
Premium Antivirus for Advanced Threat Defense
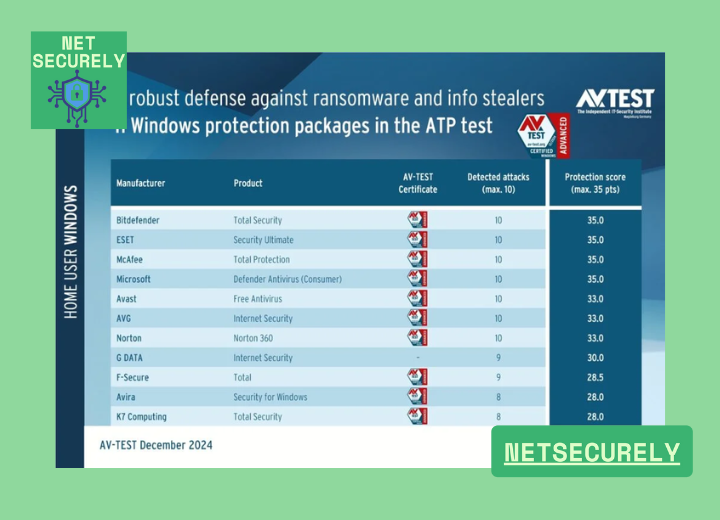
Premium Antivirus for Advanced Threat Defense, in today's digital landscape, sophisticated cyber threats demand equally advanced security solutions. Organizations and individuals face an escalating array of malware, ransomware, and zero-day exploits that traditional antivirus tools often fail to counter.

Our comprehensive analysis explores how investing in a provides multi-layered protection, combining real-time behavioral analysis, machine learning algorithms, and proactive threat hunting capabilities. This article examines why such specialized security suites are essential for safeguarding sensitive data and maintaining operational integrity against evolving cyber risks in an interconnected world.
You may also be interested in reading: Enterprise Firewalls for Scalable Protection
Premium Antivirus for Advanced Threat Defense represents the highest tier of cybersecurity solutions, engineered to counteract sophisticated digital threats that conventional antivirus software may overlook. This category of software integrates multiple protective layers, including behavioral analysis, machine learning algorithms, cloud-based threat intelligence, and real-time monitoring, to identify and neutralize advanced persistent threats (APTs), zero-day exploits, ransomware, and other complex malware. It is designed for users and organizations requiring robust security measures to safeguard sensitive data and maintain operational integrity against evolving cyber risks.
Core Protection Mechanisms
Premium Antivirus for Advanced Threat Defense employs a multi-layered approach to security. This includes signature-based detection for known threats, heuristic analysis to identify suspicious behavior patterns, and sandboxing techniques to isolate and examine potentially harmful files in a secure environment. Additionally, it utilizes machine learning models that continuously adapt to new threat vectors, ensuring proactive defense against emerging malware and sophisticated attacks that evade traditional detection methods.
Real-Time Threat Monitoring
Real-time monitoring is a critical component, scanning all system activities, network traffic, and file operations instantaneously. This feature detects and blocks threats as they occur, preventing infiltration and damage. By leveraging cloud-based analytics, the software compares potential threats against a global database of known malware, providing up-to-the-minute protection and reducing the window of vulnerability to near zero.
Advanced Behavioral Analysis
Behavioral analysis goes beyond static signatures by examining how programs and processes behave during execution. This mechanism identifies anomalies indicative of malware, such as unauthorized encryption attempts (common in ransomware) or unusual network communications. By focusing on actions rather than code patterns, Premium Antivirus for Advanced Threat Defense can intercept previously unknown threats, including zero-day attacks and polymorphic viruses.
Ransomware and Exploit Protection
Specialized shields against ransomware and exploits are integral, safeguarding personal files, documents, and system integrity. These features monitor for behaviors typical of ransomware, like mass file encryption, and block such activities before they cause harm. Exploit protection hardens vulnerable applications (e.g., browsers, office software) against attacks that target software flaws, ensuring that even unpatched systems remain secure from exploitation.
