
Secure Hardware Firewalls for Enterprises USA

- Implementing Robust Secure Hardware Firewalls for Enterprises USA
- Comprehensive Guide to Implementing Secure Hardware Firewalls for Enterprises USA
- What defines an enterprise-grade hardware firewall and how does it differ from standard firewalls?
- What are the key features to consider when selecting a secure hardware firewall for enterprises in the USA?
- How do secure hardware firewalls protect enterprise networks against advanced cyber threats?
- What compliance requirements in the USA influence the deployment of hardware firewalls for enterprises?
- How can enterprises in the USA ensure optimal configuration and maintenance of their hardware firewalls?
- More information of interest
- What are the key features to consider when selecting a secure hardware firewall for an enterprise in the USA?
- How does a hardware firewall enhance network security for large-scale enterprises compared to software solutions?
- What are the compliance and regulatory considerations for deploying hardware firewalls in US enterprises?
- How can enterprises ensure optimal performance and maintenance of their hardware firewalls?
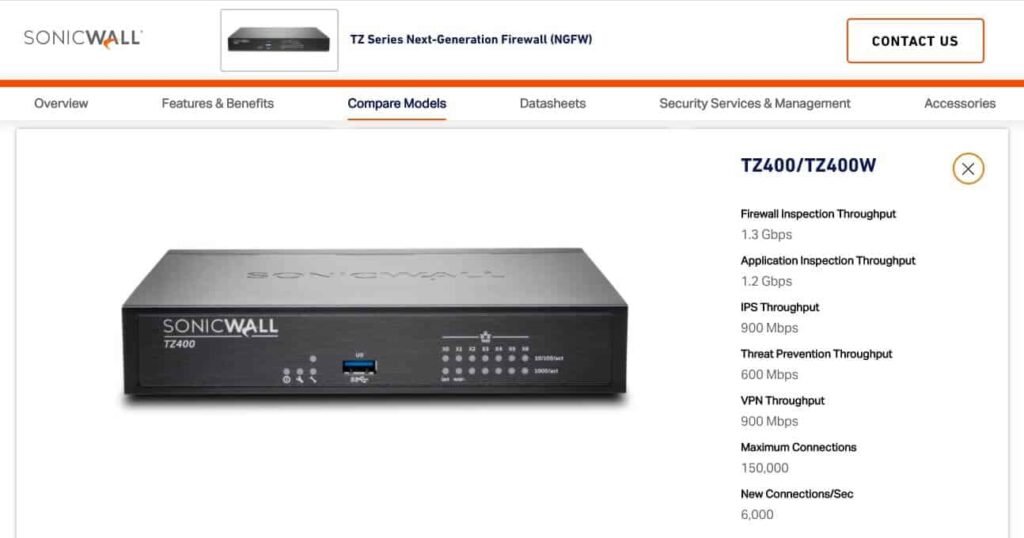
Secure Hardware Firewalls for Enterprises USA, enterprises across the United States increasingly rely on robust cybersecurity infrastructure to protect sensitive data and maintain operational integrity. As cyber threats grow in sophistication, the implementation of dedicated security appliances becomes critical. Among the most effective solutions are , which provide a physical barrier against unauthorized access and malicious traffic.
These devices offer high-performance filtering, deep packet inspection, and centralized management capabilities tailored for complex network environments. By deploying such specialized hardware, organizations can enforce stringent security policies, safeguard critical assets, and ensure regulatory compliance in an evolving digital landscape.
You may also be interested in reading: Top Dedicated Hosting for Secure Servers USA
Implementing Robust Secure Hardware Firewalls for Enterprises USA
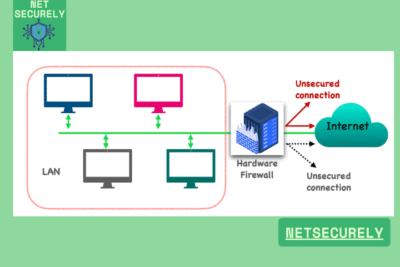
Secure Hardware Firewalls for Enterprises USA represent a critical layer of defense in modern cybersecurity infrastructures. These dedicated physical appliances are engineered to inspect and filter network traffic at the perimeter and between internal segments, providing granular control over data flows. Unlike software-based solutions, hardware firewalls operate independently of host systems, reducing vulnerability to endpoint compromises. They offer high-performance throughput, low latency, and specialized threat intelligence capabilities, making them indispensable for protecting sensitive enterprise data, ensuring regulatory compliance, and mitigating sophisticated cyber threats targeting organizational networks.
