
Best Home Firewalls for IoT Device Security
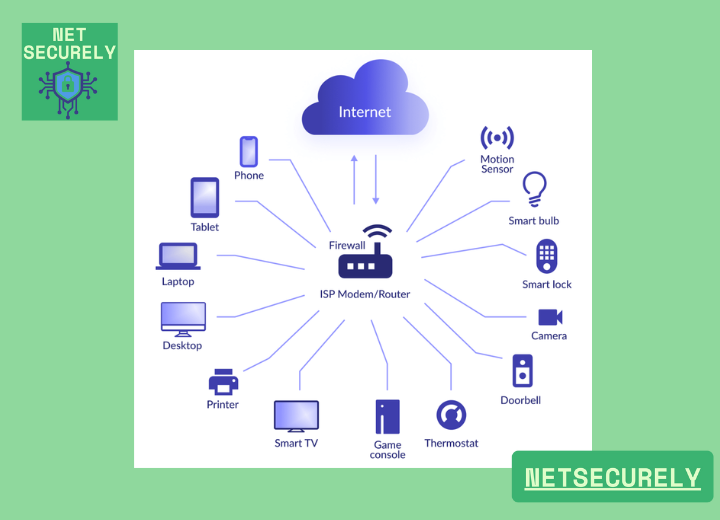
- Securing Your Smart Home: Best Home Firewalls for IoT Device Security
- A Guide to the Best Home Firewalls for IoT Device Security
- How can hardware firewalls enhance security for IoT devices in a home network?
- What are the top-rated home firewalls specifically designed for IoT device protection?
- How does an IoT firewall differ from traditional firewalls in securing connected devices?
- What are the benefits of implementing a dedicated firewall for IoT security in residential settings?
- More information of interest
- What are the key features to look for in a home firewall for IoT security?
- How does a firewall specifically protect IoT devices from cyber threats?
- Can I use a standard router firewall for IoT device security, or do I need a dedicated solution?
- What are some recommended home firewall brands or models for securing IoT networks?
Best Home Firewalls for IoT Device Security, as the proliferation of Internet of Things (IoT) devices continues to grow in modern households, securing these interconnected gadgets has become a paramount concern for homeowners. Vulnerabilities in smart devices can expose personal data and home networks to cyber threats, making robust protection essential.
This article explores the , detailing key features, setup processes, and effectiveness in safeguarding against unauthorized access. By evaluating top solutions, readers will gain insights into selecting the ideal firewall to create a secure and resilient digital environment for their smart home ecosystem.
You may also be interested in reading: Best Software Firewalls for Home and Office
Securing Your Smart Home: Best Home Firewalls for IoT Device Security
Why IoT Devices Require Specialized Firewall Protection
The proliferation of Internet of Things devices introduces unique security challenges that traditional firewalls may not adequately address. IoT devices often have limited computing resources, lack built-in security features, and communicate using various protocols that standard firewalls might not fully inspect. Specialized home firewalls for IoT security provide granular control over device communications, behavior monitoring, and protocol-specific filtering. These solutions typically offer features like device fingerprinting, automated segmentation of IoT networks, and deep packet inspection tailored for IoT traffic patterns, making them essential components in modern home network security architectures focused on Best Home Firewalls for IoT Device Security.
Key Features to Look for in IoT-Specific Firewalls
When evaluating firewalls for IoT protection, several critical features distinguish effective solutions. Advanced threat detection capabilities that can identify anomalous behavior patterns specific to smart devices are paramount. Look for solutions offering automatic device classification, real-time traffic monitoring, and customizable security policies. Additional essential features include regular firmware updates, intrusion prevention systems optimized for IoT protocols, and user-friendly interfaces that allow homeowners to manage security settings without technical expertise. The ability to create isolated network segments for different device categories significantly enhances overall security posture.
