
Firewalls with IDS for Comprehensive Defense
- Integrating Firewalls and IDS for Enhanced Network Protection
- Firewalls with IDS for Comprehensive Defense: A Detailed Guide
- How does the integration of an Intrusion Detection System (IDS) enhance the capabilities of a modern firewall in comprehensive network defense?
- Which firewall solutions are commonly employed by the Department of Defense (DoD) to incorporate Intrusion Detection Systems for robust security measures?
- What types of firewalls are designed to include integrated Intrusion Prevention Systems (IPS) as part of a layered defense strategy?
- How are Intrusion Detection System (IDS) rules configured within a firewall to optimize threat detection and response mechanisms?
- More information of interest
Firewalls with IDS for Comprehensive Defense, in today's complex digital landscape, organizations require advanced security measures to protect their networks from increasingly sophisticated threats. The integration of intrusion detection systems (IDS) with traditional firewalls creates a robust security framework that offers both preventive and detective capabilities.
This approach enables real-time monitoring, threat identification, and immediate response to potential breaches. Implementing provides organizations with layered protection that significantly enhances their security posture. By combining these technologies, businesses can achieve a more proactive defense strategy that addresses both known vulnerabilities and emerging cyber threats effectively.
You may also be interested in reading: Best Enterprise Firewalls with 24/7 Support
Integrating Firewalls and IDS for Enhanced Network Protection
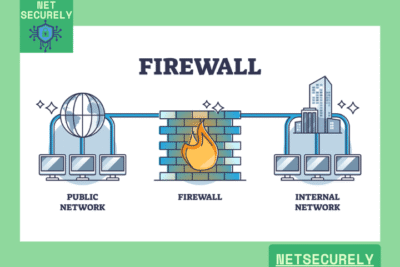
A combined approach using Firewalls with IDS for Comprehensive Defense provides a robust security framework by merging preventative and detective controls. Firewalls act as gatekeepers, enforcing access policies and blocking unauthorized traffic based on predefined rules.
Meanwhile, Intrusion Detection Systems (IDS) monitor network or system activities for malicious actions or policy violations, providing real-time alerts and forensic analysis. This integration ensures that while firewalls prevent known threats, IDS identifies and responds to suspicious behaviors that may bypass initial defenses, creating a layered security posture that addresses both external and internal threats effectively.
Core Components of an Integrated Security System
An integrated system utilizing Firewalls with IDS for Comprehensive Defense consists of several key elements. The firewall component typically includes stateful inspection capabilities, application-layer filtering, and VPN support. The IDS component may be network-based (NIDS) or host-based (HIDS), using signature-based detection, anomaly detection, or heuristic analysis.
These components work in tandem, with the firewall blocking malicious traffic and the IDS providing deeper packet inspection and behavioral analysis. Centralized management consoles often unify configuration, monitoring, and reporting, ensuring cohesive operation and streamlined incident response.
Benefits of Combining Firewall and IDS Technologies
The synergy between firewalls and IDS offers multiple advantages. It enhances threat visibility by correlating firewall logs with IDS alerts, providing a comprehensive view of network activity. This combination reduces false positives through contextual analysis, as firewall data can validate IDS alerts. It also improves response times, as automated systems can trigger firewall rule updates based on IDS findings.
Additionally, it supports regulatory compliance by demonstrating layered security measures and detailed audit trails, making Firewalls with IDS for Comprehensive Defense a strategic choice for organizations seeking to mitigate evolving cyber threats.
Implementation Best Practices
Successful deployment requires careful planning. Start by defining security policies that align with organizational risk tolerance. Position firewalls at network perimeters and between internal segments, while deploying IDS sensors at critical points for optimal traffic monitoring. Ensure both systems are regularly updated with the latest threat intelligence feeds.
Testing and tuning are crucial to minimize false positives and avoid performance bottlenecks. Integration with Security Information and Event Management (SIEM) systems can further enhance correlation and response capabilities, maximizing the effectiveness of Firewalls with IDS for Comprehensive Defense.
Common Challenges and Mitigation Strategies
Implementing an integrated system can present challenges such as complexity in configuration, resource utilization, and alert fatigue. To address these, adopt a phased deployment approach, beginning with critical network segments.
