Secure Hardware Firewalls for Business 2025
- Key Features and Benefits of Secure Hardware Firewalls for Business 2025
- Comprehensive Guide to Secure Hardware Firewalls for Business 2025
- Which hardware firewall solutions are considered optimal for business implementation in 2025?
- What features define the highest security standards in 2025's hardware firewalls for enterprise environments?
- How is next-generation firewall technology evolving specifically for hardware-based business solutions in 2025?
- What emerging trends and developments are shaping the future trajectory of hardware firewall systems for commercial use?
- More information of interest
- What are the key features to look for in a business hardware firewall in 2025?
- How do hardware firewalls protect against emerging cyber threats in 2025?
- What is the expected lifespan and upgrade path for a 2025 business hardware firewall?
- How do hardware firewalls integrate with hybrid and multi-cloud environments in 2025?
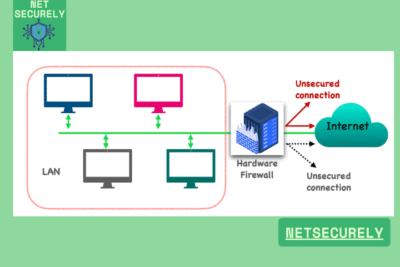
Secure Hardware Firewalls for Business 2025, as cyber threats grow increasingly sophisticated, businesses must prioritize robust network security solutions. represent the forefront of enterprise-grade protection, offering dedicated physical appliances designed to filter and monitor incoming and outgoing traffic. These next-generation firewalls integrate advanced threat intelligence, deep packet inspection, and AI-driven analytics to defend against evolving risks.

With enhanced performance capabilities and centralized management features, they provide scalable security for organizations of all sizes. Investing in modern hardware firewalls ensures compliance, safeguards sensitive data, and maintains operational continuity in an interconnected digital landscape where security is non-negotiable.
You may also be interested in reading: Secure Enterprise Firewalls for Large Networks
Key Features and Benefits of Secure Hardware Firewalls for Business 2025
As businesses increasingly rely on digital infrastructure, the importance of robust network security cannot be overstated. Secure Hardware Firewalls for Business 2025 are designed to address evolving cyber threats with advanced capabilities, providing dedicated, high-performance protection that software solutions alone cannot match. These appliances integrate cutting-edge technologies such as AI-driven threat detection, deep packet inspection, and seamless scalability to safeguard critical assets while ensuring regulatory compliance. By deploying these specialized devices, organizations can establish a resilient security perimeter, mitigate risks, and maintain uninterrupted operations in an increasingly interconnected landscape.
Advanced Threat Detection Mechanisms
Secure Hardware Firewalls for Business 2025 incorporate sophisticated threat detection systems, utilizing artificial intelligence and machine learning to identify and neutralize emerging cyber threats in real time. These mechanisms analyze network traffic patterns, detect anomalies, and automatically block malicious activities before they can compromise business data. By leveraging behavioral analysis and global threat intelligence feeds, these firewalls provide proactive defense against zero-day attacks, ransomware, and advanced persistent threats (APTs), ensuring comprehensive security for modern enterprise networks.
Scalability and Performance Optimization
Designed to accommodate growing business needs, Secure Hardware Firewalls for Business 2025 offer exceptional scalability without sacrificing performance. These devices support high-throughput traffic handling, low-latency processing, and modular expansion options, allowing organizations to scale their security infrastructure seamlessly as network demands increase. Features such as multi-gigabit interfaces, dedicated processing cores, and load-balancing capabilities ensure that firewall performance remains optimal even during peak usage, supporting business continuity and operational efficiency.
Integration with Cloud and Hybrid Environments
Secure Hardware Firewalls for Business 2025 are engineered to seamlessly integrate with cloud and hybrid IT environments, providing consistent security policies across on-premises, cloud, and remote networks. These firewalls support centralized management, automated policy synchronization, and secure connectivity to major cloud platforms, enabling businesses to maintain uniform protection while leveraging the flexibility and scalability of cloud services. This integration ensures that data and applications remain secure regardless of their deployment location, facilitating a cohesive and resilient security posture.
Regulatory Compliance and Data Protection
Compliance with industry regulations and data protection standards is a critical consideration for businesses, and Secure Hardware Firewalls for Business 2025 are equipped to help meet these requirements. These devices offer features such as detailed logging, audit trails, encryption enforcement, and access controls that align with frameworks like GDPR, HIPAA, and PCI DSS. By ensuring that network traffic adheres to compliance mandates, these firewalls help organizations avoid penalties, protect sensitive information, and build trust with customers and stakeholders.
