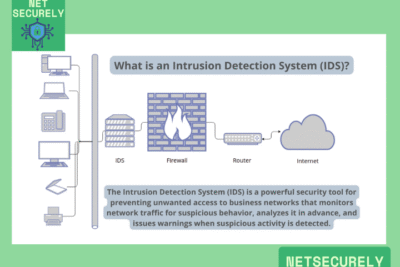
Firewalls with IDS for Malware Protection

- Next-Generation Firewalls with IDS for Malware Protection 2025
- Guide to Implementing Firewalls with IDS for Malware Protection 2025
- How do modern firewalls integrate IDS capabilities for enhanced network security in 2025?
- What criteria determine the effectiveness of an intrusion prevention system within firewalls for 2025 malware threats?
- Which next-generation firewall features are considered most critical for malware protection in 2025?
- To what extent can contemporary firewalls with integrated IDS mitigate malware risks in 2025?
- More information of interest
- What is the difference between a traditional firewall and a next-generation firewall with IDS for malware protection in 2025?
- How does an IDS enhance malware protection in modern firewalls?
- What are the key features to look for in a firewall with IDS for malware protection in 2025?
- Can a firewall with IDS completely prevent all malware infections?
As cyber threats evolve in complexity and scale, organizations face unprecedented challenges in securing their digital assets. By 2025, the integration of advanced intrusion detection systems (IDS) with next-generation firewalls represents a critical frontier in cybersecurity.

These unified solutions offer real-time threat analysis, behavioral monitoring, and automated responses to sophisticated malware attacks. The strategic deployment of will be essential for proactive defense, enabling enterprises to mitigate risks, ensure regulatory compliance, and safeguard sensitive data against emerging threats in an increasingly interconnected digital landscape.
You may be interested in reading: Top Shared Hosting for Reliable Performance
Next-Generation Firewalls with IDS for Malware Protection 2025
Next-generation firewalls (NGFWs) with integrated Intrusion Detection Systems (IDS) represent the forefront of cybersecurity technology for 2025. These advanced security solutions combine traditional firewall capabilities with sophisticated malware detection mechanisms, providing comprehensive protection against evolving cyber threats.
The integration of artificial intelligence and machine learning algorithms enables real-time threat analysis and proactive defense strategies, making Firewalls with IDS for Malware Protection 2025 essential for organizations seeking robust security postures in an increasingly complex digital landscape.
Advanced Threat Detection Capabilities
Modern Firewalls with IDS for Malware Protection 2025 incorporate deep packet inspection and behavioral analysis to identify zero-day attacks and sophisticated malware. These systems utilize signature-based detection alongside anomaly-based monitoring, enabling identification of both known threats and previously unseen attack patterns.
The 2025 implementations feature enhanced AI-driven algorithms that continuously learn from network traffic patterns, significantly reducing false positives while maintaining high detection accuracy rates across diverse network environments.
Integration with Cloud Security Architectures
The 2025 iteration of Firewalls with IDS for Malware Protection seamlessly integrates with hybrid and multi-cloud environments. These solutions provide consistent security policies across on-premises infrastructure and cloud platforms, ensuring comprehensive visibility and control.
Advanced API integrations allow for automated threat response coordination between cloud security services and traditional network perimeter defenses, creating a unified security ecosystem that adapts to dynamic workload migrations and cloud-native applications.
AI-Powered Behavioral Analysis
Next-generation systems employ sophisticated machine learning models that analyze network behavior patterns to detect malware activities. These AI engines establish baselines of normal network operations and identify deviations that may indicate compromise attempts.
The 2025 platforms feature self-improving algorithms that enhance their detection capabilities over time, automatically updating threat intelligence and adapting to new attack methodologies without requiring manual intervention or signature updates.
Real-time Response and Automated Mitigation
Firewalls with IDS for Malware Protection 2025 implement automated response mechanisms that instantly quarantine threats upon detection. These systems feature programmable response actions that can isolate infected endpoints, block malicious traffic, and initiate remediation procedures without human intervention.
