety.
You may also be interested in reading: Best VPNs to Stay Anonymous Online in the USA
Unlocking Robust Performance: The Power of Dedicated Hosting for Secure Scalable Sites
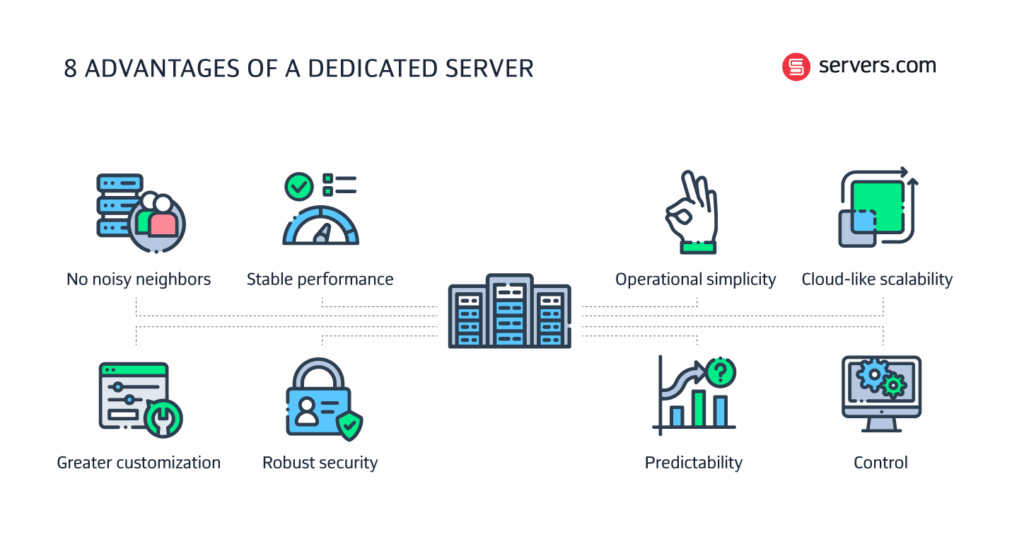
Dedicated hosting provides an exclusive server environment tailored for high-demand applications, offering unparalleled security, performance, and scalability. This solution is ideal for businesses requiring full control over their hosting infrastructure, ensuring optimal uptime and resource allocation. By eliminating the risks associated with shared resources, dedicated hosting forms the foundation for secure, scalable sites that can handle traffic surges and complex operations without compromising stability or data integrity.
Enhanced Security Measures in Dedicated Hosting
Dedicated hosting inherently provides superior security through isolated server resources, eliminating vulnerabilities from neighboring accounts. Administrators can implement custom firewalls, intrusion detection systems, and regular security audits. This controlled environment is essential for maintaining compliance with regulations like GDPR or HIPAA, making it a cornerstone for secure scalable sites handling sensitive data.
Scalability Advantages of Dedicated Servers
Unlike shared or VPS solutions, dedicated hosting allows vertical scaling by upgrading hardware components like CPU, RAM, or storage without migration hassles. This flexibility supports growing traffic and application demands seamlessly, ensuring that sites remain responsive during peak loads. The ability to customize resources on-demand makes it ideal for enterprises planning long-term growth.
Performance Optimization Techniques
Dedicated servers enable fine-tuned performance optimization through exclusive access to resources. Techniques include SSD storage deployment, load balancing configurations, and optimized database management. These measures reduce latency, improve page load speeds, and enhance user experience—critical factors for maintaining competitive secure scalable sites.
Cost-Benefit Analysis of Dedicated Hosting
While dedicated hosting involves higher upfront costs compared to shared alternatives, its long-term benefits justify the investment. Reduced downtime, better security, and scalability lead to lower operational risks and higher ROI. Businesses with steady growth trajectories find the predictable pricing model advantageous for budgeting.
Implementation Best Practices
Successful deployment of dedicated hosting requires careful planning: selecting appropriate hardware specs, configuring backups, and monitoring tools. Partnering with experienced providers ensures smooth migration and ongoing support. Regular maintenance schedules and proactive monitoring are vital for sustaining optimal performance.
| Feature | Shared Hosting | Dedicated Hosting |
| Resource Allocation | Shared among users | Fully isolated |
| Security Control | Limited | Full administrative access |
| Scalability Options | Restricted | Highly flexible |
| Performance Impact | Variable (noisy neighbor risk) | Consistent and reliable |
| Ideal Use Case | Small blogs/static sites | High-traffic secure scalable sites |
Dedicated Hosting for Secure Scalable Sites: A Detailed Guide
What are the primary limitations of dedicated hosting for secure and scalable websites?