Top Recommended Firewall Solutions for Home IoT Networks
Several firewall solutions excel in providing robust protection for home IoT environments. Next-generation firewalls from established vendors offer comprehensive security features specifically designed for smart home ecosystems. Open-source solutions provide customizable options for technically proficient users, while consumer-grade firewall appliances offer plug-and-play simplicity. Each solution varies in its approach to IoT security, with some focusing on behavioral analysis, others emphasizing network segmentation, and several combining multiple protection layers. The optimal choice depends on network complexity, technical requirements, and specific security concerns within the smart home environment.
Implementation and Configuration Best Practices
Proper implementation of IoT firewalls requires careful planning and configuration. Begin by conducting a comprehensive inventory of all connected devices and their communication requirements. Establish separate VLANs for different device categories, such as separating entertainment systems from security cameras and smart assistants. Configure firewall rules to restrict unnecessary outgoing and incoming connections, allowing only essential communications. Regularly update firewall firmware and security definitions, and implement monitoring alerts for suspicious activities. Continuous review and adjustment of security policies ensure ongoing protection as new devices are added to the network.
Monitoring and Maintaining Your IoT Firewall Security
Effective IoT security requires ongoing monitoring and maintenance rather than a set-and-forget approach. Implement regular security audits to review firewall logs and identify potential vulnerabilities. Establish automated alert systems for unusual network activities, such as unexpected data transfers or communication attempts to suspicious external addresses. Regularly update all connected devices' firmware alongside firewall maintenance. Conduct periodic security assessments to evaluate the effectiveness of current protection measures and adjust configurations as new threats emerge. Maintaining detailed documentation of network architecture and security policies supports consistent security management.
| Firewall Feature | Importance Level | Implementation Complexity |
| Device Behavioral Analysis | Critical | Medium |
| Network Segmentation | Essential | Low-Medium |
| Protocol-Specific Filtering | High | High |
| Automatic Updates | Essential | Low |
| User-Friendly Interface | Important | Low |
A Guide to the Best Home Firewalls for IoT Device Security
How can hardware firewalls enhance security for IoT devices in a home network?
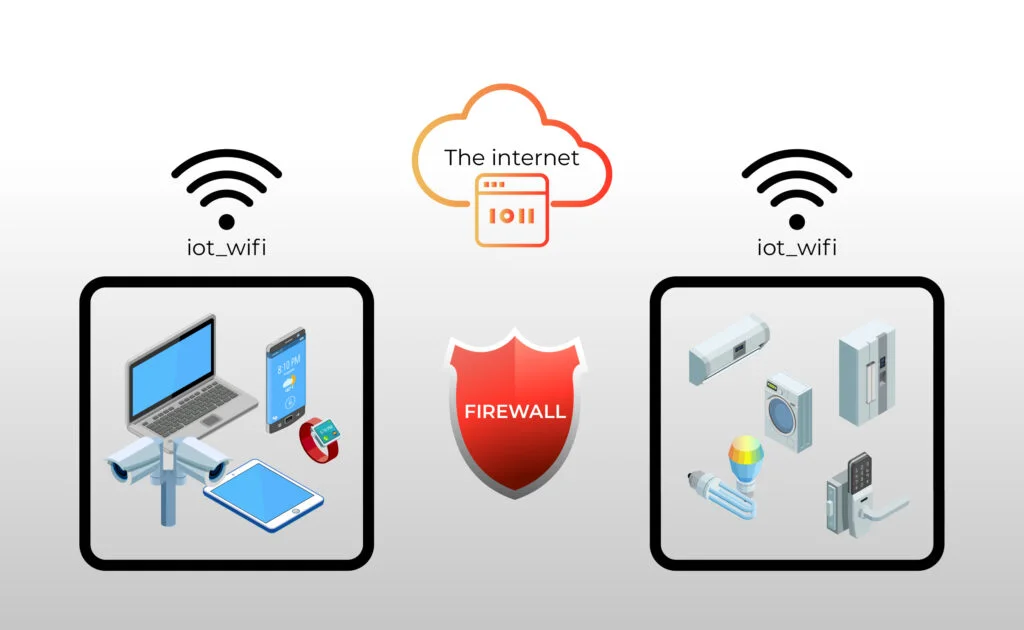
Hardware firewalls enhance security for IoT devices in a home network by acting as a dedicated barrier that monitors and controls all incoming and outgoing traffic based on predetermined security rules, effectively blocking unauthorized access attempts, malware, and suspicious data packets before they reach connected devices; they provide centralized protection, segment network traffic to prevent lateral movement in case of a compromise, and often include features like deep packet inspection, intrusion prevention systems, and customizable access controls that are specifically tailored to identify and mitigate threats targeting IoT vulnerabilities, thereby significantly reducing the attack surface and ensuring that even poorly secured devices do not expose the entire network to risks, with some of the Best Home Firewalls for IoT Device Security offering advanced capabilities such as automated threat response and regular firmware updates to maintain robust defense mechanisms.