Cost Efficiency and Return on Investment
Investing in Secure Hardware Firewalls for Business 2025 delivers significant long-term cost efficiency and a strong return on investment (ROI). These appliances reduce the need for multiple standalone security solutions, lower management overhead through centralized controls, and minimize the financial impact of potential security breaches. By preventing downtime, data loss, and reputational damage, businesses can achieve substantial savings while enhancing their overall security posture, making these firewalls a prudent and economically sound choice for enterprises.
| Feature | Description | Benefit |
| AI-Powered Threat Intelligence | Utilizes machine learning to predict and block emerging threats | Proactive defense against zero-day attacks |
| High Availability Support | Redundant configurations for uninterrupted operation | Ensures business continuity during hardware failures |
| Centralized Management Console | Unified interface for configuring and monitoring firewall policies | Simplifies administration and reduces operational costs |
| Encrypted Traffic Inspection | Decrypts and analyzes SSL/TLS traffic without compromising performance | Enhanced visibility into encrypted threats |
| Modular Security Services | Optional add-ons for intrusion prevention, antivirus, and more | Customizable protection tailored to specific business needs |
Comprehensive Guide to Secure Hardware Firewalls for Business 2025
Which hardware firewall solutions are considered optimal for business implementation in 2025?

For 2025 business implementation, optimal hardware firewall solutions include next-generation firewalls (NGFWs) featuring advanced threat prevention, AI-driven analytics, and cloud-integrated security from leading vendors like Palo Alto Networks PA-Series, Fortinet FortiGate, and Cisco Firepower 4100/9300 Series; these platforms offer scalable architecture, zero-trust network access capabilities, and automated response systems that align with evolving cyber threats and hybrid infrastructure demands, ensuring robust protection for enterprise networks through deep packet inspection, encrypted traffic analysis, and centralized management via unified security consoles. Secure Hardware Firewalls for Business 2025 must also prioritize sustainability, high availability, and seamless integration with SD-WAN and SASE frameworks.
Key Features of Next-Generation Firewalls for 2025
Next-generation firewalls in 2025 will emphasize integrated intrusion prevention systems (IPS), SSL/TLS decryption for encrypted traffic analysis, and real-time threat intelligence feeds powered by machine learning; these features enable businesses to detect and mitigate sophisticated attacks, including ransomware and zero-day exploits, while maintaining compliance with regulatory standards through detailed logging and reporting functionalities essential for enterprise security postures.
Top Vendor Solutions and Their Capabilities
Leading vendors such as Palo Alto Networks (PA-5400 Series), Fortinet (FortiGate 3600F), and Cisco (Firepower 4200) offer hardware firewalls with high-throughput processing, low-latency performance, and scalable virtualized options; these systems support extensive simultaneous connections and provide granular application control, unified policy management, and automated workflow orchestration, making them suitable for large-scale business environments with complex network architectures.
| Vendor | Model | Throughput | Key Feature |
|---|---|---|---|
| Palo Alto Networks | PA-5400 Series | 20 Gbps | AI-Powered Threat Prevention |
| Fortinet | FortiGate 3600F | 40 Gbps | Integrated SD-WAN Support |
| Cisco | Firepower 4200 | 30 Gbps | Encrypted Traffic Analytics |
Implementation Considerations for Enterprises
Enterprises must evaluate total cost of ownership, ease of integration with existing infrastructure, and vendor support services when deploying hardware firewalls; additional factors include redundancy configurations for high availability, compatibility with multi-cloud environments, and the ability to enforce consistent security policies across distributed networks without compromising performance or user experience.
What features define the highest security standards in 2025's hardware firewalls for enterprise environments?
