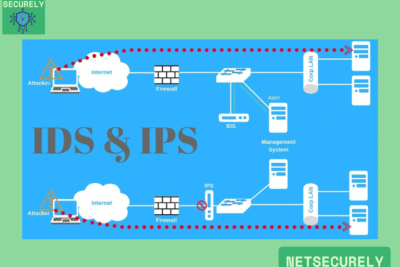
Best Firewalls with IDS for Security in 2025
- Best Firewalls with IDS for Security in 2025: Key Features and Capabilities
- Best Firewalls with IDS for Security in 2025: A Detailed Guide
- More information of interest
- What are the top firewalls with integrated IDS for enterprise security in 2025?
- How do next-generation firewalls with IDS enhance network protection?
- What features should I prioritize when selecting a firewall with IDS for 2025?
- Are there cost-effective firewall with IDS options suitable for small to medium businesses?
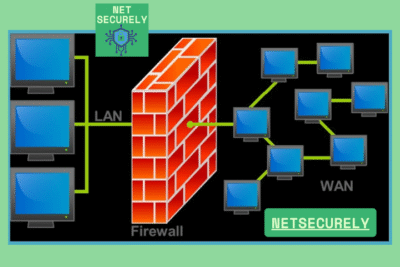
Best Firewalls with IDS for Security in 2025, in an increasingly complex cybersecurity landscape, organizations must prioritize advanced threat detection and prevention mechanisms. The integration of Intrusion Detection Systems (IDS) with next-generation firewalls represents a critical evolution in defending networks against sophisticated attacks. As we approach 2025, selecting the right security infrastructure is paramount for safeguarding digital assets.

This article examines the leading solutions that combine robust firewall capabilities with intelligent IDS features, providing comprehensive protection against emerging threats. Our analysis highlights the top contenders in the market, offering insights into the to help enterprises make informed decisions for their defense strategies.
You may also be interested in reading: Cloud Hosting for Secure Fast Websites 2025
Best Firewalls with IDS for Security in 2025: Key Features and Capabilities
1. Advanced Threat Detection Mechanisms
Modern firewalls integrated with Intrusion Detection Systems (IDS) in 2025 leverage artificial intelligence and machine learning to identify sophisticated threats. These systems analyze network traffic patterns in real-time, detecting anomalies indicative of zero-day attacks, malware, or unauthorized access attempts. Behavioral analysis complements signature-based detection, ensuring comprehensive coverage against evolving cyber threats. Enterprises benefit from reduced false positives and actionable insights, enabling proactive security measures.
2. Performance and Scalability Considerations
When evaluating the Best Firewalls with IDS for Security in 2025, performance metrics such as throughput, latency, and concurrent connection handling are critical. High-end solutions support multi-gigabit speeds without compromising detection accuracy, ideal for data-intensive environments. Scalability features include modular hardware expansions and cloud-native deployments, allowing organizations to adapt to growing network demands seamlessly. Load balancing and clustering options ensure uninterrupted service during peak traffic periods.
3. Integration with Security Ecosystems
Top-tier firewalls with IDS functionality in 2025 emphasize interoperability with broader security frameworks. They integrate seamlessly with Security Information and Event Management (SIEM) systems, endpoint protection platforms, and threat intelligence feeds. APIs and standardized protocols facilitate automated responses, such as isolating compromised devices or blocking malicious IP addresses. This cohesive approach enhances situational awareness and streamlines incident response workflows.
4. Management and Usability Features
User experience is a priority in the Best Firewalls with IDS for Security in 2025, featuring intuitive dashboards and centralized management consoles. Administrators gain granular control over policies, monitoring, and reporting through unified interfaces. Automation capabilities reduce manual intervention, with features like policy optimization suggestions and one-click threat mitigation. Role-based access control ensures secure delegation of responsibilities across IT teams.
5. Compliance and Regulatory Alignment
Firewalls with IDS in 2025 are designed to help organizations meet stringent regulatory requirements, such as GDPR, HIPAA, or PCI-DSS. Built-in compliance templates and audit trails simplify reporting and demonstrate due diligence. Encryption standards and data loss prevention (DLP) integrations protect sensitive information, while detailed logging supports forensic investigations. Regular firmware updates address emerging vulnerabilities and maintain adherence to evolving legal frameworks.
| Vendor | Product Name | Threat Detection Accuracy | Max Throughput | Cloud Integration |
| Vendor A | SecureNet 2025 | 99.8% | 40 Gbps | AWS, Azure, GCP |
| Vendor B | Guardian IDS FW | 99.5% | 35 Gbps | Azure, Oracle Cloud |
| Vendor C | CyberShield Pro | 99.9% | 50 Gbps | AWS, GCP, Private Cloud |
| Vendor D | FortiGate 2025 | 99.7% | 45 Gbps | Multi-Cloud Support |
Best Firewalls with IDS for Security in 2025: A Detailed Guide
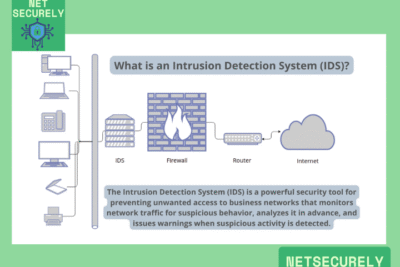
How do modern firewalls incorporate Intrusion Detection System (IDS) capabilities to enhance security measures?