Network Segmentation and Access Control
Hardware firewalls enhance IoT security by enforcing network segmentation, which isolates IoT devices from critical systems like computers and smartphones, preventing compromised devices from affecting the entire network; they implement strict access control policies that regulate communication between devices and external servers, blocking unauthorized data exfiltration or command-and-control traffic, and many modern firewalls allow administrators to create dedicated VLANs or zones for IoT equipment, ensuring that even if a device is breached, the damage remains contained and sensitive information remains protected from lateral movement exploits.
Threat Detection and Prevention Capabilities
These firewalls incorporate advanced threat detection mechanisms, such as intrusion prevention systems (IPS) and deep packet inspection (DPI), which analyze traffic in real-time to identify and block malicious activities like denial-of-service attacks, malware propagation, or anomalous behavior patterns common in IoT botnets; by maintaining up-to-date threat intelligence databases and employing heuristic analysis, they can proactively defend against emerging vulnerabilities specific to IoT ecosystems, ensuring that devices with weak built-in security are shielded from exploitation without requiring individual configuration or constant user intervention.
Centralized Management and Monitoring
A key advantage of hardware firewalls is their centralized management interface, which provides a unified dashboard for monitoring all network activity, setting security policies, and reviewing logs related to IoT devices; this allows homeowners to easily track device behavior, receive alerts for suspicious events, and apply consistent security rules across all connected endpoints, simplifying maintenance and ensuring that protection measures are consistently enforced without relying on each device's inherent security features, which are often inadequate or rarely updated by manufacturers.
| Feature | Description | Benefit for IoT Security |
|---|---|---|
| Deep Packet Inspection (DPI) | Examines data packets for malicious content | Blocks hidden threats in IoT device communications |
| Intrusion Prevention System (IPS) | Monitors for and blocks attack patterns | Prevents exploitation of IoT vulnerabilities |
| Access Control Lists (ACLs) | Defines permitted traffic rules | Restricts unnecessary IoT device internet access |
| VLAN Support | Enables network segmentation | Isolates IoT devices from critical network zones |
What are the top-rated home firewalls specifically designed for IoT device protection?

Several high-performing home firewalls tailored for IoT protection include the Firewalla Gold, which offers deep packet inspection and real-time monitoring to segment and safeguard connected devices; the Ubiquiti UniFi Dream Machine Pro, known for its integrated threat management and network segmentation capabilities; the Bitdefender Box, which combines firewall functionality with advanced IoT vulnerability scanning; and the Sophos XG Firewall Home Edition, providing enterprise-grade security features like intrusion prevention and detailed traffic analysis for home use. These solutions excel in detecting anomalous behaviors, blocking unauthorized access, and ensuring that IoT ecosystems remain isolated from critical networks, with the Best Home Firewalls for IoT Device Security emphasizing ease of use alongside robust protective measures.
