
Enterprise Firewalls for Scalable Protection

- Key Features of Enterprise Firewalls for Scalable Protection
- A Comprehensive Guide to Enterprise Firewalls for Scalable Protection
- What defines an enterprise firewall in the context of scalable network protection?
- Which four primary types of firewalls are most relevant for enterprise scalability?
- How do software firewalls contribute to scalability in enterprise environments?
- Which firewall solution is adopted by the Department of Defense for scalable security operations?
- More information of interest
Enterprise Firewalls for Scalable Protection, in today's rapidly evolving digital landscape, organizations face increasingly sophisticated cyber threats that demand robust security measures. represent a critical component in defending complex network infrastructures against unauthorized access and malicious activities. These advanced solutions are designed not only to provide comprehensive threat detection and prevention but also to adapt seamlessly as businesses grow and their security needs expand.

By integrating intelligent filtering, deep packet inspection, and centralized management capabilities, enterprise firewalls ensure that security scales in tandem with organizational demands, offering resilient defense without compromising performance or operational agility.
You may also be interested in reading: Top Hardware Firewalls for Business in USA
Key Features of Enterprise Firewalls for Scalable Protection
Enterprise Firewalls for Scalable Protection provide critical security measures for large organizations, offering advanced threat detection, centralized management, and seamless integration with existing infrastructure. These solutions are designed to handle high traffic volumes while maintaining performance, ensuring uninterrupted business operations and safeguarding sensitive data across distributed networks.
Core Components of Enterprise Firewalls
Enterprise Firewalls for Scalable Protection consist of multiple integrated components, including stateful inspection engines, intrusion prevention systems (IPS), application control modules, and centralized management consoles. These elements work together to provide comprehensive network security, allowing organizations to enforce granular policies, monitor traffic in real-time, and respond swiftly to emerging threats.
Benefits of Scalable Firewall Solutions
Scalable firewall solutions offer significant advantages, such as the ability to expand security coverage without compromising performance. They support high availability, load balancing, and seamless integration with cloud environments, making them ideal for growing enterprises. Additionally, these firewalls reduce operational costs by streamlining management and automating routine tasks.
Implementation Best Practices
Successful deployment of Enterprise Firewalls for Scalable Protection requires careful planning, including network assessment, policy definition, and phased rollout. Organizations should prioritize redundancy, regular updates, and employee training to maximize effectiveness. It is also essential to align firewall configurations with compliance requirements and business objectives.
Common Challenges and Solutions
Implementing scalable firewalls can present challenges, such as complexity in managing distributed environments or performance bottlenecks during traffic spikes. Solutions include adopting a unified security architecture, leveraging automation for policy enforcement, and conducting periodic audits to optimize configurations and ensure alignment with organizational needs.
Future Trends in Enterprise Firewall Technology
The future of Enterprise Firewalls for Scalable Protection lies in advancements like AI-driven threat detection, zero-trust integration, and enhanced cloud-native capabilities. These innovations will enable more proactive security measures, improved scalability, and greater adaptability to evolving cyber threats.
| Feature | Description | Benefit |
| High Availability | Ensures uninterrupted operation through redundant systems | Minimizes downtime and maintains business continuity |
| Centralized Management | Single console for configuring and monitoring firewall policies | Simplifies administration and improves operational efficiency |
| Threat Intelligence Integration | Leverages real-time data to identify and block emerging threats | Enhances security posture with proactive defense mechanisms |
| Scalable Performance | Supports growing traffic loads without degradation | Ideal for expanding enterprises and dynamic network environments |
| Cloud Compatibility | Seamlessly integrates with public, private, and hybrid clouds | Extends protection to modern IT infrastructures |
A Comprehensive Guide to Enterprise Firewalls for Scalable Protection
What defines an enterprise firewall in the context of scalable network protection?