Core Security Features of Enterprise Hardware Firewalls
Enterprise-grade hardware firewalls incorporate multiple security technologies including stateful packet inspection, deep packet inspection (DPI), intrusion prevention systems (IPS), and application-aware filtering. These features work cohesively to identify and block malicious traffic, enforce security policies, and prevent unauthorized access. Advanced models often include SSL/TLS decryption for encrypted traffic analysis, threat intelligence integration for real-time updates on emerging risks, and sandboxing capabilities for detecting zero-day exploits. These functionalities ensure comprehensive network protection tailored to complex enterprise environments.
Performance and Scalability Considerations
When deploying Secure Hardware Firewalls for Enterprises USA, performance metrics such as throughput, concurrent connections, and latency are paramount. Enterprises must select appliances that can handle their specific bandwidth requirements without becoming bottlenecks. Scalability is equally critical; modular firewalls allow organizations to add processing power, additional interfaces, or security subscriptions as needs evolve. High-availability configurations with redundant units ensure uninterrupted operation, while load-balancing capabilities distribute traffic efficiently across multiple devices in large-scale deployments.
Regulatory Compliance and Standards Alignment
Hardware firewalls help U.S. enterprises meet stringent regulatory requirements such as HIPAA, PCI DSS, FISMA, and GDPR through detailed logging, access controls, and audit trails. These appliances provide the necessary capabilities to demonstrate due diligence in protecting sensitive data, including configurable reporting features that simplify compliance audits. Properly configured firewalls enforce segmentation requirements, control data flows between security zones, and maintain records of all network transactions—essential elements for proving adherence to legal and industry standards.
Integration with Existing Security Architectures
Modern hardware firewalls are designed to integrate seamlessly with broader security ecosystems through APIs, SIEM integrations, and support for standardized protocols. They can share threat intelligence with other security components, participate in automated incident response workflows, and provide contextual data to security analytics platforms. This interoperability enables enterprises to create a cohesive defense-in-depth strategy where the firewall acts as a enforcement point within a larger framework of security tools, rather than operating as an isolated solution.
Management and Operational Efficiency
Enterprise firewall management encompasses centralized policy administration, real-time monitoring, and streamlined troubleshooting. Modern systems offer intuitive graphical interfaces, role-based access controls, and automation capabilities that reduce administrative overhead. Features like zero-touch deployment, predefined security templates, and automated firmware updates help maintain operational consistency across distributed enterprises. Additionally, comprehensive reporting tools provide visibility into network traffic patterns, security events, and policy effectiveness, enabling data-driven security decisions.
| Firewall Class | Throughput Capacity | Key Enterprise Features | Typical Deployment Scale |
| Mid-Range | 5-20 Gbps | Basic IPS, VPN support, VLAN segmentation | Medium-sized business networks |
| Enterprise | 20-100 Gbps | Advanced threat prevention, SSL inspection, high availability | Large corporate networks |
| Carrier-Class | 100+ Gbps | Multi-tenant support, massive connection handling, advanced routing | Service providers & large enterprises |
Comprehensive Guide to Implementing Secure Hardware Firewalls for Enterprises USA
What defines an enterprise-grade hardware firewall and how does it differ from standard firewalls?

An enterprise-grade hardware firewall is defined by its dedicated physical appliance designed to handle high-volume network traffic with advanced security features such as deep packet inspection, intrusion prevention systems (IPS), and granular application control, operating at multi-gigabit speeds to protect large-scale networks without compromising performance; it differs from standard firewalls, which are often software-based or lower-capacity devices, by offering superior throughput, redundancy like failover support, centralized management for complex policies, and the ability to integrate with broader security ecosystems, making it essential for organizations with critical data and compliance requirements, including those seeking Secure Hardware Firewalls for Enterprises USA.