The integration with Security Orchestration, Automation and Response (SOAR) platforms enables coordinated defense measures across multiple security layers, significantly reducing mean time to detection and response.
Compliance and Regulatory Alignment
The 2025 solutions are designed to meet evolving regulatory requirements and industry compliance standards. These systems provide comprehensive logging, auditing, and reporting capabilities that demonstrate adherence to data protection regulations and security frameworks.
Advanced features include automated compliance reporting, audit trail generation, and integration with governance, risk, and compliance (GRC) platforms, ensuring organizations maintain regulatory compliance while implementing robust malware protection measures.
| Feature | 2020 Standard | 2025 Advanced |
| Threat Detection Method | Signature-based | AI Behavioral Analysis |
| Response Time | Minutes | Milliseconds |
| Cloud Integration | Basic API | Native Multi-cloud |
| Automation Level | Manual rules | AI-driven automation |
| Compliance Features | Basic logging | Automated reporting |
Guide to Implementing Firewalls with IDS for Malware Protection 2025
How do modern firewalls integrate IDS capabilities for enhanced network security in 2025?
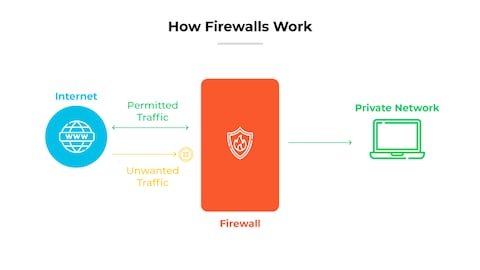
Modern firewalls in 2025 integrate Intrusion Detection System (IDS) capabilities through deep packet inspection and machine learning algorithms that analyze network traffic in real-time, identifying and mitigating threats such as malware, zero-day exploits, and anomalous behavior by correlating data across layers and leveraging cloud-based threat intelligence feeds for proactive defense, with Firewalls with IDS for Malware Protection 2025 emphasizing automated response mechanisms like quarantine and traffic blocking to minimize human intervention and enhance security posture.
Deep Packet Inspection and Behavioral Analysis
Modern firewalls utilize deep packet inspection (DPI) combined with behavioral analysis to examine data packets at a granular level, identifying malicious patterns and deviations from normal network behavior; this integration allows for the detection of sophisticated threats like encrypted malware or polymorphic code by analyzing packet headers, payloads, and session data in real-time, ensuring comprehensive visibility and threat mitigation without significant latency.
Machine Learning and AI-Driven Threat Detection
By incorporating machine learning (ML) and artificial intelligence, firewalls can autonomously adapt to evolving threats, using historical data and anomaly detection models to predict and identify intrusions; these systems continuously learn from network traffic patterns, improving accuracy over time and reducing false positives, while enabling proactive responses such as automatically updating rules or isolating compromised devices to maintain robust security.
Cloud Integration and Automated Response Mechanisms
Integration with cloud-based security platforms enhances IDS capabilities by providing access to global threat intelligence and real-time updates, allowing firewalls to quickly识别 and respond to emerging threats; automated mechanisms, such as immediate traffic blocking or alert escalation, ensure rapid containment without manual intervention, significantly reducing the window of vulnerability and strengthening overall network defense.
| Feature | Description | Benefit |
|---|---|---|
| Real-Time Analysis | Continuous monitoring of network traffic using stream processing | Immediate threat detection and response |
| Threat Intelligence Feeds | Integration with external databases for up-to-date malware signatures | Enhanced accuracy in identifying known and unknown threats |
| Automated Quarantine | Isolation of affected systems upon detection | Prevents lateral movement of threats within the network |
What criteria determine the effectiveness of an intrusion prevention system within firewalls for 2025 malware threats?

The effectiveness of an intrusion prevention system within firewalls for 2025 malware threats is determined by multiple critical criteria including real-time threat detection accuracy with minimal false positives, integration capabilities with next-generation threat intelligence feeds, scalability to handle increased network traffic and encrypted communications, behavioral analysis proficiency against zero-day and polymorphic malware, automated response mechanisms that can isolate threats without human intervention, and compliance with evolving security frameworks.
