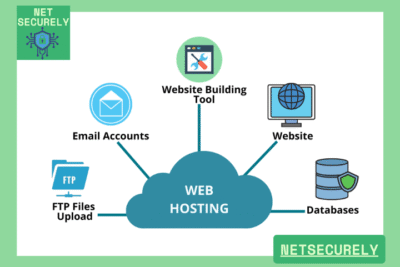
Cloud Hosting for Secure Scalable Solutions


Cloud Hosting for Secure Scalable Solutions, in today’s rapidly evolving digital landscape, businesses require robust and adaptable infrastructure to maintain competitiveness and operational continuity. The demand for reliable, high-performance resources has never been greater, particularly as organizations navigate increasing data volumes and cybersecurity threats.

Adopting represents a strategic approach to addressing these challenges, offering unparalleled flexibility, enhanced protection mechanisms, and the ability to seamlessly adjust to fluctuating workloads. This model not only supports growth but also ensures that critical applications remain accessible and resilient in an interconnected world.
You may also be interested in reading: Top Linux VPS for Custom Server Setups
Ensuring Security and Scalability with Cloud Hosting Solutions
Cloud Hosting for Secure Scalable Solutions provides a robust infrastructure that enables businesses to grow seamlessly while maintaining high levels of data protection. This approach combines advanced security protocols with elastic resource allocation, allowing organizations to adapt to changing demands without compromising on safety or performance. The integration of automated scaling mechanisms ensures that resources are dynamically allocated based on real-time requirements, while comprehensive security measures protect against evolving cyber threats.
Key Security Features in Cloud Hosting
Modern Cloud Hosting for Secure Scalable Solutions incorporates multiple layers of protection including end-to-end encryption, advanced firewalls, and regular security audits. These features work together to create a fortified environment that safeguards sensitive data while maintaining compliance with industry regulations such as GDPR and HIPAA.
Scalability Mechanisms and Performance Optimization
The scalable nature of Cloud Hosting for Secure Scalable Solutions allows businesses to automatically adjust computing resources based on traffic patterns and workload demands. This elastic scalability ensures consistent performance during peak periods while optimizing costs during quieter times through automated resource allocation and load balancing.
Implementation Strategies for Enterprise Deployment
Successful implementation of Cloud Hosting for Secure Scalable Solutions requires careful planning regarding architecture design, migration strategies, and integration with existing systems. Enterprises should consider phased deployment approaches, comprehensive testing protocols, and staff training programs to ensure smooth transition and optimal utilization of cloud capabilities.
Cost Management and Resource Allocation
Cloud Hosting for Secure Scalable Solutions offers flexible pricing models that align operational costs with actual usage. Through detailed monitoring tools and automated scaling policies, organizations can optimize their spending while maintaining required performance levels, ensuring efficient resource utilization across all operational aspects.
Compliance and Regulatory Considerations
Implementing Cloud Hosting for Secure Scalable Solutions requires adherence to various regulatory frameworks depending on industry and geographic location. Providers typically offer compliance certifications and tools that help organizations meet requirements for data protection, privacy standards, and industry-specific regulations.
| Feature Type | Security Aspect | Scalability Benefit |
| Automated Backups | Data protection and recovery | Seamless resource restoration |
| Load Balancing | Distributed threat mitigation | Optimal performance distribution |
| Elastic Computing | Secure resource allocation | Dynamic scaling capability |
| Network Security | Advanced firewall protection | Scalable security infrastructure |
| Monitoring Tools | Real-time threat detection | Performance optimization insights |
Comprehensive Guide to Cloud Hosting for Secure Scalable Solutions
How do cloud hosting services provide scalable infrastructure solutions?
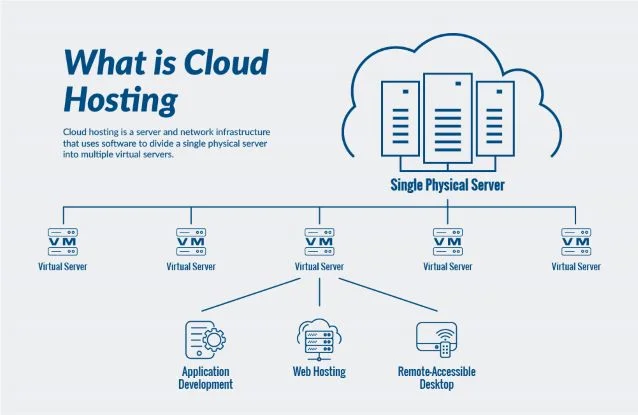
Cloud hosting services provide scalable infrastructure solutions through virtualized resources that can be dynamically allocated based on real-time demand, utilizing a pay-as-you-go model that allows users to instantly scale computing power, storage, and network capabilities without investing in physical hardware; this elasticity is managed via automated orchestration tools and load balancers that distribute traffic efficiently across servers, ensuring optimal performance during traffic spikes while maintaining cost-efficiency during lower demand periods, making Cloud Hosting for Secure Scalable Solutions ideal for businesses with fluctuating needs.
Resource Elasticity and On-Demand Scaling
Cloud hosting enables resource elasticity by allowing instant allocation or deallocation of virtualized compute, storage, and networking components based on real-time requirements; this is achieved through hypervisor technology and APIs that automate scaling processes, ensuring applications can handle traffic surges without manual intervention while minimizing idle resource costs.
Automated Load Balancing and Distribution
Automated load balancers play a critical role in scalable cloud infrastructure by distributing incoming network traffic across multiple servers to prevent overload on any single node, enhancing both performance and fault tolerance; this distribution is managed through algorithms like round-robin or least connections, and often integrates with health checks to reroute traffic from failed instances seamlessly.
| Component | Function | Impact on Scalability |
|---|---|---|
| Virtual Machines (VMs) | Provide isolated compute environments | Enable horizontal scaling by adding/removing instances |
| Object Storage | Offers scalable data storage | Supports unlimited data expansion without hardware limits |
| Auto-Scaling Groups | Automate instance provisioning | Dynamically adjust capacity based on predefined metrics |
Cost-Efficiency and Operational Flexibility
The pay-per-use pricing model inherent in cloud hosting eliminates upfront capital expenditure on physical hardware, allowing organizations to scale resources precisely as needed while only incurring costs for actual consumption; this operational flexibility is bolstered by monitoring tools that provide insights into usage patterns, enabling informed decisions on scaling actions and budget management.
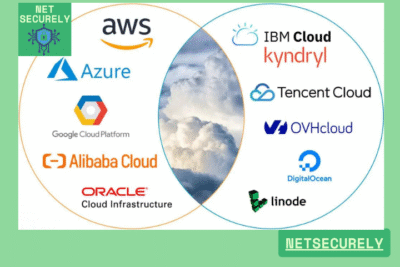
Which cloud hosting providers offer the most secure service options?