Performance and Scalability
Enterprise-grade hardware firewalls excel in performance and scalability, supporting high bandwidth demands—often ranging from 10 Gbps to over 100 Gbps—and accommodating thousands of concurrent connections without latency, unlike standard firewalls that may struggle with traffic beyond 1 Gbps or limited sessions; they feature modular designs for expandability, such as adding ports or security licenses, and are built with multi-core processors and specialized ASICs to handle intensive tasks like encryption and threat analysis efficiently, ensuring seamless growth for large networks.
| Aspect | Enterprise-Grade Firewall | Standard Firewall |
|---|---|---|
| Maximum Throughput | 10-100+ Gbps | Up to 1-5 Gbps |
| Concurrent Connections | Millions | Thousands to hundreds of thousands |
| Scalability Options | Modular hardware, license upgrades | Fixed capacity, limited expansion |
Advanced Security Features
These firewalls incorporate advanced security features beyond basic stateful inspection, including integrated intrusion prevention systems (IPS), application-aware filtering, sandboxing for threat emulation, and real-time threat intelligence feeds, which provide proactive defense against sophisticated attacks like zero-day exploits and advanced persistent threats; standard firewalls typically offer only rudimentary packet filtering and lack the depth of analysis, making them insufficient for enterprises facing evolving cyber risks that require comprehensive, multi-layered protection.
| Feature | Enterprise-Grade Firewall | Standard Firewall |
|---|---|---|
| Intrusion Prevention (IPS) | Integrated and customizable | Basic or absent |
| Application Control | Granular, layer 7 visibility | Limited or none |
| Threat Intelligence | Real-time updates and integration | Manual or minimal updates |
Reliability and Management
Enterprise solutions prioritize reliability and management through hardware redundancy like hot-swappable power supplies and fans, high availability configurations with automatic failover, and centralized management platforms that allow unified policy enforcement across distributed networks, reducing downtime and administrative overhead; in contrast, standard firewalls often lack redundancy, have simpler interfaces with limited automation, and are suited for smaller setups where continuous uptime and streamlined governance are less critical.
| Characteristic | Enterprise-Grade Firewall | Standard Firewall |
|---|---|---|
| High Availability | Active-active/active-passive support | Rare or not supported |
| Management System | Centralized, API-driven | Local web interface only |
| Hardware Redundancy | Yes (e.g., redundant PSUs) | No |
What are the key features to consider when selecting a secure hardware firewall for enterprises in the USA?

When selecting secure hardware firewalls for enterprises USA, key features to prioritize include throughput capacity to handle network traffic without latency, advanced threat protection with integrated IPS/IDS and malware scanning, high availability through redundant configurations and failover capabilities, granular policy management for precise access controls, VPN support for secure remote connectivity, scalability to accommodate growth, and compliance certifications (such as FIPS 140-2) ensuring adherence to US regulatory standards, all backed by robust vendor support and regular firmware updates.
Performance and Scalability Requirements
Performance metrics are critical when evaluating Secure Hardware Firewalls for Enterprises USA, particularly throughput under various traffic conditions (e.g., UDP, HTTP, IPS-enabled) and connection rates to prevent bottlenecks. Enterprises must assess scalability options, including modular expansion slots for additional interfaces or security processing cards, ensuring the firewall can grow with increasing network demands and support future technologies without requiring complete hardware replacement.
| Performance Metric | Enterprise Requirement | Consideration |
|---|---|---|
| Throughput (IPS Enabled) | 10 Gbps+ | Must handle peak traffic without degradation |
| Maximum Connections | 1 Million+ | Support for large user bases and devices |
| VPN Throughput | 5 Gbps+ | Critical for remote access and site-to-site tunnels |
| Scalability Options | Modular Slots | Allows future hardware enhancements |
Security and Threat Prevention Capabilities
Advanced security features are paramount, including deep packet inspection, intrusion prevention systems (IPS), and real-time threat intelligence integration to block known and emerging threats. Enterprises should prioritize firewalls with application-aware filtering, sandboxing for unknown malware analysis, and SSL/TLS decryption capabilities to inspect encrypted traffic, ensuring comprehensive protection against sophisticated attacks while maintaining compliance with industry regulations.
Management, Compliance, and Support
Effective centralized management through intuitive GUI or API interfaces simplifies policy enforcement across distributed enterprises, while logging and reporting tools aid in auditing and incident response. Compliance with US standards like NIST, FISMA, or CMMC is essential, alongside reliable vendor support offering timely firmware updates, security patches, and 24/7 technical assistance to maintain ongoing protection and operational integrity.
How do secure hardware firewalls protect enterprise networks against advanced cyber threats?