An enterprise firewall, in the context of scalable network protection, is defined as a comprehensive security solution designed to protect large organizational networks by enforcing granular access control policies, inspecting traffic at multiple layers (including application and user levels), and integrating advanced threat prevention capabilities such as intrusion prevention, deep packet inspection, and real-time threat intelligence; it must be capable of handling high volumes of traffic across distributed environments while maintaining performance, supporting centralized management for consistency, and enabling seamless scalability through modular hardware or cloud-based architectures to adapt to growing network demands and emerging threats without compromising security efficacy.
Core Architectural Components
Enterprise firewalls for scalable protection rely on a robust architecture that includes high-availability clustering, load balancing, and redundant components to ensure uninterrupted operation and fault tolerance. They incorporate dedicated processing units for specific tasks, such as deep packet inspection (DPI) and encryption/decryption, to maintain performance under heavy traffic loads. The architecture often supports modular expansion, allowing organizations to add capacity—such as additional interfaces, storage, or security modules—as network requirements evolve, ensuring that the firewall can scale horizontally or vertically without becoming a bottleneck.
Advanced Security Features
These firewalls integrate a suite of advanced security features essential for defending against sophisticated threats in scalable environments. Key capabilities include intrusion prevention systems (IPS), application-aware filtering, sandboxing for unknown malware analysis, and SSL/TLS decryption to inspect encrypted traffic. They leverage global threat intelligence feeds to dynamically update policies and block emerging attacks, while identity-based access controls ensure that security policies are enforced based on users and groups rather than just IP addresses, enhancing precision and adaptability in large, dynamic networks.
Management and Scalability Considerations
Centralized management is critical for enterprise firewalls in scalable deployments, providing a unified interface to configure, monitor, and enforce policies across distributed firewalls, whether on-premises, in cloud environments, or hybrid setups. This management framework often includes automation tools for policy orchestration, real-time logging, and analytics to streamline operations and reduce administrative overhead. Scalability is achieved through features like virtual system partitioning, which allows a single physical device to operate as multiple independent firewalls, and integration with software-defined networking (SDN) or cloud-native platforms for elastic resource allocation.
| Scalability Feature | Description | Benefit |
|---|---|---|
| High-Availability Clustering | Pairs of firewalls operating in active-active or active-passive mode | Ensures continuous uptime and load distribution |
| Modular Hardware Design | Support for expandable ports, processing cards, and storage | Allows incremental capacity upgrades |
| Cloud Integration | Native support for virtual instances in public/private clouds | Enables elastic scaling and hybrid deployment flexibility |
| Centralized Management Console | Unified platform for policy administration and monitoring | Simplifies control across large, distributed networks |
Which four primary types of firewalls are most relevant for enterprise scalability?
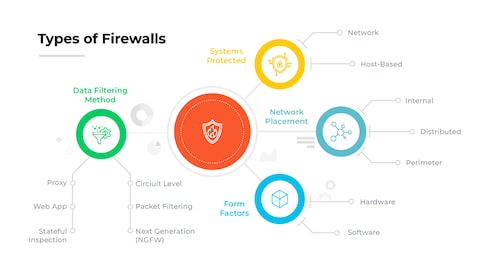
The four primary types of firewalls most relevant for enterprise scalability are packet-filtering firewalls, which inspect packets at the network layer for basic access control; stateful inspection firewalls, which monitor active connections and context for enhanced security; next-generation firewalls (NGFWs), which integrate deep packet inspection, intrusion prevention, and application awareness; and cloud firewalls, which provide scalable, flexible protection for cloud-based and hybrid infrastructures. These Enterprise Firewalls for Scalable Protection ensure robust defense mechanisms capable of adapting to growing network demands, securing diverse traffic types, and supporting complex enterprise architectures without compromising performance or manageability.
Packet-Filtering Firewalls for Enterprise Scalability
Packet-filtering firewalls operate at the network layer by examining individual packets based on predefined rules such as source/destination IP addresses, ports, and protocols, making them efficient for high-traffic environments due to their low resource overhead. While they lack advanced features like deep packet inspection, their simplicity and speed allow enterprises to implement basic access control at scale, particularly for perimeter defense in large networks where processing millions of packets quickly is critical, though they are often supplemented with more advanced firewalls for comprehensive Enterprise Firewalls for Scalable Protection.