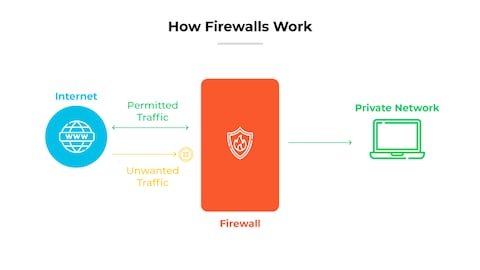
Modern firewalls incorporate Intrusion Detection System (IDS) capabilities by integrating deep packet inspection (DPI), stateful protocol analysis, and signature-based detection mechanisms to monitor network traffic in real-time, allowing them to identify and alert on suspicious activities such as malware, unauthorized access attempts, or anomalous behavior patterns without necessarily blocking traffic outright; this enhances security by providing an additional layer of vigilance that complements the firewall's traditional access control functions, enabling faster incident response and more comprehensive threat visibility across the network infrastructure. When evaluating the Best Firewalls with IDS for Security in 2025, it is essential to consider solutions that offer advanced machine learning algorithms and seamless integration with other security tools for optimal protection.
Integration of Deep Packet Inspection (DPI) in Firewall-IDS Systems
Modern firewalls utilize Deep Packet Inspection (DPI) as a core component of their integrated IDS capabilities, enabling them to analyze the actual content of data packets traversing the network rather than just headers; this allows for the detection of sophisticated threats hidden within encrypted or legitimate traffic, such as malware payloads or command-and-control communications, by comparing packet contents against known attack signatures and behavioral anomalies, thereby significantly enhancing the accuracy and depth of threat identification and providing a more robust defense mechanism against evolving cyber threats.
Signature-Based and Anomaly-Based Detection Methods
Firewalls with integrated IDS employ a combination of signature-based detection, which relies on a database of known threat patterns to identify attacks like viruses or exploits, and anomaly-based detection, which uses machine learning to establish a baseline of normal network behavior and flag deviations that may indicate zero-day attacks or insider threats; this dual approach ensures comprehensive coverage by catching both recognized and novel threats, with the system continuously updating its signatures and adapting its behavioral models to maintain effectiveness against the dynamic threat landscape, making it a critical feature for the Best Firewalls with IDS for Security in 2025.
| Detection Method | Key Function | Advantages |
|---|---|---|
| Signature-Based | Matches traffic against known threat databases | High accuracy for identified threats, low false positives |
| Anomaly-Based | Monitors deviations from normal behavior baselines | Detects zero-day and unknown attacks |
| Hybrid Approach | Combines both methods for comprehensive coverage | Balanced threat detection and adaptability |
Real-Time Alerting and Response Mechanisms
Integrated IDS capabilities in modern firewalls include real-time alerting systems that immediately notify administrators of potential security incidents through dashboards, emails, or SIEM integrations, coupled with automated response actions such as temporarily blocking suspicious IP addresses or terminating malicious sessions to mitigate risks without human intervention; this rapid response minimizes the window of opportunity for attackers and reduces the impact of breaches, ensuring that network integrity is maintained and compliance requirements are met through detailed logging and reporting features.
Which next-generation firewall solutions are considered most effective for comprehensive security in 2025?

Looking toward 2025, the most effective next-generation firewall (NGFW) solutions for comprehensive security are those that integrate advanced threat intelligence, machine learning, and zero-trust architecture to defend against increasingly sophisticated cyber threats. Leading options include Palo Alto Networks' PAN-OS with its AI-driven security operations, Fortinet's FortiGate leveraging high-performance ASICs and deep learning for real-time threat detection, and Check Point's Quantum offering consolidated security with advanced prevention capabilities. These platforms excel in providing granular visibility, automated policy enforcement, and robust protection across cloud, hybrid, and on-premises environments, with a focus on scalability and adaptive security to counter evolving risks like ransomware and supply chain attacks.
Key Features of Top NGFW Solutions for 2025
Leading NGFW solutions in 2025 prioritize integration of AI and behavioral analytics for proactive threat hunting, along with cloud-native support for hybrid infrastructure. They offer centralized management, SSL/TLS decryption, and IoT visibility, ensuring defense against advanced persistent threats and encrypted attacks. These firewalls also emphasize automation for rapid incident response and compliance adherence, making them indispensable for modern security postures. Best Firewalls with IDS for Security in 2025 incorporate these capabilities to provide multi-layered protection.
| Vendor | Key Feature | Use Case |
|---|---|---|
| Palo Alto Networks | AI-powered threat prevention | Enterprise cloud security |
| Fortinet | ASIC-accelerated performance | High-volume network environments |
| Check Point | Consolidated security architecture | Unified threat management |
Integration with Cloud and Zero-Trust Frameworks
Modern NGFWs are designed to seamlessly integrate with cloud platforms like AWS, Azure, and Google Cloud, enabling consistent security policies across distributed environments. They support zero-trust principles through micro-segmentation, identity-based access controls, and continuous verification, reducing the attack surface. This alignment with cloud-native tools and zero-trust frameworks ensures adaptive security that can dynamically respond to threats in real-time, crucial for protecting remote workforces and hybrid infrastructures in 2025.
