Best Firewalls with IDS for Threat Detection
- Top Enterprise-Grade Firewalls with Integrated IDS for Advanced Threat Detection
- Best Firewalls with IDS for Threat Detection: A Detailed Guide
- What are the top firewalls with integrated intrusion detection systems for enhanced threat detection?
- Do modern firewalls commonly incorporate intrusion detection capabilities within their architecture?
- Is Palo Alto Networks' threat detection technology classified as an IDS or IPS?
- Which firewall categories are known to integrate intrusion prevention systems for proactive security?
- More information of interest
In today’s rapidly evolving cybersecurity landscape, organizations require robust solutions to defend against sophisticated threats. The integration of Intrusion Detection Systems (IDS) with advanced firewalls has become essential for identifying and mitigating malicious activities in real-time. Evaluating the top solutions in this domain is critical for maintaining a secure network infrastructure.
This article explores the leading options available, providing insights into their features, performance, and deployment capabilities. Our focus is to guide you through the selection of the , ensuring enhanced protection for your digital assets against both known and emerging cyber risks.
You may also be interested in reading: Secure Software Firewalls for PC and Mac 2025
Top Enterprise-Grade Firewalls with Integrated IDS for Advanced Threat Detection
Understanding IDS Integration in Modern Firewall Solutions
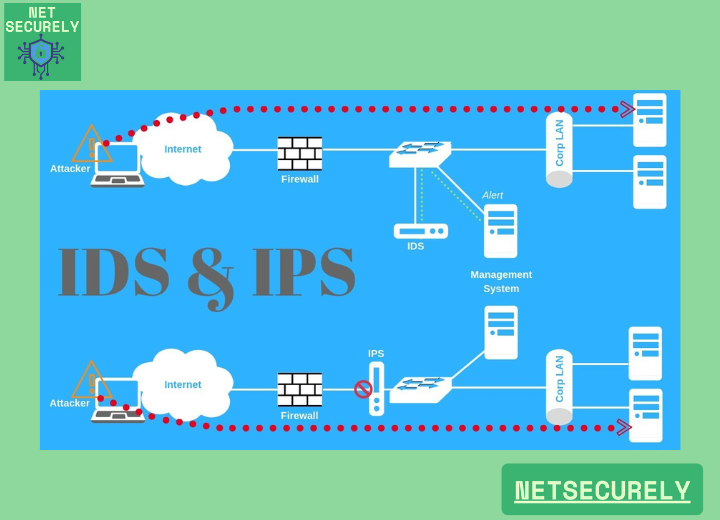
Integrated Intrusion Detection Systems (IDS) have become a critical component of contemporary network security architectures. Modern firewall solutions incorporate deep packet inspection and behavioral analysis capabilities that go beyond traditional port-based blocking. These systems analyze network traffic patterns in real-time, comparing them against known attack signatures and anomalous behavior profiles. The integration of IDS within firewall infrastructure enables organizations to detect sophisticated threats, including zero-day attacks and advanced persistent threats, while maintaining centralized management and streamlined security policies. This convergence significantly enhances the effectiveness of threat detection mechanisms while reducing operational complexity.
Key Features to Evaluate in Firewalls with IDS Capabilities
When selecting among the Best Firewalls with IDS for Threat Detection, several critical features demand careful consideration. Look for solutions offering comprehensive signature-based detection combined with heuristic and behavioral analysis capabilities. Essential features include real-time threat intelligence updates, custom rule creation, SSL/TLS inspection, and low false-positive rates. Additionally, evaluate the system's logging and reporting capabilities, integration with security information and event management (SIEM) systems, and the availability of automated response mechanisms. The most effective solutions provide granular control over inspection policies while maintaining high throughput performance.