Use hardware or virtual resources that meet performance requirements to prevent network latency. Implement automated alert prioritization and response mechanisms to manage volume. Regular staff training and clear operational procedures ensure that security teams can effectively manage and respond to incidents, maintaining the integrity of the Firewalls with IDS for Comprehensive Defense framework.
Future Trends in Integrated Network Security
The evolution of Firewalls with IDS for Comprehensive Defense is leaning towards greater automation and intelligence. Next-generation firewalls (NGFWs) are increasingly incorporating IDS/IPS functionalities natively, using machine learning to adapt to new threats. Cloud-based and virtualized deployments are becoming standard, offering scalability and flexibility.
Integration with threat intelligence platforms and orchestration tools enables proactive defense measures. As attacks grow more sophisticated, the convergence of these technologies will continue to advance, emphasizing real-time analytics, automated remediation, and enhanced visibility across hybrid environments.
| Component | Primary Function | Key Feature |
| Firewall | Access Control | Stateful Inspection |
| Network IDS (NIDS) | Traffic Monitoring | Signature Detection |
| Host IDS (HIDS) | System Activity Analysis | Anomaly Detection |
| Management Console | Unified Control | Real-time Alerting |
Firewalls with IDS for Comprehensive Defense: A Detailed Guide
How does the integration of an Intrusion Detection System (IDS) enhance the capabilities of a modern firewall in comprehensive network defense?
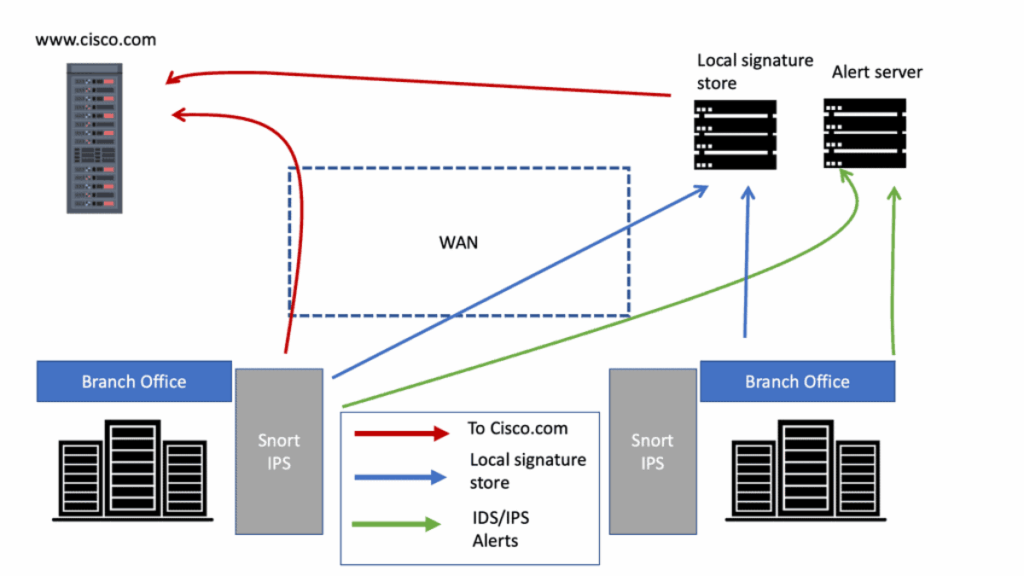
The integration of an Intrusion Detection System (IDS) significantly enhances a modern firewall's capabilities by adding a deep packet inspection and behavioral analysis layer that transcends the firewall's static rule-based filtering, enabling the detection of sophisticated threats like zero-day exploits, polymorphic malware, and anomalous internal traffic patterns that evade conventional perimeter defenses.
This synergy creates a more adaptive security posture where the firewall acts as the gatekeeper enforcing access policies while the IDS serves as the vigilant monitor analyzing traffic for malicious signatures and deviations, thereby forming a foundational element of Firewalls with IDS for Comprehensive Defense that addresses both known and emerging threats across the network landscape.