Threat Intelligence and Automation Capabilities
Top-tier NGFWs leverage global threat intelligence feeds and automated response mechanisms to identify and mitigate emerging threats without human intervention. Features like sandboxing, intrusion prevention systems (IPS), and security orchestration automate the detection of malware, phishing, and zero-day exploits. This proactive approach, powered by machine learning, significantly enhances organizational resilience by minimizing dwell time and accelerating remediation efforts in complex attack scenarios.
What technological advancements define next-generation firewall systems in 2025?
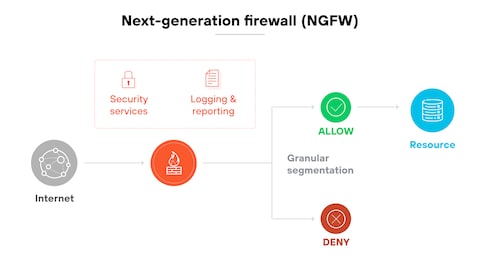
Next-generation firewall systems in 2025 are defined by the integration of artificial intelligence and machine learning for predictive threat analysis and automated response mechanisms, enhanced by behavioral analytics that monitor network traffic patterns to identify anomalies in real time. These systems also incorporate zero-trust architecture principles, ensuring strict identity verification for every user and device attempting to access resources, regardless of their location. Additionally, advancements in encryption technologies and cloud-native designs allow seamless scalability and protection across hybrid environments, while threat intelligence sharing across platforms enables proactive defense against emerging cyber threats, making solutions like the Best Firewalls with IDS for Security in 2025 critical for comprehensive protection.
Integration of Artificial Intelligence and Machine Learning
Artificial intelligence and machine learning are at the core of next-generation firewalls in 2025, enabling these systems to analyze vast amounts of network data in real time to predict and identify potential threats before they manifest. By leveraging advanced algorithms, firewalls can autonomously adapt to new attack vectors, reducing the need for manual intervention and significantly improving response times. This proactive approach enhances the overall security posture, allowing organizations to stay ahead of sophisticated cyber threats. The Best Firewalls with IDS for Security in 2025 utilize these technologies to provide dynamic, intelligent protection that evolves with the threat landscape.
Zero-Trust Architecture Implementation
Zero-trust architecture has become a fundamental component of next-generation firewalls, enforcing strict access controls based on the principle of never trust, always verify. This model requires continuous authentication and authorization for every user, device, and application attempting to connect to the network, regardless of whether they are inside or outside the corporate perimeter. By segmenting networks and applying least-privilege access policies, firewalls minimize the attack surface and prevent lateral movement by threats. The integration of zero-trust principles ensures that security is maintained consistently across all environments, from on-premises to cloud infrastructures.
| Feature | Benefit | Example Technology |
|---|---|---|
| Micro-segmentation | Limits breach impact | Software-defined perimeters |
| Continuous Monitoring | Real-time threat detection | Behavioral analytics engines |
| Identity Verification | Prevents unauthorized access | Multi-factor authentication (MFA) |
Cloud-Native and Scalable Design
Next-generation firewalls in 2025 are designed with cloud-native architectures to provide seamless scalability and flexibility, supporting dynamic workloads across hybrid and multi-cloud environments. These systems utilize containerized deployment and API-driven management to integrate effortlessly with modern DevOps practices and cloud services. Enhanced encryption standards and distributed threat intelligence ensure consistent security policies are enforced regardless of where applications and data reside. This adaptability allows organizations to maintain robust protection while efficiently scaling their infrastructure to meet evolving business needs.
More information of interest
What are the top firewalls with integrated IDS for enterprise security in 2025?
In 2025, the leading firewalls with integrated Intrusion Detection Systems (IDS) include offerings from Palo Alto Networks, Cisco, Fortinet, and Check Point, which combine advanced threat intelligence, machine learning, and real-time monitoring to defend against sophisticated cyber threats.
How do next-generation firewalls with IDS enhance network protection?
Next-generation firewalls with IDS enhance protection by integrating deep packet inspection, behavioral analysis, and automated threat response, allowing organizations to detect and mitigate both known and zero-day attacks more effectively than traditional solutions.
What features should I prioritize when selecting a firewall with IDS for 2025?
Key features to prioritize include AI-driven analytics, seamless integration with cloud environments, scalability for growing networks, and compliance with emerging regulatory standards to ensure robust and future-proof security.
Are there cost-effective firewall with IDS options suitable for small to medium businesses?
Yes, several vendors offer cost-effective solutions tailored for SMBs, such as Sophos, SonicWall, and certain Fortinet models, which provide essential IDS capabilities without compromising on critical security performance.





Deja una respuesta