Several leading cloud hosting providers offer highly secure service options, with Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) standing out due to their comprehensive security frameworks, including end-to-end encryption, identity and access management (IAM), DDoS protection, and compliance with global standards like ISO 27001, SOC 2, and GDPR, making them ideal for enterprises seeking Cloud Hosting for Secure Scalable Solutions; other notable providers like IBM Cloud and Oracle Cloud also provide robust security features tailored for specific industry needs.
Key Security Features of Top Cloud Providers
The top cloud providers prioritize security through features such as advanced encryption for data at rest and in transit, multi-factor authentication (MFA), and network security tools like virtual private clouds (VPCs) and firewalls; for instance, AWS offers Shield for DDoS mitigation, Azure provides Azure Security Center for threat protection, and GCP includes Security Command Center for visibility and control, ensuring a secure environment for sensitive workloads and compliance with regulations.
| Provider | Key Security Feature | Compliance Certifications |
|---|---|---|
| AWS | AWS Shield (DDoS protection) | ISO 27001, SOC 2, GDPR |
| Microsoft Azure | Azure Security Center | ISO 27001, HIPAA, FedRAMP |
| Google Cloud Platform | Security Command Center | ISO 27001, SOC 3, PCI DSS |
Comparison of Security Compliance Standards
When evaluating cloud hosting providers, it is essential to consider their adherence to international compliance standards, which demonstrate a commitment to security and regulatory requirements; AWS, Azure, and GCP all maintain certifications like ISO 27001 for information security management, SOC 2 for operational controls, and GDPR for data privacy, alongside industry-specific standards such as HIPAA for healthcare and PCI DSS for payment processing, ensuring that organizations can meet legal and contractual obligations without compromising on security.
Specialized Secure Solutions for Enterprises
Enterprises often require specialized secure solutions, and providers like IBM Cloud and Oracle Cloud offer tailored options, such as dedicated hosts for isolated environments, confidential computing for encrypted data processing, and hybrid cloud capabilities for integrating on-premises infrastructure; these features, combined with robust IAM and auditing tools, support complex security needs while enabling Cloud Hosting for Secure Scalable Solutions that adapt to growing business demands.
More information of interest
What is Cloud Hosting and how does it enhance security?
Cloud Hosting is a service that uses virtual servers to host websites and applications across a network of interconnected physical servers, providing scalability and flexibility. It enhances security through advanced encryption, regular security updates, and distributed denial-of-service (DDoS) protection, ensuring data integrity and minimizing vulnerabilities.
How does Cloud Hosting support scalability for growing businesses?
Cloud Hosting supports scalability by allowing businesses to dynamically allocate resources such as storage, bandwidth, and processing power on demand. This elasticity enables seamless handling of traffic spikes and growth without downtime, ensuring optimal performance and cost-efficiency.
What security measures are typically included in Cloud Hosting solutions?
Typical security measures in Cloud Hosting include firewalls, intrusion detection systems, and data encryption both in transit and at rest. Providers also often offer multi-factor authentication (MFA), regular security audits, and compliance with industry standards like ISO 27001 and GDPR.
Can Cloud Hosting ensure data redundancy and disaster recovery?
Yes, Cloud Hosting ensures data redundancy by storing copies of data across multiple geographically dispersed servers, minimizing the risk of data loss. It also supports automated backups and disaster recovery plans, enabling quick restoration of services in case of hardware failure or unforeseen events.




Deja una respuesta