Complementary Threat Detection Mechanisms
Firewalls primarily operate through predefined rules to allow or block traffic based on protocols, ports, and IP addresses, which is effective for perimeter control but limited against disguised attacks; an IDS complements this by employing signature-based detection to identify known malware patterns and anomaly-based detection to spot deviations from normal network behavior, thus catching threats that bypass firewall rules, such as encrypted attacks or insider threats, ensuring a multi-layered defensive strategy where the firewall blocks obvious threats and the IDS alerts on suspicious activities that require further investigation.
Enhanced Visibility and Real-Time Alerting
Integrating an IDS with a firewall provides granular visibility into network traffic beyond mere connection attempts, analyzing packet contents and flow patterns to identify covert activities like data exfiltration or command-and-control communications; this enables real-time alerts for security teams upon detecting potential intrusions, allowing immediate response actions such as isolating affected systems or updating firewall rules dynamically, which transforms the combined system into an active defense framework rather than a passive barrier, significantly improving incident response times and reducing the window of opportunity for attackers.
Dynamic Policy Enforcement and Adaptive Defense
The combination allows for dynamic policy adjustments where the IDS can inform the firewall to update its rules in response to detected threats, creating an adaptive loop that enhances network resilience; for example, upon identifying a brute-force attack pattern, the IDS can trigger the firewall to temporarily block the source IP, or upon detecting malware communication, it can enforce stricter outbound rules, illustrating how Firewalls with IDS for Comprehensive Defense not only detect but also proactively mitigate risks through automated or manual interventions, ensuring continuous protection alignment with evolving threat landscapes.
| Component | Primary Function | Enhancement from Integration |
|---|---|---|
| Firewall | Access control based on static rules | Gains dynamic rule updates from IDS alerts |
| IDS | Traffic monitoring and threat detection | Leverages firewall to block detected threats in real-time |
| Combined System | Comprehensive network defense | Provides layered protection with proactive mitigation |
Which firewall solutions are commonly employed by the Department of Defense (DoD) to incorporate Intrusion Detection Systems for robust security measures?
The Department of Defense extensively utilizes advanced firewall solutions integrated with Intrusion Detection Systems (IDS) to establish multi-layered security architectures, primarily employing next-generation firewalls (NGFWs) from vendors like Palo Alto Networks, Cisco Systems, and Fortinet that incorporate deep packet inspection, threat intelligence feeds, and automated response capabilities. These systems are often deployed in conjunction with specialized military-grade platforms such as McAfee Sidewinder and Cross Domain Solutions that meet strict compliance requirements like DISA STIGs, creating Firewalls with IDS for Comprehensive Defense through real-time traffic analysis, behavioral analytics, and protocol anomaly detection to protect critical network segments and data classification levels across DoD information networks.
Primary Firewall Vendors and Platforms
The DoD predominantly relies on enterprise-grade firewall solutions from established cybersecurity vendors, with Palo Alto Networks PA-Series and Cisco Firepower Threat Defense (FTD) platforms being extensively deployed due to their integrated IDS/IPS modules and advanced threat prevention capabilities. These systems are configured to operate in high-availability clusters across classified and unclassified networks, implementing stateful inspection and application-aware filtering while maintaining compliance with DoD Directive 8500.01 and NIST SP 800-53 controls. The architecture typically involves:
| Vendor | Platform | Key Capability |
|---|---|---|
| Palo Alto Networks | PA-Series NGFW | WildFire malware analysis |
| Cisco Systems | Firepower FTD | Snort-based IPS |
| Fortinet | FortiGate | Fabric Security Integration |
Integration with Military-Specific Security Frameworks
DoD firewall implementations are rigorously aligned with military cybersecurity frameworks including the Defense Information Systems Agency (DISA) Security Technical Implementation Guides (STIGs) and the Risk Management Framework (RMF). These firewalls with embedded IDS capabilities enforce mandatory access controls and traffic encryption standards consistent with NSA-approved algorithms, while supporting cross-domain guard systems for information transfer between security domains. The configurations are audited against United States Cyber Command (USCYBERCOM) directives and must demonstrate interoperability with DoD's Joint Regional Security Stacks (JRSS) architecture for enterprise-wide threat visibility and coordinated defense.
