
Hardware Firewalls for High-Speed Security
- Key Components of Hardware Firewalls for High-Speed Security
- Comprehensive Guide to Hardware Firewalls for High-Speed Security
- What are the key factors in determining the best hardware firewall for high-speed security applications?
- How do hardware firewalls compare to software-based alternatives in delivering high-speed network security?
- Which firewall system architecture provides the highest level of security while maintaining optimal throughput performance?
- More information of interest
- What is a hardware firewall and how does it provide high-speed security?
- What are the key features to look for in a high-speed hardware firewall?
- How does a hardware firewall compare to a software firewall in terms of performance?
- Can a hardware firewall be integrated into an existing network infrastructure easily?
Hardware Firewalls for High-Speed Security, in today's digital landscape, organizations demand robust security solutions that can keep pace with escalating network speeds and sophisticated cyber threats. The deployment of dedicated hardware firewalls for high-speed security offers a critical layer of protection, filtering traffic at the network perimeter with minimal latency.

These appliances are engineered to handle substantial throughput while enforcing granular access policies, making them indispensable for enterprises with high-bandwidth requirements. By integrating advanced threat intelligence and deep packet inspection capabilities, hardware firewalls for high-speed security provide a scalable, reliable defense mechanism essential for safeguarding sensitive data and maintaining operational continuity in fast-evolving IT environments.
You may also be interested in reading: Home Firewalls for Safe Internet Browsing 2025
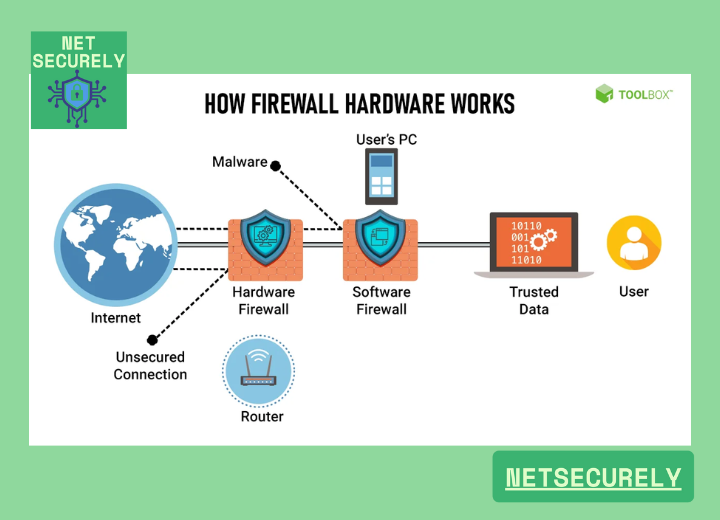
Key Components of Hardware Firewalls for High-Speed Security
Hardware Firewalls for High-Speed Security are dedicated physical devices designed to protect network infrastructure by filtering incoming and outgoing traffic based on predefined security rules. These appliances operate at the network perimeter, providing a robust first line of defense against cyber threats while maintaining optimal network performance. Unlike software firewalls, they are optimized for high-throughput environments, making them ideal for enterprises, data centers, and organizations requiring minimal latency alongside maximum protection. Their architecture typically includes specialized processors, deep packet inspection capabilities, and scalable interfaces to handle gigabit or even terabit speeds without compromising security efficacy.
Architecture and Operational Principles
The architecture of Hardware Firewalls for High-Speed Security is built around specialized components such as ASICs (Application-Specific Integrated Circuits) or FPGAs (Field-Programmable Gate Arrays), which enable rapid packet processing. These devices utilize stateful inspection to monitor active connections and enforce policies based on traffic context. By operating at the network layer, they efficiently filter data packets, block unauthorized access, and mitigate threats like DDoS attacks, all while maintaining high throughput rates essential for modern high-speed networks.