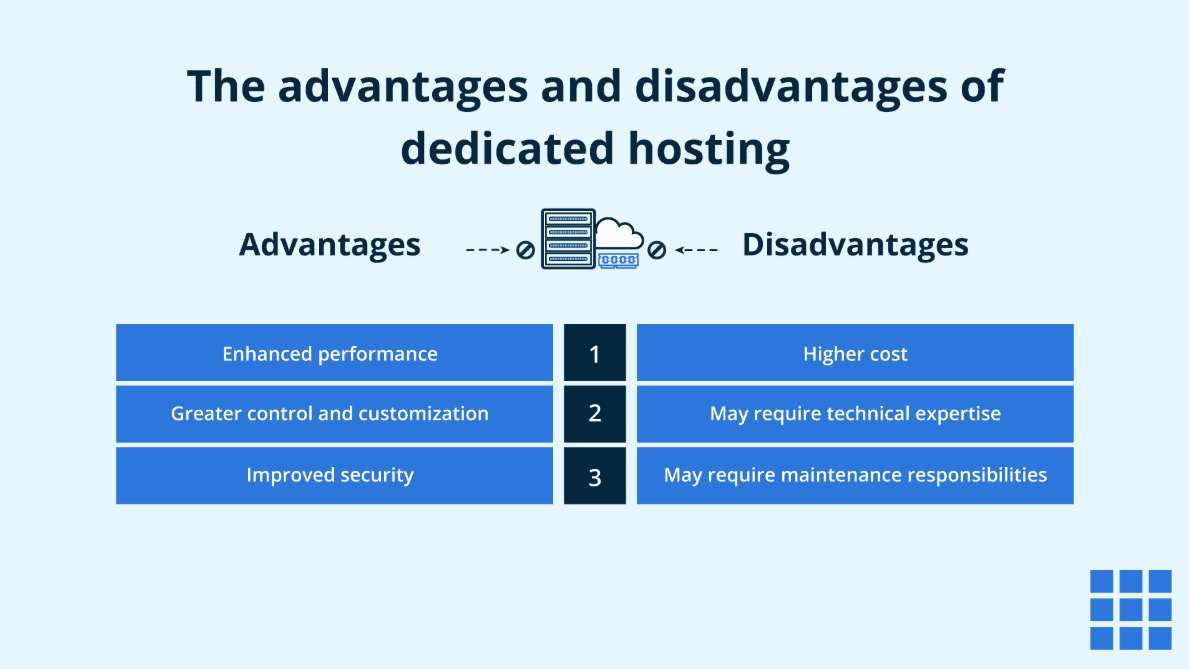
Dedicated Hosting for Secure Scalable Sites faces several primary limitations, including significant financial investment due to high upfront and ongoing costs for hardware, maintenance, and security measures, which can be prohibitive for growing businesses; limited scalability as physical server upgrades require manual intervention, leading to potential downtime and inability to handle sudden traffic spikes seamlessly; and administrative complexity that demands extensive technical expertise to manage security configurations, software updates, and performance optimizations, increasing the risk of human error and security vulnerabilities if not properly addressed.
Financial Constraints and Cost Management
The financial burden of Dedicated Hosting for Secure Scalable Sites is a major limitation, as it involves substantial initial capital expenditure for server hardware and setup, along with ongoing expenses for maintenance, security software licenses, and energy consumption, making it less adaptable for businesses with fluctuating budgets or those in early growth stages where cost-efficiency is critical.
Scalability and Performance Challenges
Scalability is inherently restricted in Dedicated Hosting for Secure Scalable Sites because expanding resources—such as CPU, RAM, or storage—requires physical hardware upgrades or additional servers, leading to downtime during implementation and an inability to automatically accommodate rapid traffic increases, which can compromise website performance and user experience during peak demand periods.
Security and Administrative Overheads
| Aspect | Challenge | Impact |
|---|---|---|
| Security Management | Requires manual configuration of firewalls, patches, and monitoring | Higher risk of vulnerabilities if not expertly managed |
| Administrative Effort | Needs skilled personnel for server administration | Increased operational costs and potential for errors |
| Compliance | Must be handled independently per regulations | Adds complexity and resource allocation |
How does dedicated hosting provide the most secure environment for website deployment?