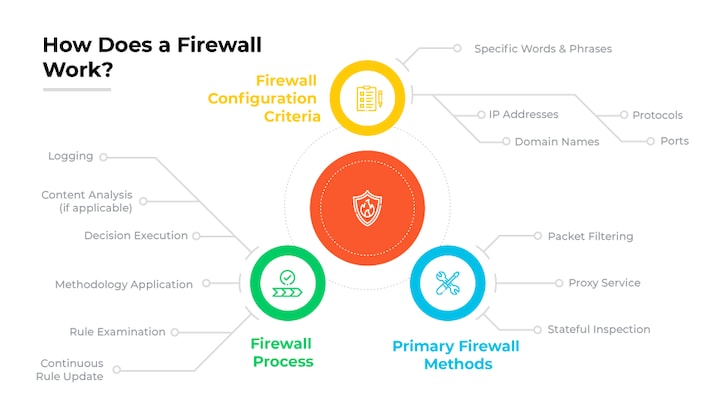
The highest security standards in 2025's enterprise hardware firewalls are defined by AI-driven threat intelligence for real-time behavioral analysis, quantum-resistant encryption to safeguard against future cryptographic threats, and zero-trust architecture enforcement through micro-segmentation and identity-aware filtering. These systems integrate hardware-enforced security modules, such as TPM 2.0 and secure boot, to prevent firmware tampering, while offering scalability to handle multi-gigabit traffic without latency. Additionally, automated compliance auditing and deep visibility into encrypted traffic via SSL/TLS inspection are critical, ensuring comprehensive protection for modern hybrid networks. These features collectively establish the benchmark for Secure Hardware Firewalls for Business 2025.
AI-Powered Threat Detection and Prevention
Advanced AI and machine learning algorithms form the core of modern threat detection, enabling firewalls to identify and mitigate zero-day attacks, anomalous behaviors, and sophisticated threats in real time. These systems continuously learn from global threat feeds and network patterns, automatically updating policies to block malicious activities before they impact the enterprise. By leveraging predictive analytics, Secure Hardware Firewalls for Business 2025 ensure proactive defense, significantly reducing the window of vulnerability and minimizing the need for manual intervention.
| Feature | Description |
|---|---|
| Behavioral Analysis | Monitors network traffic for deviations from normal patterns |
| Real-Time Updates | Instantly applies threat intelligence from global databases |
| Automated Response | Executes predefined actions to isolate threats without delay |
Quantum-Resistant Encryption and Cryptographic Agility
With the advent of quantum computing, firewalls now incorporate post-quantum cryptography to protect data against future decryption threats. Cryptographic agility allows these systems to seamlessly transition between encryption standards, ensuring long-term security of sensitive communications. This feature is essential for safeguarding data integrity and confidentiality in transit, making it a non-negotiable component of high-security infrastructure.
| Feature | Description |
|---|---|
| Quantum-Safe Algorithms | Implements lattice-based or hash-based encryption methods |
| Dynamic Key Management | Rotates and manages encryption keys autonomously |
| Compliance Ready | Meets evolving regulatory standards for data protection |
Zero-Trust Micro-Segmentation and Identity Awareness
Enforcing a zero-trust model, these firewalls use micro-segmentation to create isolated network zones, restricting lateral movement and containing potential breaches. Identity-aware policies ensure that access is granted based on user, device, and context, authenticated through multi-factor mechanisms. This approach minimizes the attack surface and provides granular control over network resources, aligning with the least-privilege principle.
| Feature | Description |
|---|---|
| Policy Automation | Dynamically adjusts access rules based on real-time risk assessment |