Performance Metrics and Deployment Considerations
Deployment of firewalls with integrated IDS requires careful planning around performance requirements and network architecture. Key metrics include maximum throughput with IDS enabled, concurrent connection capacity, and latency impact. Organizations must consider whether to deploy in inline or passive monitoring mode, each offering distinct advantages for different security postures. The table below compares critical performance indicators for leading solutions:
| Firewall Model | Max Throughput (with IDS) | Connections/Second | Latency Impact |
| Palo Alto Networks PA-7000 | 20 Gbps | 350,000 | < 50μs |
| Fortinet FortiGate 6000F | 25 Gbps | 400,000 | < 45μs |
| Cisco Firepower 4100 | 18 Gbps | 300,000 | < 60μs |
| Check Point 6000 Appliance | 22 Gbps | 320,000 | < 55μs |
Industry-Leading Solutions and Their Distinct Capabilities
The market offers several superior options for organizations seeking comprehensive threat protection. Palo Alto Networks delivers exceptional threat prevention through its App-ID technology and WildFire malware analysis. Fortinet's FortiGate series provides integrated security fabric architecture with automated threat response. Cisco's Firepower platform offers advanced malware protection with Talos intelligence integration. Check Point delivers proven threat prevention with over 60 security services unified in a single architecture. Each solution brings unique strengths in handling the evolving landscape of cyber threats while maintaining network performance.
Implementation Best Practices and Ongoing Management
Successful implementation of these security systems requires adherence to established best practices. Begin with comprehensive network assessment and traffic profiling to establish baseline behaviors. Implement gradual deployment using monitoring mode before transitioning to inline prevention. Regularly update threat intelligence feeds and fine-tune detection rules to minimize false positives while maintaining high detection efficacy. Establish clear incident response procedures and ensure security team training covers both firewall management and IDS alert investigation. Continuous monitoring and periodic rule audits are essential for maintaining optimal security posture over time.
Best Firewalls with IDS for Threat Detection: A Detailed Guide
What are the top firewalls with integrated intrusion detection systems for enhanced threat detection?

The top firewalls with integrated intrusion detection systems for enhanced threat detection include Cisco Firepower Next-Generation Firewall, which combines advanced malware protection with network intelligence; Palo Alto Networks Next-Generation Firewall, known for its deep packet inspection and threat prevention capabilities; Fortinet FortiGate, offering high-performance security processing and AI-driven threat detection; Check Point Quantum Security Gateways, providing multi-layered security with real-time threat intelligence; and SonicWall Network Security Firewalls, which deliver comprehensive threat protection with automated response mechanisms. These solutions represent the Best Firewalls with IDS for Threat Detection, integrating signature-based and behavioral analysis to identify and mitigate sophisticated cyber threats across networks.
Key Features of Leading Firewalls with IDS
Leading firewalls with integrated intrusion detection systems offer advanced features such as real-time traffic analysis, deep packet inspection, and automated threat response. These systems utilize a combination of signature-based detection for known threats and anomaly-based detection for zero-day attacks, ensuring comprehensive network protection. Additionally, many include cloud-based management and threat intelligence feeds to stay updated against emerging risks, making them essential for modern cybersecurity infrastructures.
Performance and Scalability Comparison
When evaluating firewalls with IDS, performance metrics like throughput, latency, and concurrent connections are critical. Enterprise-grade solutions are designed to scale seamlessly, supporting everything from small businesses to large data centers without compromising security efficacy. The table below highlights key performance aspects of top products:
| Firewall Model | Throughput (Gbps) | Max Connections | IDS/IPS Enabled |
|---|---|---|---|
| Cisco Firepower | 10-100 | 1-10 million | Yes |
| Palo Alto Networks | 5-50 | 500K-5M | Yes |
| Fortinet FortiGate | 20-100 | 2-12 million | Yes |
| Check Point Quantum | 8-40 | 750K-4M | Yes |
| SonicWall | 2-25 | 500K-2M | Yes |
Deployment and Management Considerations
Effective deployment of firewalls with integrated IDS requires careful planning regarding network architecture, hardware or virtual appliance selection, and integration with existing security tools. Centralized management platforms, such as Cisco Firepower Management Center or Palo Alto Panorama, provide unified control over policies, logging, and incident response. Additionally, automated updates and comprehensive reporting features streamline ongoing maintenance, ensuring optimal performance and compliance with security standards.