Systems must also demonstrate adaptive learning through machine learning algorithms to counteract advanced persistent threats and sophisticated social engineering attacks, ensuring robust protection for increasingly complex network architectures.
Real-Time Threat Detection and Analysis
Effective real-time threat detection is paramount for Firewalls with IDS for Malware Protection 2025, requiring advanced heuristic and signature-based analysis to identify both known and emerging malware variants instantly; this involves deep packet inspection, anomaly detection, and integration with global threat databases to minimize latency and prevent threats from propagating within the network, ensuring immediate mitigation without compromising performance.
Integration with Advanced Threat Intelligence
Seamless integration with advanced threat intelligence platforms enhances the efficacy of Firewalls with IDS for Malware Protection 2025 by providing up-to-date information on emerging malware strains, attack vectors, and malicious IP addresses; this synergy allows for proactive defense measures, dynamic policy adjustments, and enriched contextual awareness, significantly reducing the window of exposure and strengthening overall security posture against sophisticated threats.
Automated Response and Adaptive Learning Mechanisms
The capability for automated response and adaptive learning is crucial in Firewalls with IDS for Malware Protection 2025, enabling systems to autonomously quarantine infected devices, block malicious traffic, and apply patches based on machine learning algorithms that continuously analyze attack patterns; this self-improving functionality ensures sustained effectiveness against evolving threats while reducing the dependency on manual intervention and enhancing operational efficiency.
| Criteria | Key Feature | Impact on Effectiveness |
|---|---|---|
| Detection Accuracy | Low false positive rate | Ensures legitimate traffic is not disrupted |
| Behavioral Analysis | Identifies zero-day threats | Provides protection against unknown malware |
| Automation | Instant response actions | Reduces time to mitigate threats |
| Scalability | Handles high traffic volumes | Maintains performance under attack conditions |
Which next-generation firewall features are considered most critical for malware protection in 2025?

For comprehensive malware protection in 2025, next-generation firewalls must prioritize AI-driven threat intelligence, deep packet inspection with SSL/TLS decryption, integrated intrusion prevention systems (IPS), and automated zero-day threat mitigation. These features enable real-time analysis of encrypted traffic, behavioral anomaly detection, and proactive blocking of emerging threats, with Firewalls with IDS for Malware Protection 2025 being particularly critical for identifying and neutralizing sophisticated attacks before they infiltrate networks.
AI-Driven Threat Intelligence and Behavioral Analysis
AI-driven threat intelligence will be paramount in 2025, as it enables firewalls to analyze vast datasets in real-time to identify unknown malware variants and suspicious behavioral patterns. By leveraging machine learning algorithms, these systems can predict and block zero-day attacks, adapt to evolving threats, and reduce false positives. The integration of global threat feeds and automated response mechanisms ensures that firewalls remain proactive rather than reactive, significantly enhancing organizational security posture against advanced persistent threats.
Integrated Intrusion Prevention and SSL/TLS Decryption
The ability to decrypt and inspect SSL/TLS encrypted traffic is non-negotiable for modern malware defense, as a significant portion of malicious payloads are hidden within encrypted channels. Coupled with integrated intrusion prevention systems (IPS), this feature allows firewalls to detect and block covert command-and-control communications and data exfiltration attempts. Firewalls with IDS for Malware Protection 2025 will rely heavily on this combination to ensure comprehensive visibility and control over all network traffic, regardless of encryption.