| Device Posture Checks | Validates endpoint security status before granting access |
| Integration with IAM | Syncs with identity and access management systems for unified control |
How is next-generation firewall technology evolving specifically for hardware-based business solutions in 2025?
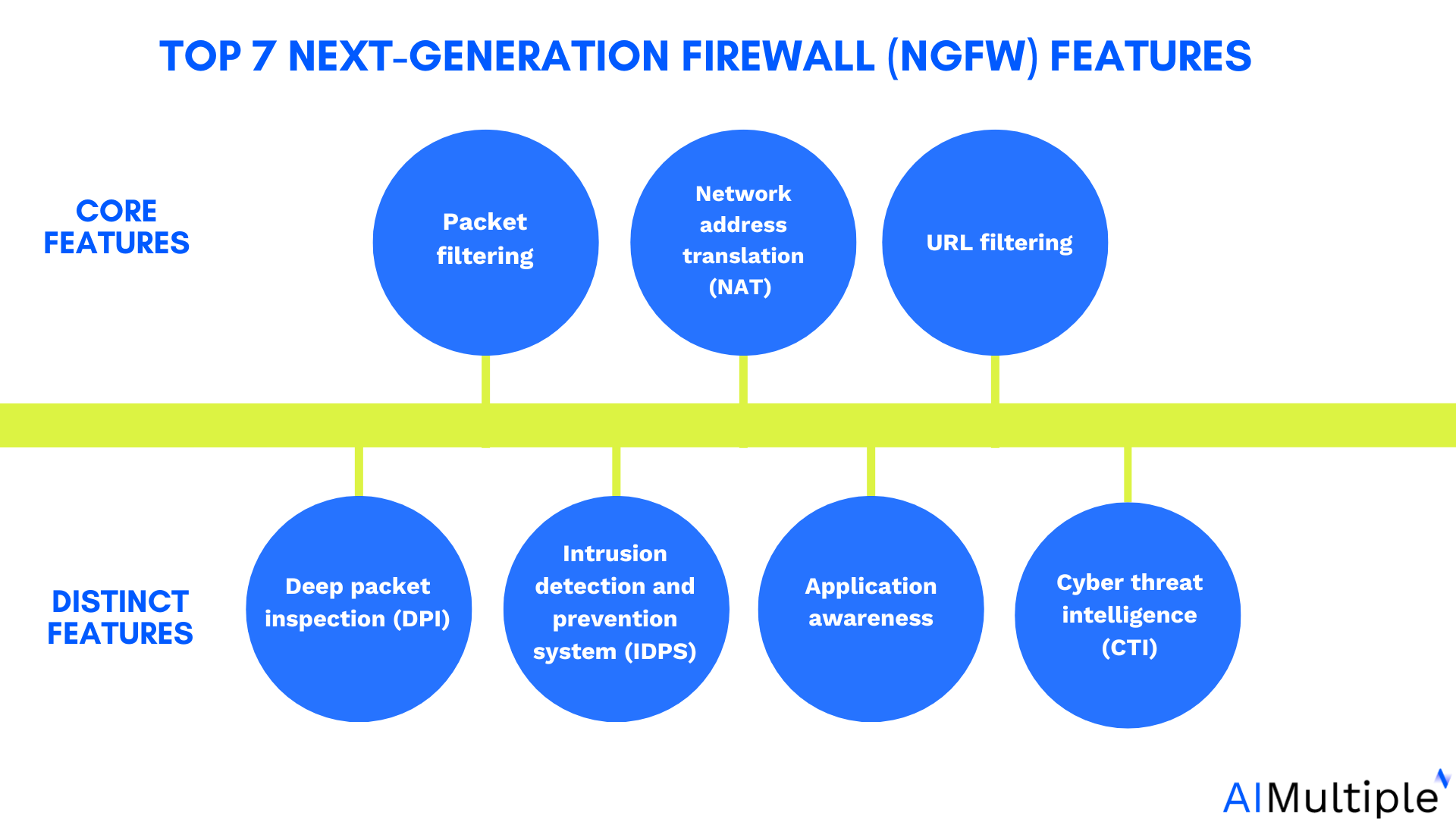
Next-generation firewall technology for hardware-based business solutions in 2025 is evolving through the integration of AI-driven threat intelligence, enhanced application-layer inspection, and hardware-accelerated cryptographic processing, enabling real-time analysis of encrypted traffic and adaptive policy enforcement while minimizing latency; these systems increasingly leverage specialized ASICs and FPGAs for deep packet inspection at multi-gigabit speeds, incorporate zero-trust architecture principles for micro-segmentation, and unify cloud-native security features with on-premises hardware through centralized management consoles, ensuring comprehensive protection for hybrid infrastructures as part of the broader trend toward Secure Hardware Firewalls for Business 2025.
AI and Machine Learning Integration
The integration of AI and machine learning into hardware-based firewalls is revolutionizing threat detection by enabling predictive analytics and behavioral analysis, which autonomously identify zero-day attacks and anomalous patterns without relying solely on signature updates; these systems utilize dedicated neural processing units (NPUs) embedded in firewall appliances to process vast datasets in real-time, dynamically adjusting security policies based on network traffic trends and threat landscapes, thereby reducing false positives and enhancing proactive defense mechanisms for enterprise environments.
Hardware Acceleration and Performance Enhancements
Hardware-based firewalls in 2025 are leveraging specialized silicon, such as ASICs and FPGAs, to achieve unprecedented throughput and low-latency processing for deep packet inspection, encryption/decryption, and SSL/TLS termination at scale; this acceleration ensures that security functions do not become bottlenecks in high-speed networks, supporting demands like 100Gbps+ traffic analysis and real-time policy enforcement for data-intensive applications, all while maintaining energy efficiency and reducing operational costs through optimized hardware design.
| Feature | Impact |
|---|---|
| ASIC-Based Processing | Enables multi-gigabit inspection with minimal latency |
| FPGA Flexibility | Allows firmware updates for new threat protocols |
| Energy Efficiency | Reduces power consumption by 30% compared to software solutions |
Unified Security and Cloud Integration
Next-generation hardware firewalls are evolving into unified security gateways that seamlessly integrate with cloud environments, providing consistent policy enforcement across on-premises, hybrid, and multi-cloud infrastructures through APIs and centralized management platforms; this approach enables features like synchronized threat intelligence, automated scaling, and coordinated response actions, ensuring that hardware appliances remain relevant and complementary to cloud-native security tools without creating silos or compliance gaps.