Stateful Inspection Firewalls in Scalable Networks
Stateful inspection firewalls enhance security by tracking the state of active connections and evaluating packets based on context, such as whether a packet is part of an established session, which reduces the risk of unauthorized access while maintaining performance. This type of firewall is highly scalable for enterprises because it balances security and efficiency, handling numerous simultaneous connections across expanding networks without significant bottlenecks, making it suitable for dynamic environments where traffic patterns fluctuate and robust session-aware filtering is required.
Next-Generation Firewalls (NGFWs) and Cloud Firewalls for Enterprise Growth
Next-generation firewalls (NGFWs) and cloud firewalls represent the most advanced solutions for scalable enterprises, with NGFWs incorporating features like application-level inspection, intrusion prevention systems (IPS), and threat intelligence, while cloud firewalls offer elastic, on-demand security for cloud and hybrid setups. The following table compares their key scalability attributes:
| Feature | NGFWs | Cloud Firewalls |
|---|---|---|
| Deployment Flexibility | Hardware or virtual appliances | Fully cloud-native |
| Scalability Mechanism | Vertical scaling (upgrading hardware) | Horizontal scaling (auto-scaling resources) |
| Performance Impact | High processing for deep inspection | Low latency, distributed processing |
| Ideal Use Case | Large on-premises networks | Cloud-first or multi-cloud enterprises |
Both types provide Enterprise Firewalls for Scalable Protection by adapting to increasing traffic and complex threats, with NGFWs excelling in traditional infrastructures and cloud firewalls supporting agile, expanding cloud environments.
How do software firewalls contribute to scalability in enterprise environments?
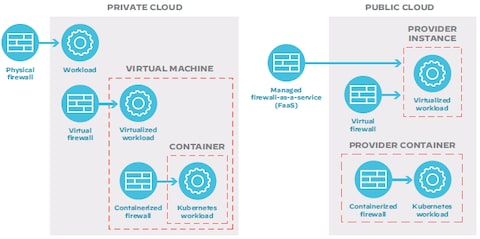
Software firewalls significantly enhance scalability in enterprise environments by offering flexible, software-based deployment that adapts to dynamic infrastructure changes without requiring physical hardware upgrades, allowing organizations to seamlessly extend protection across new virtual machines, cloud instances, or remote networks while maintaining centralized policy management and automated rule enforcement, which reduces operational overhead and supports growth without compromising security integrity, thereby providing Enterprise Firewalls for Scalable Protection that align with evolving business needs.
Centralized Management and Automation
Software firewalls enable centralized management through unified consoles that allow administrators to deploy, update, and enforce security policies across distributed enterprise networks from a single interface, automating tasks such as rule provisioning, threat response, and compliance auditing, which drastically reduces manual effort and ensures consistent protection as the organization scales; this automation is critical for maintaining security posture without proportional increases in administrative overhead, making it a cornerstone of scalable network defense.
Adaptability to Dynamic Infrastructure
In enterprise environments, software firewalls excel at adapting to dynamic infrastructure changes, such as cloud expansion, virtualization, or hybrid network setups, by deploying as lightweight agents or virtual appliances that can be instantly provisioned or scaled down based on demand; this flexibility ensures that security measures keep pace with organizational growth, resource fluctuations, or architectural shifts without the delays or costs associated with physical hardware, thereby supporting seamless scalability while enforcing robust perimeter and internal segmentation policies.
Cost-Efficiency and Resource Optimization
Software firewalls contribute to scalability by optimizing costs and resources, as they eliminate the need for dedicated physical hardware and reduce capital expenditures, instead leveraging existing server infrastructure or cloud platforms; this model allows enterprises to allocate security resources precisely where needed, scale protection on-demand, and avoid over-provisioning, which is especially beneficial for growing organizations with fluctuating traffic patterns or expanding digital footprints.
| Factor | Impact on Scalability |
|---|---|
| Virtualization Support | Enables deployment across unlimited virtual instances |
| Elastic Licensing | Allows pay-as-you-grow models without upfront investment |
| Integration with Cloud Services | Facilitates automatic scaling with cloud workloads |
| Unified Policy Management | Reduces administrative burden as network size increases |
Which firewall solution is adopted by the Department of Defense for scalable security operations?
