Secure Shared Hosting for Small Businesses
- Essential Security Features in Secure Shared Hosting for Small Businesses
- Comprehensive Guide to Secure Shared Hosting for Small Businesses
- What are the benefits of shared hosting for small businesses seeking cost-effective solutions?
- What security measures do shared hosting providers implement to protect small business websites?
- Which shared hosting providers offer the most robust security features for small business requirements?
- What security vulnerabilities should small businesses consider when using shared web hosting environments?
- More information of interest
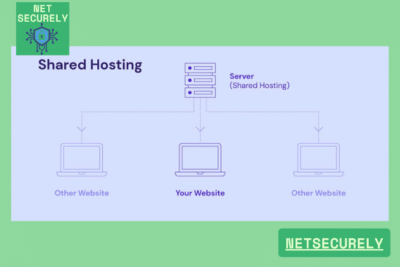
Secure Shared Hosting for Small Businesses, for small businesses seeking an online presence without the complexities of dedicated infrastructure, choosing the right hosting solution is critical. provides an accessible and cost-effective option, allowing multiple websites to operate on a single server while maintaining essential protections.
This approach balances affordability with key security measures—such as malware scanning, SSL certificates, and regular updates—to safeguard sensitive data and ensure reliable performance. By selecting a trusted provider, small enterprises can focus on growth, knowing their digital assets are protected against common threats in an increasingly interconnected landscape.
You may also be interested in reading: Secure Reseller Hosting for Web Designers
Secure Shared Hosting for Small Businesses incorporates multiple layers of protection to safeguard your online presence. This hosting solution combines robust security measures with cost-effective shared infrastructure, making it ideal for small businesses needing enterprise-grade protection without the enterprise price tag. Key security implementations include regular malware scanning, distributed denial-of-service (DDoS) protection, and automated backup systems. These features work collectively to ensure your business website remains protected against common cyber threats while maintaining optimal performance and reliability.
Core Security Protocols
Secure Shared Hosting for Small Businesses implements fundamental security protocols including SSL/TLS encryption, firewalls, and regular security patches. These protocols create a protective barrier between your website and potential threats, ensuring data integrity and confidentiality during transmission and storage.
Malware Protection and Scanning
Continuous malware scanning and automatic removal systems are integral to Secure Shared Hosting for Small Businesses. These systems proactively detect and neutralize malicious software before it can compromise your website's functionality or data security.
DDoS Mitigation Strategies
Distributed Denial of Service protection is built into Secure Shared Hosting for Small Businesses, employing advanced traffic filtering and rate limiting techniques to prevent service disruptions and maintain website availability during attack attempts.
Backup and Recovery Systems
Automated backup solutions within Secure Shared Hosting for Small Businesses ensure regular data preservation with point-in-time recovery options, providing business continuity assurance in case of data loss or corruption incidents.
Compliance and Data Protection
Secure Shared Hosting for Small Businesses adheres to industry compliance standards, implementing data protection measures that meet regulatory requirements for customer information security and privacy preservation.
| Security Feature | Implementation | Business Benefit |
| SSL Certificates | Automated installation and renewal | Encrypted data transmission and trust indicators |
| Firewall Protection | Network and application layer filtering | Prevents unauthorized access attempts |
| Malware Scanning | Daily automated scans | Early threat detection and removal |
| Automated Backups | Daily incremental backups | Data recovery capability |
| DDoS Protection | Real-time traffic monitoring | Service availability maintenance |

Shared hosting offers small businesses several key advantages when seeking cost-effective web solutions, primarily through significant cost savings as server resources and maintenance expenses are distributed among multiple users, while still providing essential features like standard security measures, automated backups, and technical support, making it an accessible entry point for establishing an online presence without substantial upfront investment, including options for Secure Shared Hosting for Small Businesses that ensure basic protection while maintaining affordability.
Cost Efficiency and Budget Management
Shared hosting is exceptionally cost-effective for small businesses as it allows multiple websites to utilize a single server, drastically reducing operational expenses compared to dedicated or VPS hosting; this model includes maintenance, security updates, and technical support within a low monthly fee, often starting under $10, enabling businesses to allocate funds to other critical areas like marketing or product development while maintaining a professional online presence.
Ease of Use and Technical Support
This hosting type is designed for user-friendliness, featuring intuitive control panels such as cPanel or Plesk that simplify website management, domain setup, and email configuration without requiring advanced technical skills; moreover, providers typically offer 24/7 customer support and comprehensive knowledge bases, ensuring that small business owners can resolve issues quickly and focus on their core operations rather than server administration.
Scalability and Feature Availability
While shared hosting has resource limitations, it provides scalable options that allow businesses to start with basic plans and upgrade as their traffic and needs grow, often including one-click installers for popular applications like WordPress, e-commerce platforms, and marketing tools; key features such as SSL certificates, email accounts, and automated backups are commonly bundled, offering a balanced mix of functionality and affordability for growing enterprises.
| Feature | Benefit | Typical Inclusion |
|---|---|---|
| Storage Space | Adequate for small to medium sites | 10GB - 100GB |
| Bandwidth | Supports moderate traffic levels | Unmetered or generous limits |
| Email Accounts | Professional communication | 5 - Unlimited |
| SSL Certificate | Basic security and trust | Free with most plans |
| Backups | Data protection | Weekly automated |