Performance and Throughput Capabilities
Performance is a critical aspect of Hardware Firewalls for High-Speed Security, with throughput metrics often exceeding 100 Gbps in enterprise-grade models. These devices minimize latency through hardware acceleration and parallel processing, ensuring that security checks do not bottleneck network speed. Key factors influencing performance include packet size, rule complexity, and enabled features (e.g., VPN, IPS). High-end models support line-rate filtering, meaning they can process data at maximum network speeds without degradation.
Deployment Scenarios and Use Cases
Hardware Firewalls for High-Speed Security are deployed in environments where both security and performance are paramount. Common use cases include protecting data centers, securing WAN links, and safeguarding critical infrastructure networks. They are also ideal for sectors like finance, healthcare, and e-commerce, where high-volume transactions require uninterrupted, secure connectivity. Deployment can be at the network edge, between internal segments, or in redundant clusters for high availability.
Security Features and Threat Mitigation
These firewalls offer advanced security features such as intrusion prevention systems (IPS), application control, and deep packet inspection (DPI). They effectively mitigate threats like malware, ransomware, and unauthorized access by enforcing granular policies. Additionally, many models include SSL/TLS inspection to decrypt and analyze encrypted traffic, providing visibility into modern threats that often hide in encrypted channels. Regular firmware updates ensure protection against emerging vulnerabilities.
Scalability and Future-Proofing
Scalability is a hallmark of Hardware Firewalls for High-Speed Security, allowing organizations to expand capacity through modular upgrades or clustered configurations. Future-proofing involves support for evolving standards like IPv6, integration with cloud environments, and adaptability to new threat landscapes. High-end devices offer features like SD-WAN compatibility and API-driven automation, ensuring long-term relevance in dynamic network architectures.
| Feature | Entry-Level Models | Enterprise Models |
| Throughput | 1-10 Gbps | Up to 100+ Gbps |
| Interfaces | 1-10 GbE ports | 10/25/40/100 GbE ports |
| IPS Performance | Moderate | High with hardware acceleration |
| High Availability | Basic failover | Active-active clustering |
| Threat Prevention | Standard signatures | Advanced AI/ML-based detection |
Comprehensive Guide to Hardware Firewalls for High-Speed Security
What are the key factors in determining the best hardware firewall for high-speed security applications?

The key factors in determining the best hardware firewall for high-speed security applications include throughput performance under maximum threat inspection loads, latency minimization, and scalability to handle growing network traffic without degradation. Essential considerations are the processing power (including specialized ASICs or multi-core CPUs), memory capacity, and support for advanced security features like deep packet inspection, intrusion prevention, and VPN capabilities without compromising speed. Additionally, redundancy features, ease of management, and vendor support for updates and vulnerabilities are critical to ensure continuous, reliable protection in dynamic high-speed environments, making the selection of appropriate Hardware Firewalls for High-Speed Security a balance between raw performance and comprehensive threat mitigation.
Performance and Throughput Metrics
Performance and throughput are paramount when selecting hardware firewalls for high-speed security applications, as these devices must process massive volumes of network traffic without introducing bottlenecks. Key metrics include maximum throughput with all security features enabled (such as DPI and IPS), packet processing rates, and latency figures, ensuring the firewall can sustain line-rate speeds even under heavy load. It is critical to evaluate performance in real-world scenarios rather than theoretical maximums, as encryption/decryption processes and simultaneous connections can significantly impact efficiency.
Security Features and Inspection Capabilities
Advanced security features are essential for effective threat protection in high-speed environments, requiring hardware firewalls to perform deep packet inspection, intrusion prevention, and application control without sacrificing performance. Capabilities such as SSL/TLS inspection, threat intelligence integration, and automated threat response must be supported by dedicated processing resources to maintain throughput. The firewall should also offer customizable security policies and regular signature updates to defend against evolving threats, ensuring comprehensive security without compromising network speed.