The Department of Defense (DoD) has adopted the Joint Regional Security Stack (JRSS) as its primary firewall solution for scalable security operations, which integrates multiple enterprise-grade firewalls, intrusion prevention systems, and other security technologies into a unified architecture to provide centralized management, enhanced visibility, and robust threat mitigation across the entire DoD network, ensuring scalable protection for its global operations. This approach leverages Enterprise Firewalls for Scalable Protection to handle massive data flows and sophisticated cyber threats while maintaining compliance with stringent defense security standards.
Core Components of JRSS Architecture
The JRSS architecture incorporates several key components to deliver comprehensive security, including next-generation firewalls (NGFWs), intrusion prevention systems (IPS), enterprise management tools, and virtual routing and forwarding (VRF) capabilities, all integrated into a standardized stack deployed at regional points of presence. This design enables the DoD to consolidate and streamline security functions, reducing complexity and improving operational efficiency while providing consistent policy enforcement and real-time monitoring across diverse network environments. The use of advanced threat intelligence feeds and automated response mechanisms ensures that the system can adapt to emerging threats and scale effectively to protect critical defense infrastructure.
| Component | Function | Example Technology |
|---|---|---|
| Next-Generation Firewall (NGFW) | Provides deep packet inspection, application awareness, and advanced threat prevention | Palo Alto Networks PA-Series |
| Intrusion Prevention System (IPS) | Detects and blocks malicious network activities in real time | Sourcefire (Cisco) |
| Enterprise Management | Centralizes control, policy administration, and logging | VMware NSX, SolarWinds |
Scalability and Performance Features
The JRSS solution is engineered for high scalability and performance, capable of handling the immense data throughput and complex traffic patterns characteristic of DoD networks, which span classified and unclassified systems across global locations. It supports elastic resource allocation, allowing additional capacity to be deployed as needed without compromising security or performance, and incorporates load balancing and failover mechanisms to ensure continuous availability. This scalability is critical for maintaining operational resilience during peak demand or under cyber attack conditions, enabling the DoD to expand its network capabilities while consistently enforcing security policies.
Security and Compliance Standards
JRSS adheres to rigorous security and compliance standards mandated by the DoD, including the Risk Management Framework (RMF), NIST guidelines, and specific directives such as the Defense Information Systems Agency (DISA) Security Technical Implementation Guides (STIGs). The solution undergoes continuous auditing and assessment to ensure it meets requirements for data confidentiality, integrity, and availability, with built-in features for encrypted traffic inspection, access control, and detailed logging to support forensic analysis and regulatory reporting. This compliance-driven approach ensures that the firewall infrastructure not only defends against threats but also aligns with legal and policy obligations essential for national security operations.
More information of interest
What are the primary benefits of an enterprise firewall for scalable protection?
Enterprise firewalls provide centralized security management and granular control over network traffic, enabling organizations to defend against advanced threats while supporting growth. They offer scalable architecture to handle increasing data loads without compromising performance, ensuring consistent protection across expanding networks.
How does an enterprise firewall differ from a standard firewall?
Unlike standard firewalls, enterprise-grade solutions include advanced features such as deep packet inspection, intrusion prevention systems (IPS), and application-aware filtering. They are designed for high availability, seamless integration with other security tools, and management of complex, distributed network environments.
What key features should I look for in a scalable enterprise firewall?
Key features include high throughput capabilities, support for virtualized environments, centralized management consoles, and advanced threat intelligence integration. Additionally, ensure the firewall offers flexible licensing and modular expansion options to adapt to future network demands.
Can enterprise firewalls effectively protect against modern cyber threats?
Yes, modern enterprise firewalls utilize AI-driven analytics, real-time threat updates, and behavioral analysis to detect and mitigate sophisticated attacks like zero-day exploits and ransomware. They provide multi-layered defense strategies essential for safeguarding critical infrastructure in dynamic threat landscapes.






Deja una respuesta