Zero-Trust Network Access and Micro-Segmentation
Implementing zero-trust principles through micro-segmentation will be a cornerstone of next-generation firewall capabilities, limiting lateral movement of malware within networks. By enforcing strict identity verification and least-privilege access policies, firewalls can contain breaches and prevent malware from spreading beyond initial entry points. This approach minimizes the attack surface and ensures that even if one segment is compromised, the entire network remains protected.
| Feature | Key Capability | Benefit for Malware Protection |
|---|---|---|
| AI-Driven Threat Intelligence | Real-time behavioral analysis | Proactive zero-day threat detection |
| SSL/TLS Decryption | Deep packet inspection of encrypted traffic | Uncovers hidden malware in encrypted channels |
| Integrated IPS | Signature and anomaly-based blocking | Prevents intrusion and command-and-control attacks |
| Micro-Segmentation | Network isolation based on policies | Contains malware spread and limits lateral movement |
To what extent can contemporary firewalls with integrated IDS mitigate malware risks in 2025?
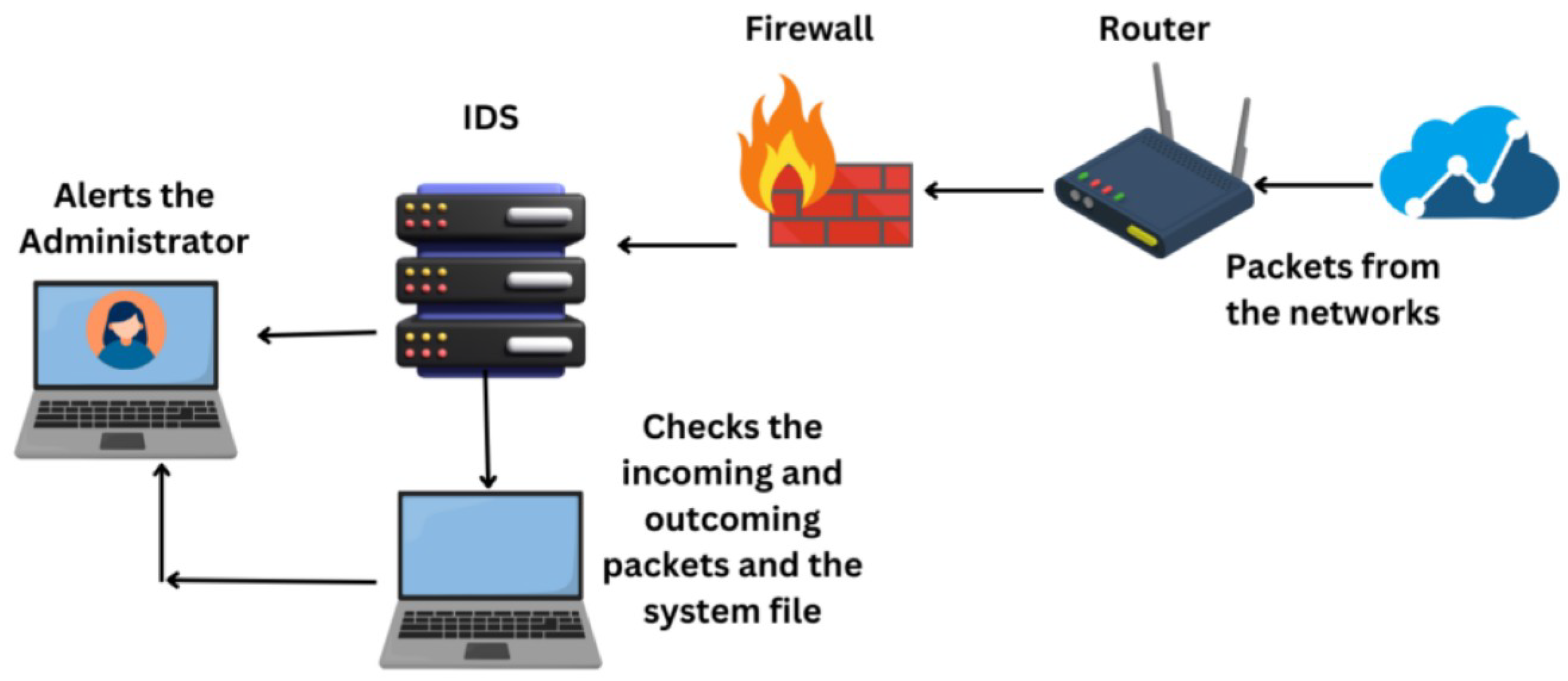
Contemporary firewalls with integrated IDS will significantly mitigate malware risks in 2025 through multi-layered threat detection, combining signature-based analysis with advanced behavioral heuristics and machine learning to identify zero-day threats and polymorphic malware; however, their effectiveness will be constrained by encrypted traffic obfuscation, sophisticated social engineering tactics bypassing perimeter defenses, and the increasing prevalence of fileless malware and supply chain attacks that require complementary endpoint and network segmentation strategies, making them a critical but not complete solution within a defense-in-depth framework for Firewalls with IDS for Malware Protection 2025.