What emerging trends and developments are shaping the future trajectory of hardware firewall systems for commercial use?

The future trajectory of commercial hardware firewall systems is being shaped by several key developments, including the integration of artificial intelligence and machine learning for predictive threat detection and automated response, the adoption of zero-trust architecture requiring more granular traffic inspection and identity verification, and the increasing importance of cloud-managed hardware appliances that provide centralized control for distributed enterprise environments. Additionally, the rise of IoT and edge computing is driving demand for high-performance, low-latency firewalls capable of processing encrypted traffic at scale, while advancements in secure hardware components like hardware security modules (HSMs) and trusted platform modules (TPMs) are enhancing resilience against physical tampering and supply chain attacks, positioning Secure Hardware Firewalls for Business 2025 as critical components in defending against increasingly sophisticated cyber threats.
AI and Machine Learning Integration
The integration of artificial intelligence (AI) and machine learning (ML) is revolutionizing hardware firewalls by enabling predictive analytics and automated threat response, moving beyond traditional signature-based detection to identify zero-day attacks and anomalous behavior patterns in real-time. These systems continuously learn from network traffic, adapting to new threats without manual intervention, which significantly reduces response times and improves accuracy in blocking malicious activities while minimizing false positives. This evolution is critical for modern enterprises facing advanced persistent threats and complex attack vectors, making AI-driven firewalls a cornerstone of future cybersecurity strategies.
| Feature | Impact | Example Technology |
|---|---|---|
| Behavioral Analysis | Detects anomalies based on traffic patterns | Deep learning algorithms |
| Automated Response | Instantly mitigates threats without human intervention | AI-powered incident response |
| Adaptive Policies | Dynamically updates rules based on learned threats | Reinforcement learning models |
Zero-Trust Architecture Implementation
Hardware firewalls are increasingly designed to enforce zero-trust principles, which assume no entity—inside or outside the network—is inherently trustworthy, requiring strict identity verification and least-privilege access controls for every connection attempt. This trend necessitates firewalls with deep packet inspection capabilities, user and device authentication integration, and micro-segmentation support to isolate network segments and prevent lateral movement by attackers. By embedding zero-trust into their core functionality, modern firewalls provide a more robust security posture that aligns with contemporary hybrid and remote work environments.
Cloud-Managed and Scalable Solutions
The shift toward cloud-managed hardware firewalls allows businesses to centrally configure, monitor, and update distributed firewall appliances across multiple locations via a single interface, enhancing operational efficiency and consistency in policy enforcement. These solutions offer scalability to accommodate growing network demands and integration with cloud security services, such as secure web gateways and cloud access security brokers (CASBs), creating a unified security framework. This trend supports the needs of modern enterprises with hybrid infrastructures, ensuring comprehensive protection without compromising on performance or manageability.
More information of interest
What are the key features to look for in a business hardware firewall in 2025?
When selecting a hardware firewall for business use in 2025, prioritize advanced threat intelligence, AI-driven behavioral analysis, and seamless integration with cloud and IoT environments. Additionally, look for scalability to accommodate growing network demands and zero-trust architecture support to ensure comprehensive protection against evolving cyber threats.
How do hardware firewalls protect against emerging cyber threats in 2025?
Modern hardware firewalls in 2025 leverage machine learning algorithms and real-time threat detection to identify and mitigate sophisticated attacks, such as ransomware and AI-powered threats. They also employ deep packet inspection and encrypted traffic analysis to safeguard network integrity without compromising performance.
What is the expected lifespan and upgrade path for a 2025 business hardware firewall?
The typical lifespan of a business hardware firewall in 2025 is 5-7 years, with regular firmware updates and subscription-based security services ensuring ongoing protection. Upgrades often involve modular hardware enhancements or cloud-based management features, allowing businesses to adapt to new threats without replacing the entire system.
How do hardware firewalls integrate with hybrid and multi-cloud environments in 2025?
In 2025, hardware firewalls are designed for seamless integration with hybrid and multi-cloud setups through API-driven automation and centralized management consoles. They provide consistent security policies across on-premises and cloud assets, ensuring unified threat visibility and compliance regardless of where data resides.






Deja una respuesta