Dedicated hosting provides the most secure environment for website deployment by ensuring that all server resources—including CPU, RAM, storage, and bandwidth—are exclusively allocated to a single client, eliminating the risks associated with shared environments such as cross-site contamination, unauthorized access from neighboring accounts, or resource-based vulnerabilities; this isolation allows for customizable security configurations, such as tailored firewalls, intrusion detection systems, and strict access controls, while also enabling compliance with industry-specific regulations like HIPAA or PCI DSS, making it an ideal foundation for Dedicated Hosting for Secure Scalable Sites where both protection and performance are paramount.
Exclusive Resource Allocation and Isolation
Dedicated hosting ensures that all server resources are exclusively allocated to a single user, providing complete isolation from other clients, which eliminates common threats found in shared hosting, such as cross-site contamination or resource-based attacks; this isolation allows for fine-tuned control over security measures, including custom firewall rules, dedicated IP addresses, and private network configurations, creating a fortified environment that is inherently more secure and predictable for hosting sensitive data and applications.
Customizable Security Configurations and Control
With dedicated hosting, users have full administrative access to the server, enabling the implementation of bespoke security protocols such as advanced firewalls, malware scanners, and encryption standards tailored to specific needs; this level of control facilitates compliance with stringent regulatory requirements and allows for real-time monitoring and adjustments, ensuring that the security posture can evolve in response to emerging threats without being constrained by the limitations of a shared infrastructure.
| Security Feature | Description | Benefit |
|---|---|---|
| Dedicated IP Address | Exclusive use of an IP not shared with other sites | Prevents blacklisting due to others' activities |
| Custom Firewalls | Configurable software or hardware-based firewalls | Blocks unauthorized access attempts precisely |
| Isolated Environment | No resource sharing with other users | Eliminates neighbor-induced vulnerabilities |
| Root Access | Full administrative control over the server | Enables installation of specialized security tools |
Enhanced Performance and Scalability for Security
Dedicated hosting not only bolsters security but also supports scalable performance by providing guaranteed resources that can handle increased traffic and data processing demands without compromising safety; this ensures that security measures like encryption, logging, and monitoring do not degrade site performance, allowing for seamless scalability while maintaining a robust defense against attacks such as DDoS or brute force attempts, which are more effectively mitigated with dedicated bandwidth and processing power.
Which dedicated hosting solutions are considered optimal for secure and scalable site performance?
For enterprises requiring maximum security and performance scalability, dedicated hosting solutions with hardware-level isolation, customizable security configurations, and high-availability infrastructure are considered optimal, as they provide exclusive resources, advanced DDoS mitigation, integrated firewalls, and scalable storage/bandwidth options that support growth without compromising data integrity or response times, making Dedicated Hosting for Secure Scalable Sites the preferred choice for resource-intensive applications.
Security Features in Dedicated Hosting
Dedicated hosting provides robust security through hardware-level isolation, custom firewall configurations, real-time intrusion detection systems, and automated malware scanning, ensuring that sensitive data remains protected against external threats while maintaining compliance with industry standards such as PCI DSS and GDPR for secure operations.
Scalability Options for Growing Demands
Scalability in dedicated hosting is achieved through flexible resource allocation, on-demand upgrades to CPU, RAM, and storage, and load balancing capabilities that distribute traffic efficiently, allowing businesses to handle increased user activity without performance degradation or service interruptions.
Performance Optimization Techniques
Performance is enhanced via SSD storage solutions, optimized network infrastructure with low-latency connections, and caching mechanisms that accelerate content delivery, ensuring fast load times and reliable uptime for high-traffic websites and applications.
| Component | Impact on Performance |
|---|---|
| SSD Storage | Reduces data access latency and improves read/write speeds |
| High-Bandwidth Networks | Supports large volumes of simultaneous traffic without bottlenecks |
| Multi-Core Processors | Enables efficient handling of complex computations and requests |
Why is dedicated hosting often regarded as the most secure option for hosting websites?