Advanced Threat Detection and Response Capabilities
Modern DoD firewall-IDS integrations employ machine learning algorithms and signature-based detection engines to identify sophisticated threats, with continuous monitoring through Security Information and Event Management (SIEM) systems like Splunk Enterprise and IBM QRadar.
These solutions perform network behavior analysis to detect zero-day exploits and lateral movement patterns, automatically triggering incident response workflows through SOAR platforms while maintaining forensic data for Cyber Mission Force teams. The systems are tested against real-world attack scenarios through DoD's Cybersecurity Service Provider (CSSP) assessments and Red Team exercises to validate detection efficacy against advanced persistent threats (APTs).
What types of firewalls are designed to include integrated Intrusion Prevention Systems (IPS) as part of a layered defense strategy?
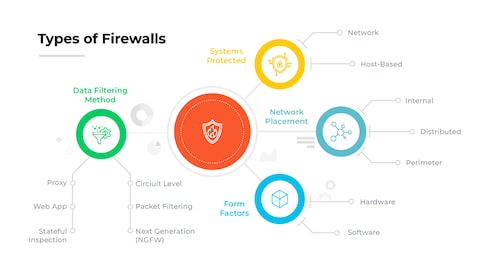
Next-generation firewalls (NGFWs) and unified threat management (UTM) firewalls are designed to include integrated Intrusion Prevention Systems (IPS) as part of a layered defense strategy, providing deep packet inspection, real-time traffic analysis, and automated threat blocking capabilities to protect networks from sophisticated attacks.
These advanced systems combine traditional firewall functionalities with IPS features, enabling proactive security measures that identify and mitigate threats based on behavioral analysis and signature-based detection, thereby enhancing overall network resilience and ensuring a more robust security posture through Firewalls with IDS for Comprehensive Defense.
Next-Generation Firewalls (NGFWs)
Next-Generation Firewalls (NGFWs) integrate Intrusion Prevention Systems (IPS) to deliver advanced security through deep packet inspection, application awareness, and identity-based controls. These firewalls go beyond traditional port and protocol filtering by analyzing traffic at the application layer, enabling them to detect and block sophisticated threats such as malware, ransomware, and zero-day exploits.
By incorporating IPS functionality, NGFWs provide real-time threat prevention, leveraging signature-based and anomaly-based detection methods to ensure comprehensive network protection. This integration allows organizations to enforce granular security policies and maintain visibility into network activities, significantly reducing the attack surface and enhancing overall defense mechanisms.
Unified Threat Management (UTM) Firewalls
Unified Threat Management (UTM) firewalls combine multiple security features, including integrated Intrusion Prevention Systems (IPS), into a single platform to streamline network defense. These firewalls are designed for ease of use and are particularly beneficial for small to medium-sized businesses seeking all-in-one security solutions.
UTM firewalls with IPS capabilities perform real-time traffic monitoring, threat detection, and automated blocking of malicious activities, while also offering additional functionalities such as antivirus, web filtering, and VPN support. This consolidated approach ensures efficient threat management, reduces complexity, and provides a cost-effective layered defense strategy that protects against a wide range of cyber threats.
Comparison of NGFW and UTM Firewalls with IPS
| Feature | NGFW with IPS | UTM with IPS |
|---|---|---|
| Primary Focus | Advanced threat prevention and application control | All-in-one security for streamlined management |
| Target Users | Large enterprises and complex networks | Small to medium-sized businesses |
| Key Capabilities | Deep packet inspection, identity-based policies | Multifunction integration (e.g., antivirus, web filtering) |
| Deployment Complexity | High, requires specialized knowledge | Low, designed for ease of use |
How are Intrusion Detection System (IDS) rules configured within a firewall to optimize threat detection and response mechanisms?