Detection Capabilities Against Evolving Malware
Modern integrated systems leverage deep packet inspection and behavioral analytics to identify malicious patterns in network traffic, effectively countering polymorphic and encrypted malware variants by analyzing communication behaviors and payload structures before they reach endpoints; these systems employ real-time signature updates and threat intelligence feeds to adapt to new threats, though highly sophisticated attacks using legitimate tools (like LOLBins) may evade detection without additional context-aware security layers.
| Feature | Impact on Malware Mitigation | Limitation |
|---|---|---|
| Behavioral Heuristics | Detects zero-day malware | False positives in complex environments |
| Encrypted Traffic Analysis | Identifies malicious TLS patterns | Limited by perfect forward secrecy |
| Machine Learning Integration | Adapts to emerging threats | Requires extensive training data |
Integration with Broader Security Ecosystems
The efficacy of Firewalls with IDS for Malware Protection 2025 hinges on seamless interoperability with SIEM systems, endpoint protection platforms, and cloud security gateways, enabling correlated threat response and automated containment; this orchestration allows for immediate isolation of compromised devices and blocking of malicious IPs, though deployment complexities in hybrid environments and latency in cross-platform data synchronization can create coverage gaps during rapid attack cycles.
Limitations in Addressing Insider and Supply Chain Threats
While excelling at perimeter defense, these systems struggle with insider threats and software supply chain compromises where malicious activity originates from trusted entities or legitimate software updates, as the IDS may treat such traffic as authorized; additional controls like zero-trust architectures and strict software attestation are necessary to mitigate these risks, highlighting that firewalls with IDS alone cannot fully eliminate malware intrusion vectors in 2025's threat landscape.
More information of interest
What is the difference between a traditional firewall and a next-generation firewall with IDS for malware protection in 2025?
Traditional firewalls primarily focus on monitoring and controlling network traffic based on predetermined security rules, such as allowing or blocking ports and IP addresses. In contrast, next-generation firewalls (NGFWs) with integrated Intrusion Detection Systems (IDS) in 2025 offer advanced capabilities, including deep packet inspection, application-level filtering, and real-time malware detection using behavioral analysis and AI-driven threat intelligence to identify and mitigate sophisticated threats.
How does an IDS enhance malware protection in modern firewalls?
An Intrusion Detection System (IDS) significantly enhances malware protection by continuously analyzing network traffic for suspicious patterns or anomalies that may indicate malicious activity. By leveraging signature-based detection and machine learning algorithms, it can identify known malware signatures as well as zero-day threats, providing an additional layer of security that complements the firewall’s access control features.
What are the key features to look for in a firewall with IDS for malware protection in 2025?
When selecting a firewall with IDS for malware protection in 2025, key features to prioritize include real-time threat intelligence updates, behavioral analytics capable of detecting zero-day attacks, seamless integration with cloud and on-premises environments, and automated response mechanisms that can isolate infected devices or block malicious traffic without manual intervention.
Can a firewall with IDS completely prevent all malware infections?
While a firewall with IDS provides robust malware protection, it cannot guarantee complete prevention of all infections due to the evolving nature of cyber threats. However, it significantly reduces risk by blocking known threats and identifying suspicious behavior. For comprehensive security, it should be part of a layered defense strategy that includes endpoint protection, user education, and regular system updates.




Deja una respuesta