Do modern firewalls commonly incorporate intrusion detection capabilities within their architecture?
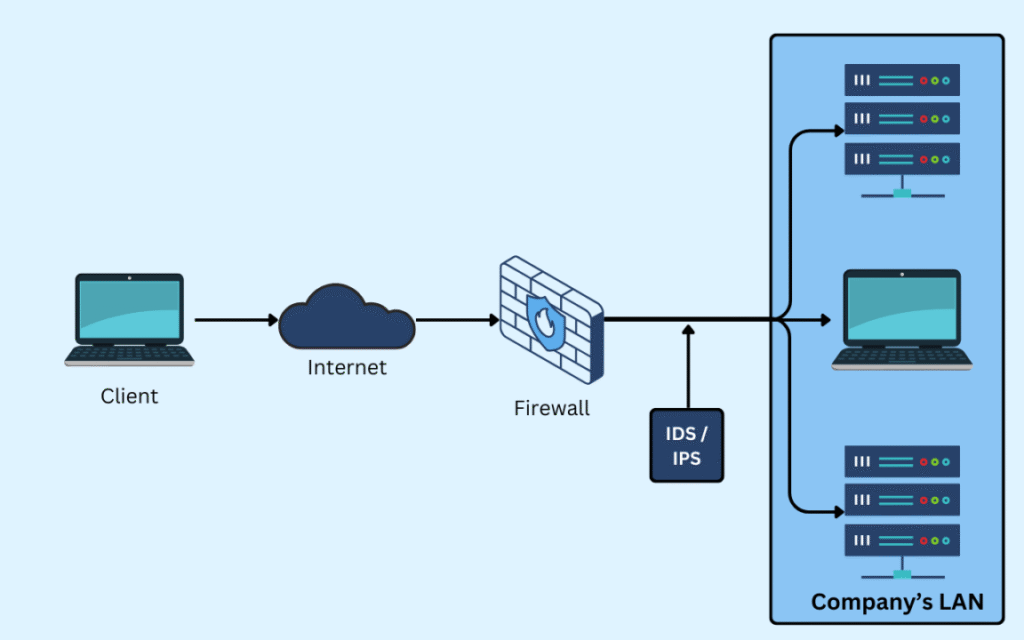
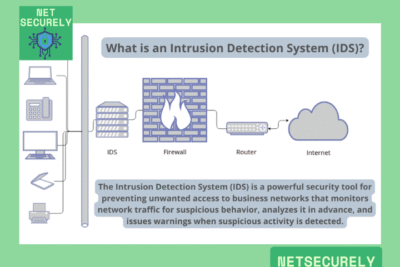
Modern firewalls have evolved beyond simple packet filtering and commonly incorporate intrusion detection capabilities as a core component of their architecture, integrating both signature-based and anomaly-based detection methods to identify malicious activities in network traffic. These systems, often referred to as Next-Generation Firewalls (NGFWs), combine traditional firewall functions with deep packet inspection, real-time traffic analysis, and behavioral monitoring to detect and alert on potential threats, providing a more comprehensive security posture without requiring separate dedicated intrusion detection systems.
Integration Methods in Next-Generation Firewalls
Next-Generation Firewalls integrate intrusion detection through embedded security modules that analyze traffic using a combination of predefined threat signatures and heuristic algorithms. This integration allows for real-time analysis of data packets, examining not just headers but also payload content for malicious patterns, which significantly enhances the ability to detect sophisticated attacks such as zero-day exploits and advanced persistent threats without impacting network performance.
Key Features of Integrated Intrusion Detection
Integrated intrusion detection in modern firewalls includes features such as deep packet inspection (DPI), which scrutinizes the actual data within packets, and behavioral analysis that monitors for deviations from normal network activity. These systems also support automated threat response, such as blocking suspicious IP addresses or terminating connections, and provide detailed logging and reporting for forensic analysis, making them essential for maintaining robust network security.