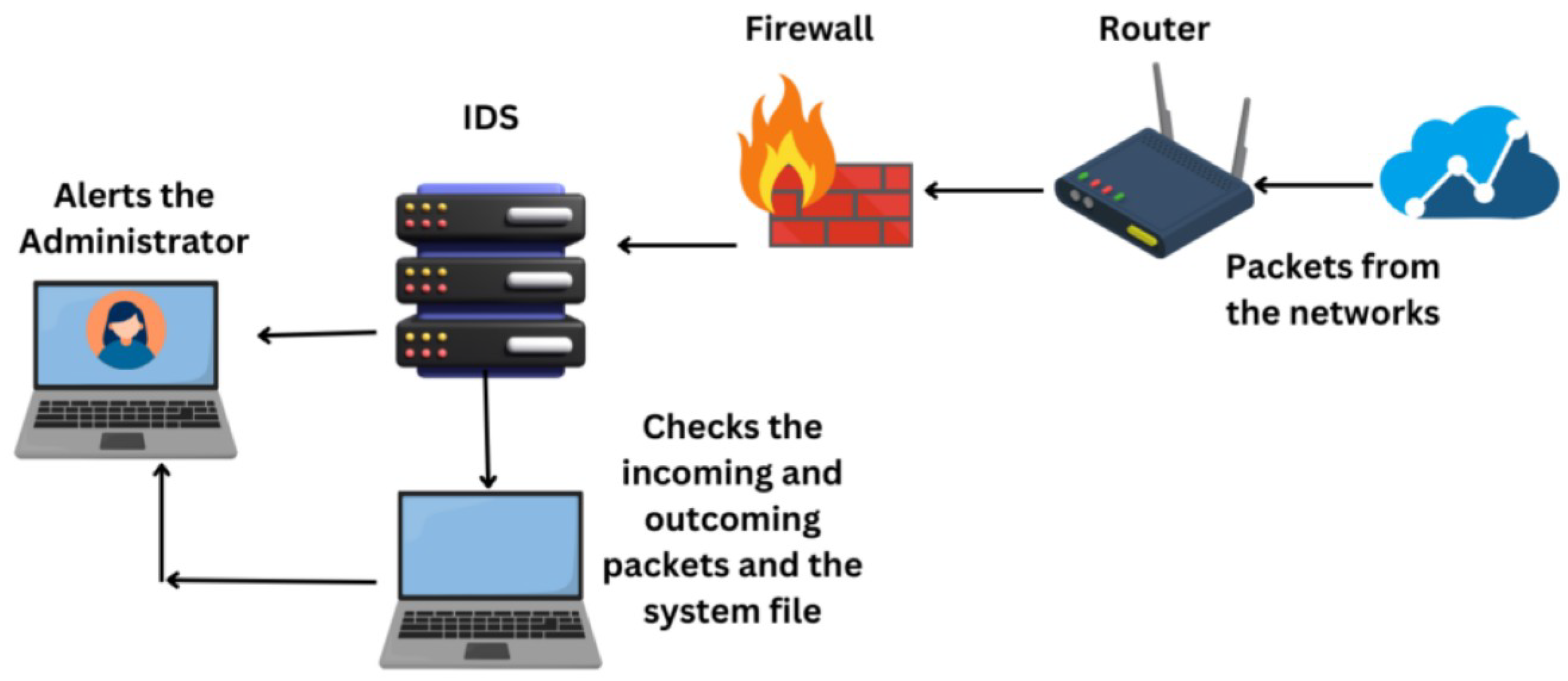
Intrusion Detection System (IDS) rules within a firewall are configured through a meticulous process involving the definition of specific threat signatures, anomalous behavior patterns, and protocol violations, which are fine-tuned based on network topology, traffic baselines, and organizational risk profiles to minimize false positives while maximizing detection accuracy; these rules leverage both signature-based and anomaly-based methodologies, integrated with real-time alerting and automated response actions such as blocking malicious IPs or terminating suspicious sessions, thereby creating a dynamic defense layer that adapts to evolving threats and ensures rapid mitigation, ultimately enhancing the overall security posture through continuous monitoring and iterative optimization of rule sets.