Performance and System Impact
Despite its advanced capabilities, Premium Antivirus for Advanced Threat Defense is optimized for minimal system resource usage. Through efficient coding, cloud-assisted processing, and intelligent scanning schedules, it maintains high performance without slowing down devices. Users experience seamless protection during everyday activities, with scans and updates designed to run unobtrusively in the background.
| Feature | Description | Benefit |
| Behavioral Analysis | Monitors program behavior in real-time to detect anomalies | Identifies unknown and zero-day threats effectively |
| Cloud-Based Intelligence | Leverages global threat data for immediate updates | Ensures protection against the latest malware variants |
| Ransomware Shield | Blocks unauthorized file encryption attempts | Protects critical data from being held hostage |
| Exploit Mitigation | Hardens applications against vulnerability attacks | Prevents exploitation of software flaws |
| Low System Impact | Optimized resource usage during scans and operations | Maintains device performance without slowdowns |
How does Bitdefender Advanced Threat Defense provide protection against sophisticated cyber threats?
Bitdefender Advanced Threat Defense provides protection against sophisticated cyber threats through a multi-layered approach that combines behavioral analysis, machine learning, and cloud-based sandboxing to detect and neutralize previously unknown malware and zero-day exploits. It continuously monitors application behavior in real-time, using advanced heuristics to identify suspicious activities and isolating potential threats before they can cause harm. This proactive system operates alongside Bitdefender’s Premium Antivirus for Advanced Threat Defense, ensuring comprehensive security by correlating data across endpoints and leveraging global threat intelligence to preemptively block complex attacks such as ransomware, advanced persistent threats (APTs), and fileless attacks.
Behavioral Detection and Analysis
Bitdefender Advanced Threat Defense employs sophisticated behavioral detection to analyze the actions of applications and processes in real-time, identifying malicious behavior based on deviations from normal operations rather than relying solely on traditional signature-based methods. This approach allows it to detect zero-day threats and polymorphic malware that evade conventional antivirus solutions by monitoring for activities such as unauthorized registry changes, suspicious network communications, or attempts to exploit system vulnerabilities. By leveraging machine learning algorithms, the system continuously refines its understanding of threat behaviors, ensuring robust protection against evolving cyber threats.
Cloud-Based Sandboxing Technology
The cloud-based sandboxing component isolates and executes suspicious files in a secure, virtualized environment to observe their behavior without risking the host system. This enables Bitdefender Advanced Threat Defense to safely analyze potentially malicious code, documents, or URLs, detecting hidden threats that may use evasion techniques to avoid detection in real-world scenarios. The sandbox mimics various operating systems and software configurations to lure advanced threats into revealing their true intent, and any malicious activity observed is immediately blocked, with threat intelligence shared across the Bitdefender network to enhance collective security.
| Sandbox Feature | Function | Benefit |
|---|---|---|
| Dynamic Analysis | Executes files in isolated environment | Detects evasive malware |
| Cross-Platform Emulation | Simulates multiple OS environments | Uncovers targeted threats |
| Real-Time Reporting | Generates detailed behavior logs | Enables rapid response |
Integration with Endpoint Security and Threat Intelligence
Bitdefender Advanced Threat Defense seamlessly integrates with endpoint protection solutions and leverages a global network of threat intelligence to provide context-aware security. It correlates data from millions of sensors worldwide to identify emerging threats and attack patterns, enabling preemptive blocking of sophisticated campaigns. This integration ensures that endpoints are protected not only by local analysis but also through insights derived from a broad ecosystem, enhancing the ability to defend against coordinated attacks such as advanced persistent threats (APTs) and large-scale malware distributions.
Which antivirus solutions are employed by the US military for advanced threat defense purposes?