Comparison of Firewall Solutions with IDS Capabilities
When evaluating firewall solutions, it is important to consider the effectiveness of their integrated intrusion detection systems. Many leading products offer advanced features, but some stand out as the Best Firewalls with IDS for Threat Detection due to their comprehensive coverage, low false positive rates, and seamless integration with other security tools. The following table compares key aspects of top solutions:
| Firewall Product | IDS Detection Methods | Threat Coverage | Performance Impact |
|---|---|---|---|
| Palo Alto Networks NGFW | Signature, Anomaly, Heuristic | High | Low |
| Cisco Firepower | Signature, Behavioral, Reputation | Comprehensive | Moderate |
| FortiGate | Signature, AI-Based, Sandboxing | Extensive | Low to Moderate |
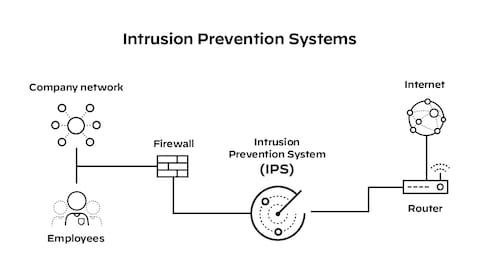
Is Palo Alto Networks' threat detection technology classified as an IDS or IPS?
Z
Palo Alto Networks' threat detection technology is classified as an Intrusion Prevention System (IPS) rather than a pure Intrusion Detection System (IDS), as their Next-Generation Firewalls (NGFWs) not only identify threats in real-time but also actively block malicious traffic through inline deployment, leveraging deep packet inspection, application identification, and threat intelligence to enforce security policies and prevent attacks before they reach the network, making them a proactive defense solution.
Core Functionality of Palo Alto Networks' Threat Detection
Palo Alto Networks' technology integrates deep packet inspection, application awareness, and threat intelligence to analyze network traffic in real-time, enabling it to detect and block a wide range of threats, including malware, exploits, and command-and-control communications, which aligns with IPS capabilities by taking immediate action to prevent breaches rather than merely alerting on them.
Comparison Between IDS and IPS in Palo Alto's Approach
While traditional IDS operates in passive mode to monitor and alert on suspicious activity, Palo Alto's solution functions as an IPS by default, as it is deployed inline and enforces policies to drop or mitigate threats actively; this proactive stance ensures that threats are neutralized before causing harm, distinguishing it from passive IDS systems that lack enforcement mechanisms.
Integration with Next-Generation Firewall Features
Palo Alto Networks embeds its IPS capabilities within its Next-Generation Firewall (NGFW) architecture, combining firewall, VPN, and advanced threat prevention into a single platform; this holistic approach allows for granular control over applications, users, and content, with the IPS component providing critical threat blocking, positioning it among the Best Firewalls with IDS for Threat Detection despite its primary classification as an IPS, as it encompasses detection and prevention synergistically.
| Feature | Description |
|---|---|
| Inline Deployment | Actively blocks threats in real-time |
| Threat Prevention | Uses signatures, behavioral analysis, and machine learning |
| Policy Enforcement | Applies security rules to drop malicious traffic |
Which firewall categories are known to integrate intrusion prevention systems for proactive security?

The firewall categories known to integrate Intrusion Prevention Systems (IPS) for proactive security include next-generation firewalls (NGFWs), unified threat management (UTM) firewalls, and standalone IPS appliances, which often serve as specialized firewalls when deployed inline. NGFWs are particularly prominent in this space, offering deep packet inspection (DPI), application awareness, and threat intelligence feeds to block malicious traffic preemptively. UTM firewalls consolidate multiple security features—such as IPS, antivirus, and content filtering—into a single platform, making them suitable for small to medium-sized businesses seeking comprehensive protection. Additionally, enterprise-grade hardware firewalls and modern cloud firewalls increasingly incorporate IPS capabilities, leveraging machine learning and behavioral analysis to detect and mitigate zero-day threats, ransomware, and advanced persistent threats (APTs) in real time.