Signature-Based Rule Configuration
Signature-based IDS rules are configured by defining precise patterns or signatures of known threats, such as malware payloads, exploit code, or malicious command sequences, which are cross-referenced against incoming and outgoing traffic in real-time; these rules are often sourced from threat intelligence feeds, vendor databases, or custom analyses, and are prioritized based on severity scores like CVSS to ensure critical vulnerabilities are detected first, with tuning performed to reduce false positives by excluding benign traffic that may trigger similar patterns, thereby enabling efficient and accurate identification of established attacks while maintaining low latency in processing.
| Configuration Aspect | Description | Optimization Technique |
|---|---|---|
| Signature Sources | Derived from threat feeds, CVE databases, or custom rules | Regular updates and filtering for relevance |
| Priority Assignment | Based on CVSS scores or organizational risk | High-severity rules placed at the top of processing order |
| False Positive Mitigation | Exclusions for legitimate traffic patterns | Continuous logging and rule adjustment |
Anomaly-Based Rule Configuration
Anomaly-based IDS rules are configured by establishing baselines of normal network behavior, such as typical traffic volume, protocol usage, or connection rates, and then defining thresholds for deviations that indicate potential threats, such as DDoS attacks, data exfiltration, or unauthorized access attempts; these rules utilize machine learning or statistical models to adapt to changing network conditions over time, with configuration involving careful calibration of sensitivity levels to balance detection rates against false alarms, and are particularly effective for identifying zero-day exploits or sophisticated attacks that lack predefined signatures, thus providing a proactive layer of defense.
| Configuration Aspect | Description | Optimization Technique |
|---|---|---|
| Baseline Establishment | Historical traffic analysis over a defined period | Dynamic updating to reflect network changes |
| Threshold Setting | Defining deviation limits for alerts | Incremental tuning based on alert feedback |
| Adaptive Learning | Machine learning integration for pattern recognition | Regular model retraining with new data |
Integration with Response Mechanisms
IDS rules are integrated with response mechanisms by configuring automated actions triggered upon rule matches, such as blocking IP addresses, dropping packets, resetting connections, or generating alerts to security teams via SIEM systems; this integration requires precise rule-to-action mapping where high-confidence detections enforce immediate mitigations while less certain alerts undergo manual review, ensuring that response times are minimized without compromising operational continuity, and this synergy between detection and action is fundamental to Firewalls with IDS for Comprehensive Defense, enabling real-time threat neutralization and reducing the attacker's window of opportunity.
| Configuration Aspect | Description | Optimization Technique |
|---|---|---|
| Action Types | Block, alert, log, or quarantine responses | Rule-specific actions based on confidence levels |
| Alert Escalation | Integration with SIEM or SOAR platforms | Prioritized alerting for critical events |
| Automation Policies | Predefined workflows for common threats | Testing in isolated environments before deployment |
More information of interest
What is the difference between a firewall and an intrusion detection system (IDS)?
A firewall is a network security device that monitors and controls incoming and outgoing network traffic based on predetermined security rules, acting as a barrier between trusted and untrusted networks. In contrast, an intrusion detection system (IDS) monitors network traffic for suspicious activity and known threats, alerting administrators when potential security breaches are detected. While firewalls focus on preventing unauthorized access, IDS focuses on identifying and reporting potential intrusions.
How do firewalls with integrated IDS enhance network security?
Firewalls with integrated IDS provide a layered defense strategy by combining prevention and detection capabilities. The firewall component blocks unauthorized access and filters traffic based on rules, while the IDS analyzes traffic patterns for anomalies or known attack signatures. This integration allows for real-time threat response, reducing the window of opportunity for attackers and improving overall network resilience.
What types of threats can a firewall with IDS protect against?
A firewall with IDS can protect against a wide range of threats, including malware, denial-of-service (DoS) attacks, unauthorized access attempts, and network reconnaissance activities. The system identifies suspicious patterns, such as unusual data packets or traffic spikes, and can block or alert on activities that deviate from normal behavior, providing comprehensive defense against both known and emerging threats.
Are there any limitations to using a firewall with IDS for network protection?
While effective, firewalls with IDS have limitations, such as potential false positives and false negatives, which can either overwhelm administrators with alerts or miss sophisticated attacks. Additionally, these systems may struggle with encrypted traffic analysis and require regular updates to threat signatures to remain effective. Proper configuration and ongoing monitoring are essential to maximize their protective capabilities.





Deja una respuesta