Key Features to Look for in IoT Firewalls
When selecting a firewall for IoT security, prioritize features such as automatic device profiling to identify and classify connected gadgets, segmentation capabilities to isolate IoT devices from main networks, and real-time threat intelligence that updates to counter emerging vulnerabilities. Advanced options should include intrusion detection systems (IDS), customizable alerting for suspicious activity, and parental controls that help manage device access. These functionalities ensure comprehensive protection by not only blocking external threats but also monitoring internal traffic for unusual patterns, which is critical given the often weak security inherent in many IoT products.
Comparison of Popular IoT Firewall Models
The market offers several models each with distinct strengths: the Firewalla Gold stands out for its user-friendly mobile app and powerful network insights, while the Ubiquiti Dream Machine Pro appeals for its scalability within larger smart home setups. The Bitdefender Box is notable for integrating with Bitdefender’s antivirus ecosystem, providing an added layer of malware protection, and the Sophos XG Home Edition offers professional-grade tools like VPN and web filtering at no cost for personal use. Each model varies in cost, complexity, and specific feature sets, making it essential to match the firewall to your network’s size and security requirements.
| Model | Key IoT Features | Price Range |
|---|---|---|
| Firewalla Gold | Real-time alerts, network segmentation | $400-$500 |
| Ubiquiti Dream Machine Pro | Integrated IDS/IPS, scalability | $300-$400 |
| Bitdefender Box | Vulnerability scans, antivirus integration | $150-$200 |
| Sophos XG Home Edition | Advanced threat prevention, free for home use | $0 (software) |
Implementation Tips for Home IoT Firewall Setup
To effectively deploy a firewall for IoT security, start by creating separate VLANs to segment IoT devices from computers and smartphones, which limits the spread of potential breaches. Ensure that the firewall’s firmware is always updated to protect against the latest threats, and activate features like automatic device blocking for unknown or suspicious entities. Regularly review traffic logs provided by the firewall to spot irregularities, and consider disabling unnecessary ports or services on IoT devices themselves to reduce attack surfaces. Proper configuration, combined with ongoing monitoring, maximizes the defensive strength of your chosen solution.
How does an IoT firewall differ from traditional firewalls in securing connected devices?
An IoT firewall differs fundamentally from traditional firewalls through its specialized focus on the unique vulnerabilities and communication patterns of connected devices, employing protocol-specific filtering for MQTT, CoAP, and Zigbee rather than just IP/port-based rules, implementing behavioral analysis to detect anomalies in device activity rather than relying solely on signature-based detection, and providing granular control over device-to-device communications within the network to prevent lateral movement, whereas traditional firewalls primarily secure network perimeters without understanding IoT device behaviors or specialized protocols.
Protocol-Specific Filtering Capabilities
IoT firewalls employ deep packet inspection tailored to IoT-specific protocols like MQTT, CoAP, and Zigbee, allowing them to analyze and filter traffic based on device behavior and data patterns rather than merely blocking ports or IP addresses, which is particularly crucial for preventing exploits targeting vulnerable IoT communication channels that traditional firewalls might overlook due to their lack of protocol awareness; this specialized approach ensures that only legitimate device communications occur, significantly reducing the attack surface for smart home networks where selecting the Best Home Firewalls for IoT Device Security becomes critical for comprehensive protection.
Behavioral Analysis and Anomaly Detection
Unlike traditional firewalls that rely heavily on static rules and known threat signatures, IoT firewalls utilize machine learning and behavioral analytics to establish baselines of normal device activity, enabling them to detect deviations such as unusual data transmission frequencies or unauthorized command executions, which is essential for identifying zero-day attacks or compromised devices that might otherwise go unnoticed; this dynamic security layer provides proactive defense against emerging threats targeting interconnected ecosystems.
| Feature | IoT Firewall | Traditional Firewall |
|---|---|---|
| Detection Method | Behavioral anomaly monitoring | Signature-based blocking |
| Protocol Support | IoT-specific (MQTT, CoAP) | Standard (TCP/IP, UDP) |
| Threat Coverage | Zero-day & unknown threats | Known threats only |
Granular Device-to-Device Control
IoT firewalls provide micro-segmentation capabilities that allow precise control over communications between individual devices within the local network, preventing lateral movement in case of a breach by enforcing strict policies about which devices can communicate and what commands they can execute, whereas traditional firewalls typically focus on inbound/outbound traffic at the network perimeter without visibility or control over internal device interactions, making them insufficient for containing threats that originate from within the IoT ecosystem itself.