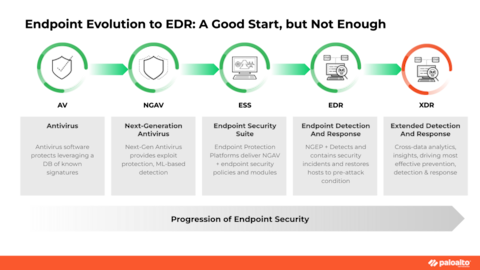
The US military employs a multi-layered cybersecurity approach utilizing specialized endpoint protection platforms rather than conventional consumer antivirus software, with solutions like McAfee's Host Based Security System (HBSS) serving as the primary enterprise-level defense system across Department of Defense networks; this comprehensive suite incorporates intrusion prevention, device control, and policy auditing capabilities alongside traditional signature-based detection, supplemented by advanced behavioral analysis tools and classified threat intelligence feeds specifically developed for military-grade protection against sophisticated adversaries, representing what could be considered a Premium Antivirus for Advanced Threat Defense architecture tailored to critical infrastructure requirements.
Primary Enterprise Security Solutions
The cornerstone of US military cyber defense is the Host Based Security System (HBSS), which integrates multiple McAfee (now Trellix) technologies into a unified platform deployed across all DoD networks; this system provides endpoint protection, firewall management, and intrusion prevention through modules like VirusScan Enterprise for signature-based detection, Policy Auditor for compliance monitoring, and Host Intrusion Prevention System (HIPS) for behavioral blocking, creating a robust defensive architecture that operates continuously across classified and unclassified networks to detect and neutralize threats before they can compromise mission-critical systems.
Advanced Threat Detection Capabilities
Beyond traditional signature-based protection, military systems incorporate behavioral analysis, machine learning algorithms, and sandboxing technologies to identify zero-day exploits and advanced persistent threats; these capabilities include memory scanning for fileless malware, network traffic analysis, and heuristic detection methods that examine code execution patterns rather than relying solely on known malware signatures, enabling proactive defense against sophisticated nation-state actors who frequently develop custom malware specifically designed to evade conventional security measures.
Implementation and Operational Protocols
| Component | Function | Deployment Scope |
|---|---|---|
| VirusScan Enterprise | Signature-based malware detection | All DoD endpoints |
| Host IPS | Behavioral threat prevention | Critical servers & workstations |
| Policy Auditor | Security compliance monitoring | Network infrastructure |
| Rogue System Detection | Unauthorized device identification | Perimeter networks |
Implementation follows strict Defense Information Systems Agency (DISA) security technical implementation guides with mandatory configuration standards and continuous monitoring through Security Content Automation Protocol (SCAP) validation; operational protocols require real-time threat reporting to joint service cyber commands and automated response actions that include network isolation, process termination, and forensic data collection without requiring manual intervention during active cyber incidents.
More information of interest
Our Premium Antivirus for Advanced Threat Defense is a comprehensive security solution designed to protect against sophisticated cyber threats. It combines real-time scanning, behavioral analysis, and machine learning algorithms to detect and neutralize malware, ransomware, zero-day exploits, and other advanced attacks that traditional antivirus software may miss.
How does it protect against zero-day threats?
This premium antivirus employs advanced heuristics and cloud-based threat intelligence to identify and block zero-day threats before they can cause harm. By analyzing file behavior and network activity patterns, it proactively defends against previously unknown vulnerabilities and exploits without relying solely on signature-based detection.
Does it include additional security features beyond antivirus protection?
Yes, it offers a multi-layered security suite including a firewall, secure browsing tools, ransomware protection, and identity theft prevention. These features work together to provide holistic defense against phishing attempts, data breaches, unauthorized access, and other cyber risks in today’s interconnected digital environment.
Is it suitable for both individual and business use?
Absolutely. The solution is scalable and offers tailored plans for individual users, small businesses, and enterprise environments. Business editions include centralized management consoles, policy enforcement, and dedicated support to ensure robust protection across all devices and networks within an organization.





Deja una respuesta