Scalability and Future-Proofing
Scalability ensures that a hardware firewall can accommodate future growth in network traffic and complexity, making it a crucial factor for long-term viability in high-speed security applications. Features such as modular expansion slots, support for higher bandwidth interfaces (e.g., 10/40/100 Gbps), and clustering capabilities for load balancing and high availability are important. Additionally, the firewall should be compatible with emerging technologies and protocols to avoid obsolescence, providing a foundation for adaptable and resilient network security.
| Factor | Description | Importance for High-Speed Security |
|---|---|---|
| Throughput | Data processing rate with security features active | Ensures no network slowdown during peak traffic |
| Latency | Delay in packet processing | Critical for real-time applications and user experience |
| Hardware Acceleration | Use of ASICs/FPGAs for specific tasks | Boosts performance for encryption and inspection |
| Redundancy | Failover and high availability features | Maintains continuous operation without interruptions |
How do hardware firewalls compare to software-based alternatives in delivering high-speed network security?

Hardware firewalls and software-based alternatives differ significantly in delivering high-speed network security, with hardware firewalls typically offering superior performance for high-throughput environments due to their dedicated processing units, specialized ASICs, and the ability to operate independently of host systems, which eliminates resource contention and reduces latency, whereas software firewalls run on general-purpose hardware and rely on the host's CPU and memory, making them more susceptible to performance bottlenecks under heavy traffic loads, though they provide greater flexibility and lower initial costs for smaller-scale or dynamic deployments; ultimately, the choice depends on balancing throughput requirements, scalability needs, and infrastructure constraints, with hardware firewalls for high-speed security being the preferred option for enterprises demanding consistent, low-latency protection without compromising network speed.
Performance and Throughput Capabilities
Hardware firewalls excel in performance and throughput by utilizing dedicated hardware components such as ASICs (Application-Specific Integrated Circuits) and network processors designed solely for packet inspection and filtering, enabling them to handle multi-gigabit traffic with minimal latency, whereas software firewalls depend on the host system's general-purpose CPU and RAM, which can lead to resource contention and reduced efficiency under high load, making hardware solutions more suitable for data centers or networks requiring uninterrupted high-speed operations; for example, a typical enterprise-grade hardware firewall can sustain throughput of 10 Gbps or higher with consistent security policy enforcement, while software alternatives may struggle to maintain comparable speeds without significant hardware upgrades.
Deployment Flexibility and Scalability
Software firewalls offer greater deployment flexibility as they can be installed on existing servers, virtual machines, or end-user devices, allowing for rapid provisioning and cost-effective scaling in cloud or hybrid environments, whereas hardware firewalls require physical installation and are less adaptable to dynamic changes, though they provide predictable performance and are easier to manage at scale for fixed infrastructure; a key consideration is that software solutions can be scaled horizontally by adding more instances, but hardware firewalls often support modular upgrades such as additional ports or processing cards to enhance capacity without replacing the entire unit.
Cost and Maintenance Considerations
The cost structure and maintenance demands differ substantially: hardware firewalls involve higher upfront capital expenses for the physical appliance and specialized components, but they typically have lower long-term overhead due to reduced dependency on host resources and streamlined management interfaces, while software firewalls have lower initial costs but may incur higher operational expenses related to licensing fees, compatibility updates, and potential performance tuning on host systems; additionally, hardware solutions often include dedicated support and longer lifecycle management, whereas software versions require regular patches and integration with existing OS environments, impacting total cost of ownership.
| Aspect | Hardware Firewalls | Software Firewalls |
|---|---|---|
| Throughput | High (e.g., 10+ Gbps) | Variable (depends on host hardware) |
| Latency | Low and consistent | Higher under load |
| Deployment Time | Longer (physical setup) | Faster (software installation) |
| Scalability | Vertical (hardware upgrades) | Horizontal (add instances) |
| Cost Initial/Ongoing | High capital, lower operational | Low capital, higher operational |
Which firewall system architecture provides the highest level of security while maintaining optimal throughput performance?