Secure hardware firewalls protect enterprise networks against advanced cyber threats by employing dedicated physical appliances that enforce strict access control policies through deep packet inspection, stateful traffic analysis, and application-layer filtering, effectively blocking malicious traffic, zero-day exploits, and sophisticated intrusion attempts before they penetrate the network perimeter; these devices often integrate threat intelligence feeds, support advanced encryption standards, and provide granular segmentation capabilities to isolate critical assets, making them indispensable components of a defense-in-depth strategy for modern cybersecurity infrastructures, particularly for organizations utilizing Secure Hardware Firewalls for Enterprises USA to safeguard sensitive data and maintain regulatory compliance.
Deep Packet Inspection and Stateful Analysis
Secure hardware firewalls utilize deep packet inspection (DPI) and stateful analysis to scrutinize both the header and payload of each data packet traversing the network, enabling the identification and blocking of malicious content, anomalous patterns, and protocol deviations that signature-based methods might miss; this granular examination allows the firewall to detect advanced threats like encrypted malware, command-and-control communications, and data exfiltration attempts by maintaining context-aware session tracking and correlating traffic behavior across multiple layers.
| Feature | Function | Benefit |
|---|---|---|
| Deep Packet Inspection | Examines packet content beyond headers | Detects hidden malware and exploits |
| Stateful Tracking | Monitors active connections and sessions | Prevents unauthorized access and spoofing |
| Protocol Validation | Ensures compliance with standard protocols | Blocks evasion techniques and anomalies |
Integration with Threat Intelligence and Automation
These firewalls integrate with global threat intelligence platforms and employ automated response mechanisms to dynamically update rule sets and block known malicious IPs, domains, and signatures in real-time, significantly reducing the window of exposure to emerging threats such as ransomware, advanced persistent threats (APTs), and zero-day vulnerabilities; this proactive approach enhances network resilience by leveraging collective security data and machine learning algorithms to predict and mitigate attacks before they cause damage.
Network Segmentation and Access Control
By enforcing granular network segmentation and role-based access control (RBAC), secure hardware firewalls compartmentalize enterprise networks into isolated zones, limiting lateral movement and containing potential breaches to minimize their impact; this strategy ensures that even if an attacker compromises one segment, critical systems and data remain protected through strict policy enforcement and micro-perimeter defenses.
What compliance requirements in the USA influence the deployment of hardware firewalls for enterprises?
The deployment of hardware firewalls for enterprises in the USA is significantly influenced by compliance requirements such as the Health Insurance Portability and Accountability Act (HIPAA), which mandates the protection of electronic protected health information (ePHI) through stringent access controls and network security measures; the Payment Card Industry Data Security Standard (PCI DSS), requiring firewalls to segment cardholder data environments and monitor traffic; the Sarbanes-Oxley Act (SOX), emphasizing internal controls over financial data integrity; and sector-specific regulations like the Gramm-Leach-Bliley Act (GLBA) for financial institutions, which enforce safeguards for customer information. These frameworks necessitate robust, auditable network perimeters, making secure hardware firewalls for enterprises USA a critical component for meeting legal obligations, avoiding penalties, and maintaining customer trust.
HIPAA Requirements for Network Security
Under HIPAA, covered entities and business associates must implement technical safeguards to protect ePHI, which directly impacts firewall deployment. Hardware firewalls are essential for enforcing access controls, monitoring network traffic, and preventing unauthorized intrusions into systems handling sensitive health data. Compliance requires documented policies, regular risk assessments, and audit trails, all supported by firewall configurations that restrict access to authorized users and systems only.
PCI DSS and Firewall Implementation
PCI DSS mandates strict firewall usage to protect cardholder data, requiring enterprises to install and maintain a firewall configuration to safeguard this information. Hardware firewalls must be deployed at all internet connections and between demilitarized zones (DMZs) and internal networks, with rules denying all unauthorized traffic and reviewed every six months. This ensures segmentation, reduces the attack surface, and supports compliance validation during audits.
SOX and GLBA Compliance Obligations
SOX requires public companies to establish internal controls over financial reporting, necessitating firewalls to secure networks housing financial data and prevent tampering. GLBA obligates financial institutions to protect customer information through administrative, technical, and physical safeguards, where firewalls are key for preventing unauthorized access and ensuring data confidentiality. Both regulations emphasize the need for auditable security measures, making hardware firewalls integral to compliance frameworks.
How can enterprises in the USA ensure optimal configuration and maintenance of their hardware firewalls?