What are the benefits of implementing a dedicated firewall for IoT security in residential settings?
Implementing a dedicated firewall for IoT security in residential settings provides enhanced protection by creating a specialized barrier that monitors and controls all incoming and outgoing network traffic specifically for Internet of Things devices, which are often vulnerable due to weak default security settings and frequent manufacturer vulnerabilities; this approach isolates IoT devices from personal computers and smartphones, preventing lateral movement of threats within the home network, offers customizable security policies to block unauthorized access and malicious communications, and allows for detailed traffic analysis and real-time alerts to detect anomalies, significantly reducing the risk of breaches, data theft, or devices being co-opted into botnets.
Network Segmentation and Isolation
A dedicated firewall enables network segmentation by creating separate zones for IoT devices, preventing compromised gadgets from infecting critical personal devices like laptops or smartphones; this isolation contains threats within the IoT segment, and advanced firewalls can enforce policies that restrict device communication only to authorized services, drastically reducing the attack surface. For example, a smart thermostat would be blocked from accessing any internal device other than its cloud server.
Threat Detection and Real-Time Monitoring
These firewalls provide continuous monitoring and deep packet inspection to analyze IoT traffic patterns, identifying suspicious activities such as unexpected data exfiltration or connections to malicious domains; they generate real-time alerts and can automatically block threats, offering residents proactive defense against zero-day exploits and known vulnerabilities common in many IoT products. When selecting the Best Home Firewalls for IoT Device Security, features like behavioral analysis and automated threat response are critical for maintaining a secure smart home environment.
Customizable Access Control and Policies
Homeowners can implement granular access rules tailored to each IoT device’s needs, such as restricting internet access for devices that only require local network communication or scheduling operational hours to minimize exposure; this reduces the risk of unauthorized remote control and ensures devices operate only as intended, enhancing overall security posture.
| Policy Type | Function | Benefit |
|---|---|---|
| Whitelisting | Allows only approved connections | Blocks unknown or malicious endpoints |
| Geofencing | Restricts access by geographic location | Prevents foreign attacks or unauthorized access |
| Time-Based Rules | Limits device activity to specific hours | Reduces attack window during idle periods |
More information of interest
What are the key features to look for in a home firewall for IoT security?
When selecting a home firewall for IoT security, prioritize features such as deep packet inspection, intrusion prevention systems, and the ability to segment your network. These features help isolate IoT devices, monitor traffic for suspicious activity, and block potential threats before they can compromise your connected devices.
How does a firewall specifically protect IoT devices from cyber threats?
A firewall protects IoT devices by monitoring and controlling incoming and outgoing network traffic based on predetermined security rules. It can identify and block malicious traffic, prevent unauthorized access, and detect anomalies that may indicate a compromise of your IoT ecosystem.
Can I use a standard router firewall for IoT device security, or do I need a dedicated solution?
While standard router firewalls offer basic protection, a dedicated home firewall provides advanced features like application-level filtering and more granular control, which are crucial for securing often-vulnerable IoT devices. For robust security, a dedicated solution is highly recommended.
What are some recommended home firewall brands or models for securing IoT networks?
Some highly regarded options include Ubiquiti UniFi Dream Machine, Firewalla series, and pfSense-based appliances. These models offer strong IoT security features such as real-time alerts, customizable rules, and network segmentation capabilities.




Deja una respuesta