The next-generation firewall (NGFW) architecture, particularly when implemented as a dedicated appliance-based solution, provides the highest level of security while maintaining optimal throughput performance by integrating deep packet inspection (DPI), intrusion prevention systems (IPS), application awareness, and threat intelligence feeds into a single, streamlined platform that processes traffic at wire speed using specialized ASICs and multi-core processors to handle encryption, stateful inspection, and advanced threat mitigation without significant latency, making it ideal for environments requiring both robust security and high-speed data processing, such as Hardware Firewalls for High-Speed Security deployments in enterprise networks.
Key Components of High-Performance Firewall Architecture
A high-performance firewall architecture integrates several critical components to balance security and throughput, including application-specific integrated circuits (ASICs) for accelerated packet processing, multi-core CPUs to distribute workloads efficiently, and dedicated security processors for handling encryption and decryption tasks at line rate; these elements work in concert to support deep packet inspection (DPI), intrusion prevention systems (IPS), and advanced threat detection without introducing bottlenecks, ensuring that security policies are enforced dynamically while maintaining low latency and high data transfer rates even under heavy network loads.
Comparison of Firewall Architectures for Security and Performance
When evaluating firewall architectures for both security efficacy and performance, appliance-based firewalls typically outperform software-based or virtualized solutions due to their hardware-optimized design, which minimizes resource contention and leverages specialized processing units for tasks like stateful inspection and encryption/decryption; the table below highlights key differences:
| Architecture Type | Security Level | Throughput Performance | Use Case |
|---|---|---|---|
| Software Firewall | Moderate | Variable (CPU-dependent) | Small networks, endpoints |
| Virtual Firewall | High (flexible policies) | Limited by host resources | Cloud, virtualized environments |
| Hardware Appliance | Very High (dedicated resources) | Optimal (ASIC-accelerated) | Enterprise, data centers |
Optimizing Throughput Without Compromising Security
To achieve optimal throughput without sacrificing security, architectures must employ techniques such as parallel processing across multiple cores, hardware offloading for encryption (e.g., via AES-NI), and efficient rule set design that prioritizes traffic and minimizes unnecessary inspections; additionally, leveraging dedicated interfaces for management and data planes reduces overhead, while adaptive scanning mechanisms focus resources on suspicious traffic, ensuring that benign data flows are processed rapidly while potential threats are subjected to deeper analysis, thus maintaining a balance between high-speed data transmission and comprehensive protection.
More information of interest
What is a hardware firewall and how does it provide high-speed security?
A hardware firewall is a physical device that acts as a barrier between a network and external threats, filtering traffic based on predefined security rules. It offers high-speed security by processing network packets at line rate using dedicated hardware, ensuring minimal latency while protecting against unauthorized access, malware, and other cyber threats without compromising network performance.
What are the key features to look for in a high-speed hardware firewall?
When selecting a high-speed hardware firewall, prioritize features such as throughput capacity, which determines data processing speed, low latency for real-time applications, advanced threat prevention capabilities like intrusion detection and deep packet inspection, and scalability to accommodate growing network demands without performance degradation.
How does a hardware firewall compare to a software firewall in terms of performance?
A hardware firewall outperforms a software firewall in performance and efficiency because it operates on dedicated hardware with optimized processing power, reducing the load on individual devices. This allows it to handle high-volume traffic at faster speeds, whereas software firewalls rely on a device's resources, which can slow down system performance and are less effective in high-bandwidth environments.
Can a hardware firewall be integrated into an existing network infrastructure easily?
Yes, a hardware firewall can typically be integrated into an existing network infrastructure with relative ease, often requiring minimal configuration. It is usually deployed as a gateway device between the internal network and the internet, and many models offer plug-and-play setup or guided interfaces for seamless integration, though professional assistance may be needed for complex networks to ensure optimal security and performance.






Deja una respuesta