Dedicated hosting is widely considered the most secure web hosting solution because it provides exclusive use of an entire physical server for a single client, eliminating the risks associated with shared environments where multiple users' activities can inadvertently compromise security; this isolation ensures that all resources—including CPU, RAM, and storage—are solely allocated to one entity, preventing cross-contamination from neighboring sites, allowing for customized security configurations such as advanced firewalls, intrusion detection systems, and strict access controls, and enabling compliance with stringent regulatory requirements, making it the ideal foundation for Dedicated Hosting for Secure Scalable Sites where data integrity, performance stability, and proactive threat management are paramount.
Exclusive Resource Allocation and Isolation
Dedicated hosting ensures complete isolation by providing a single tenant with exclusive access to all server resources, which fundamentally enhances security by eliminating the noisy neighbor effect common in shared or virtualized environments; this means that no other users can consume bandwidth, processing power, or memory in a way that might impact your site's performance or expose it to vulnerabilities originating from other accounts, and it allows for fine-tuned resource allocation that supports robust security measures without contention, making it particularly suited for high-traffic or sensitive applications where predictable performance and airtight isolation are non-negotiable for maintaining a secure operational environment.
Customizable Security Configurations
The autonomy afforded by dedicated hosting enables administrators to implement tailored security protocols that are specifically designed to address unique threat profiles and compliance needs; this includes the ability to install and configure specialized firewall rules, intrusion prevention systems, malware scanners, and encryption tools at both the hardware and software levels, as well as to enforce strict access policies such as SSH key authentication and role-based permissions, creating a defense-in-depth strategy that is far more comprehensive and adaptable than the one-size-fits-all solutions typically available in shared hosting plans, thereby significantly reducing the attack surface and enhancing proactive threat mitigation capabilities.
| Security Feature | Description | Benefit |
|---|---|---|
| Hardware Firewall | Dedicated physical firewall device | Filters traffic before it reaches the server |
| Custom IDS/IPS | Tailored intrusion detection/prevention system | Real-time threat blocking and alerts |
| SSL/TLS Encryption | Full control over certificate management | End-to-end data protection |
Enhanced Performance and Reliability
By dedicating an entire server's resources to a single client, this hosting model eliminates performance fluctuations caused by other users' activities, which directly contributes to security by ensuring that critical security processes—such as encryption, logging, and backup operations—run consistently without being starved of resources during peak loads; this reliability also extends to maintaining uptime for security services like DDoS mitigation and continuous monitoring tools, which require stable computational power to function effectively, thereby preventing vulnerabilities that can arise from system slowdowns or failures and supporting a resilient infrastructure that can withstand both operational demands and malicious attacks without degradation in protective capabilities.
More information of interest
What is dedicated hosting and how does it enhance security for websites?
Dedicated hosting provides an entire physical server exclusively for one client, ensuring that no other users share its resources. This isolation significantly enhances security by eliminating risks associated with shared environments, such as cross-site contamination or unauthorized access from neighboring accounts. With full control over the server's configuration, clients can implement tailored security measures, including custom firewalls, intrusion detection systems, and compliance-specific protocols, making it ideal for handling sensitive data and high-traffic applications.
How does dedicated hosting support scalability for growing websites?
Dedicated hosting offers exclusive access to all server resources, such as CPU, RAM, and storage, allowing websites to handle increasing traffic and data demands without performance bottlenecks. Clients can easily scale resources vertically by upgrading hardware components or integrate with cloud services for hybrid scalability. This flexibility ensures that high-traffic sites and applications can grow seamlessly while maintaining optimal speed, reliability, and user experience, even during traffic spikes or expansion phases.
The primary advantages of dedicated hosting include superior performance, enhanced security, and complete administrative control. Unlike shared or VPS hosting, dedicated servers provide exclusive resources that are not affected by other users' activities, ensuring consistent uptime and faster load times. Clients also benefit from customizable configurations, allowing them to optimize the server for specific applications, compliance requirements, or security needs, making it the optimal choice for businesses with high-demand, secure, or scalable web operations.
Can dedicated hosting be customized for specific security or compliance needs?
Yes, dedicated hosting is highly customizable to meet specific security, compliance, or performance requirements. Clients have full root access to install and configure security software, such as advanced firewalls, encryption tools, or monitoring systems, tailored to their needs. This makes it suitable for industries with strict regulatory standards, like healthcare or finance, as servers can be configured to comply with protocols such as HIPAA, PCI DSS, or GDPR, ensuring data protection and legal adherence without compromises.






Deja una respuesta