Next-Generation Firewalls (NGFWs) with IPS Integration
Next-generation firewalls are designed to provide advanced security by integrating IPS directly into their architecture, enabling real-time traffic analysis and blocking of sophisticated threats. These firewalls utilize deep packet inspection (DPI), application-level controls, and threat intelligence to identify anomalies, malware, and exploit attempts. By combining stateful inspection with IPS, NGFWs offer contextual awareness, allowing policies based on users, applications, and content rather than just ports and IP addresses. This makes them highly effective in environments requiring granular control and proactive defense against emerging threats, such as zero-day attacks and targeted intrusions. Many enterprises deploy NGFWs as part of a defense-in-depth strategy, often prioritizing models recognized as Best Firewalls with IDS for Threat Detection due to their robust feature sets and performance scalability.
Unified Threat Management (UTM) Firewalls and IPS Capabilities
Unified threat management firewalls integrate IPS as a core component alongside other security functions like antivirus, web filtering, and VPN services. Aimed at simplifying security management for small to medium-sized businesses, UTMs provide a consolidated platform that proactively scans and blocks malicious activities without requiring multiple standalone devices. Their IPS features typically include signature-based detection, heuristic analysis, and in some cases, sandboxing for unknown threats. While UTMs may not offer the same depth of customization as dedicated NGFWs or IPS appliances, they strike a balance between comprehensiveness and ease of use, making proactive security accessible to organizations with limited IT resources. The table below summarizes key UTM firewall attributes related to IPS functionality:
| Feature | Description | Benefit |
|---|---|---|
| Integrated IPS | Signature and anomaly-based intrusion prevention | Blocks known and emerging threats in real time |
| Centralized Management | Single console for configuring IPS rules and other security features | Reduces administrative overhead and improves response times |
| Automated Updates | Regular threat definition and pattern updates | Ensures protection against the latest vulnerabilities and attack vectors |
Enterprise Hardware and Cloud Firewalls with IPS
Enterprise-grade hardware firewalls and modern cloud firewalls frequently incorporate IPS to address complex network environments and dynamic workloads. Hardware firewalls, often deployed at network perimeters or data centers, leverage dedicated processing power for high-throughput IPS scanning without compromising performance. They support custom rule sets, threat intelligence integration, and detailed logging for forensic analysis. Cloud firewalls, including firewall-as-a-service (FWaaS) offerings, extend IPS capabilities to distributed infrastructures, virtual networks, and cloud-native applications. These solutions use behavioral analytics and machine learning to adapt to evolving threats, providing scalable proactive security for hybrid and multi-cloud architectures. The emphasis on automation and integration with security orchestration platforms makes these firewalls critical for organizations prioritizing agility and comprehensive threat visibility.
More information of interest
What are the key features to look for in a firewall with IDS for threat detection?
When selecting a firewall with Intrusion Detection System (IDS), prioritize features such as real-time monitoring, deep packet inspection, signature-based detection, and anomaly-based detection. Additionally, ensure it offers customizable rule sets, regular updates for threat intelligence, and seamless integration with your existing security infrastructure for comprehensive protection.
How does an IDS enhance a firewall's threat detection capabilities?
An IDS enhances a firewall's capabilities by providing advanced monitoring and analysis of network traffic for suspicious activities. It uses behavioral analysis and known threat signatures to identify potential intrusions that traditional firewalls might miss, offering an additional layer of proactive defense against evolving cyber threats.
Which firewalls with IDS are recommended for enterprise-level security?
For enterprise-level security, top recommendations include Palo Alto Networks with its advanced threat prevention, Cisco Firepower offering integrated IDS/IPS, Fortinet FortiGate with robust AI-driven detection, and Check Point Quantum providing comprehensive threat defense. These solutions deliver scalable, high-performance protection suitable for large organizations.
Can a firewall with IDS prevent zero-day attacks?
While no solution guarantees complete prevention, a firewall with advanced IDS can significantly mitigate zero-day attacks through anomaly detection and heuristic analysis that identify unusual behavior patterns. Coupled with regular updates and threat intelligence feeds, it improves the chances of detecting and blocking previously unknown threats.



Deja una respuesta