Enterprises in the USA can ensure optimal configuration and maintenance of their hardware firewalls by implementing a structured approach that includes initial baseline configuration aligned with industry standards like NIST or CIS benchmarks, conducting regular firmware updates to patch vulnerabilities, performing continuous monitoring via SIEM integration for real-time threat detection, establishing documented change management procedures for all modifications, and scheduling quarterly audits with penetration testing to validate rule effectiveness and compliance; additionally, employing dedicated network security personnel or partnering with managed security service providers (MSSPs) ensures expert oversight, while redundancy setups and disaster recovery plans maintain availability, ultimately fortifying Secure Hardware Firewalls for Enterprises USA against evolving cyber threats.
Initial Configuration Best Practices
Optimal configuration begins with a default-deny policy where all traffic is blocked unless explicitly permitted, reducing the attack surface; enterprises should segment networks into zones (e.g., DMZ, internal LAN) applying least privilege principles, disable unnecessary services, and use encryption for management access, while adhering to frameworks like CIS Critical Security Controls to establish a robust foundation for Secure Hardware Firewalls for Enterprises USA.
| Configuration Step | Description | Best Practice |
|---|---|---|
| Rule Base Setup | Define inbound/outbound traffic rules | Order rules from specific to general |
| Network Segmentation | Divide network into security zones | Isolate sensitive data segments |
| Management Access | Configure administrative interfaces | Use SSH/HTTPS instead of HTTP/Telnet |
Ongoing Maintenance Procedures
Regular maintenance involves automated firmware updates to address security flaws, log analysis for anomaly detection, and performance tuning to prevent bottlenecks; enterprises should maintain a change log, review rule sets bi-annually for redundancies, and validate backups, ensuring Secure Hardware Firewalls for Enterprises USA operate efficiently without compromising security posture.
| Maintenance Task | Frequency | Key Action |
|---|---|---|
| Firmware Updates | Monthly or as released | Test in lab before deployment |
| Rule Review | Quarterly | Remove unused or overlapping rules |
| Backup Verification | Weekly | Store encrypted copies offsite |
Monitoring and Auditing Strategies
Continuous monitoring via SIEM integration enables real-time alerting on suspicious activities, while annual audits assess compliance with policies like HIPAA or PCI-DSS; enterprises should employ intrusion prevention systems (IPS) alongside firewalls, conduct penetration testing, and document incidents to refine strategies for Secure Hardware Firewalls for Enterprises USA.
| Strategy | Tool/Method | Purpose |
|---|---|---|
| Real-Time Monitoring | SIEM (e.g., Splunk, IBM QRadar) | Detect and respond to threats instantly |
| Compliance Auditing | Automated scanners (e.g., Nessus) | Ensure adherence to regulatory standards |
| Performance Metrics | SNMP monitoring | Track latency and throughput issues |
More information of interest
What are the key features to consider when selecting a secure hardware firewall for an enterprise in the USA?
When selecting a secure hardware firewall for an enterprise in the USA, key features to consider include throughput capacity to handle network traffic without bottlenecks, advanced threat protection capabilities such as intrusion prevention and malware blocking, support for high availability and redundancy configurations, and compliance with industry standards like NIST frameworks to ensure robust security and regulatory adherence.
How does a hardware firewall enhance network security for large-scale enterprises compared to software solutions?
A hardware firewall enhances network security for large-scale enterprises by providing dedicated processing power, which reduces latency and avoids resource contention with other applications. It offers superior performance for high-traffic environments, supports complex access control policies at the network perimeter, and often includes integrated security features like VPN support and deep packet inspection, making it more scalable and reliable than software-based alternatives for enterprise use.
What are the compliance and regulatory considerations for deploying hardware firewalls in US enterprises?
Deploying hardware firewalls in US enterprises requires adherence to compliance and regulatory standards such as HIPAA for healthcare data, PCI DSS for payment card information, and FISMA for federal systems. Enterprises must ensure their firewall configurations enforce data protection, maintain audit trails, and support encryption standards to meet legal obligations and avoid penalties, while also aligning with guidelines from agencies like NIST or CISA for cybersecurity best practices.
How can enterprises ensure optimal performance and maintenance of their hardware firewalls?
Enterprises can ensure optimal performance and maintenance of their hardware firewalls by implementing regular firmware updates to address vulnerabilities, continuously monitoring traffic and logs for anomalies, configuring redundant setups for failover protection, and conducting periodic security audits. Additionally, training IT staff on firewall management and leveraging vendor support services helps maintain reliability and adapt to evolving threats.



Deja una respuesta