Shared hosting providers implement a multi-layered security approach to protect small business websites, including firewalls and intrusion detection systems to monitor and block malicious traffic, regular software updates for server operating systems and control panels to patch vulnerabilities, DDoS protection to mitigate large-scale attacks, malware scanning and removal tools to identify threats, secure FTP and SSH access with encryption protocols, account isolation techniques to prevent cross-site contamination, automated backups for data recovery, and SSL certificate support to ensure encrypted data transmission, all contributing to a robust Secure Shared Hosting for Small Businesses environment.
Network-Level Security Measures
Shared hosting providers deploy comprehensive network security measures including hardware firewalls that filter incoming and outgoing traffic based on predefined rules, intrusion prevention systems (IPS) to actively block potential threats, and DDoS mitigation services that absorb malicious traffic before it reaches servers. These systems operate 24/7 to detect anomalies such as brute force attacks or suspicious IP addresses, with many providers using cloud-based security platforms that scale protection dynamically. Additionally, network segmentation isolates customer accounts to prevent lateral movement in case of a breach, while real-time monitoring tools alert security teams to any unusual activity, ensuring prompt response to potential network threats.
Server and Application Protection
Providers secure server infrastructure through hardened operating systems with minimal unnecessary services, regular security patches applied automatically to close vulnerabilities, and web application firewalls (WAF) that filter HTTP traffic for threats like SQL injection or cross-site scripting. Server-level malware scanners perform scheduled and on-demand checks on files, while mod_security rulesets provide tailored protection for applications like WordPress or Joomla. Access controls include SSH key authentication instead of passwords where possible, and permission hardening to restrict file editing capabilities. The following table summarizes key application protection features:
| Feature | Description | Frequency |
|---|---|---|
| Automatic Patching | Updates for OS, PHP, MySQL | Daily/Weekly |
| Malware Scanning | Filesystem checks for threats | Daily |
| WAF Rulesets | Block common exploit patterns | Real-time |
| Brute Force Protection | Limit login attempts | Continuous |
Data Security and Backup Systems
Data protection involves encryption protocols like TLS 1.3 for data in transit and disk encryption for data at rest on servers, coupled with secure backup storage in geographically separate locations with restricted access. Providers implement automated backup schedules (typically daily or weekly) with retention policies allowing point-in-time recovery, while redundant storage arrays prevent data loss from hardware failures. Customers often receive tools to initiate manual backups or restore points through control panels, with some services offering versioning to recover previous file states. All backup transfers and storage utilize encrypted channels to prevent interception, and compliance with standards like GDPR or PCI DSS is maintained where applicable.

Several shared hosting providers offer strong security features for small businesses, with SiteGround, A2 Hosting, and InMotion Hosting standing out for their comprehensive measures including free SSL certificates, automated daily backups, malware scanning, and advanced Web Application Firewalls (WAF); these providers ensure reliable protection, making them ideal choices for Secure Shared Hosting for Small Businesses seeking to safeguard their online presence without incurring high costs.
Key Security Features to Look For
When evaluating Secure Shared Hosting for Small Businesses, prioritize providers that include free SSL certificates to encrypt data, automated daily backups for quick recovery, malware scanning and removal tools, and a robust Web Application Firewall (WAF) to block threats; additional features like two-factor authentication (2FA) and DDoS protection further enhance security, ensuring comprehensive defense against common vulnerabilities and attacks.
Top Providers and Their Security Offerings
Among the leading options, SiteGround provides a custom WAF, daily backups, and AI anti-bot system; A2 Hosting includes free HackScan protection and reinforced DDoS defense; and InMotion Hosting offers SSL, automatic backups, and malware detection. These providers deliver a balanced mix of proactive and reactive security measures, making them suitable for small businesses needing reliable protection without dedicated server costs.
| Provider | Key Security Features | Ideal For |
|---|---|---|
| SiteGround | Custom WAF, Daily Backups, Free SSL | E-commerce and high-traffic sites |
| A2 Hosting | HackScan, DDoS Protection, SSL | Performance-focused businesses |
| InMotion Hosting | Malware Detection, Backups, Free SSL | General small business websites |
Comparing Costs and Value
The investment in Secure Shared Hosting for Small Businesses varies, with providers like SiteGround starting at higher tiers but including more advanced security, while A2 Hosting and InMotion offer competitive pricing with essential features; it is crucial to assess the cost-to-value ratio, ensuring that security tools like firewalls, backups, and SSL certificates are included without hidden fees, providing affordable yet robust protection for limited budgets.
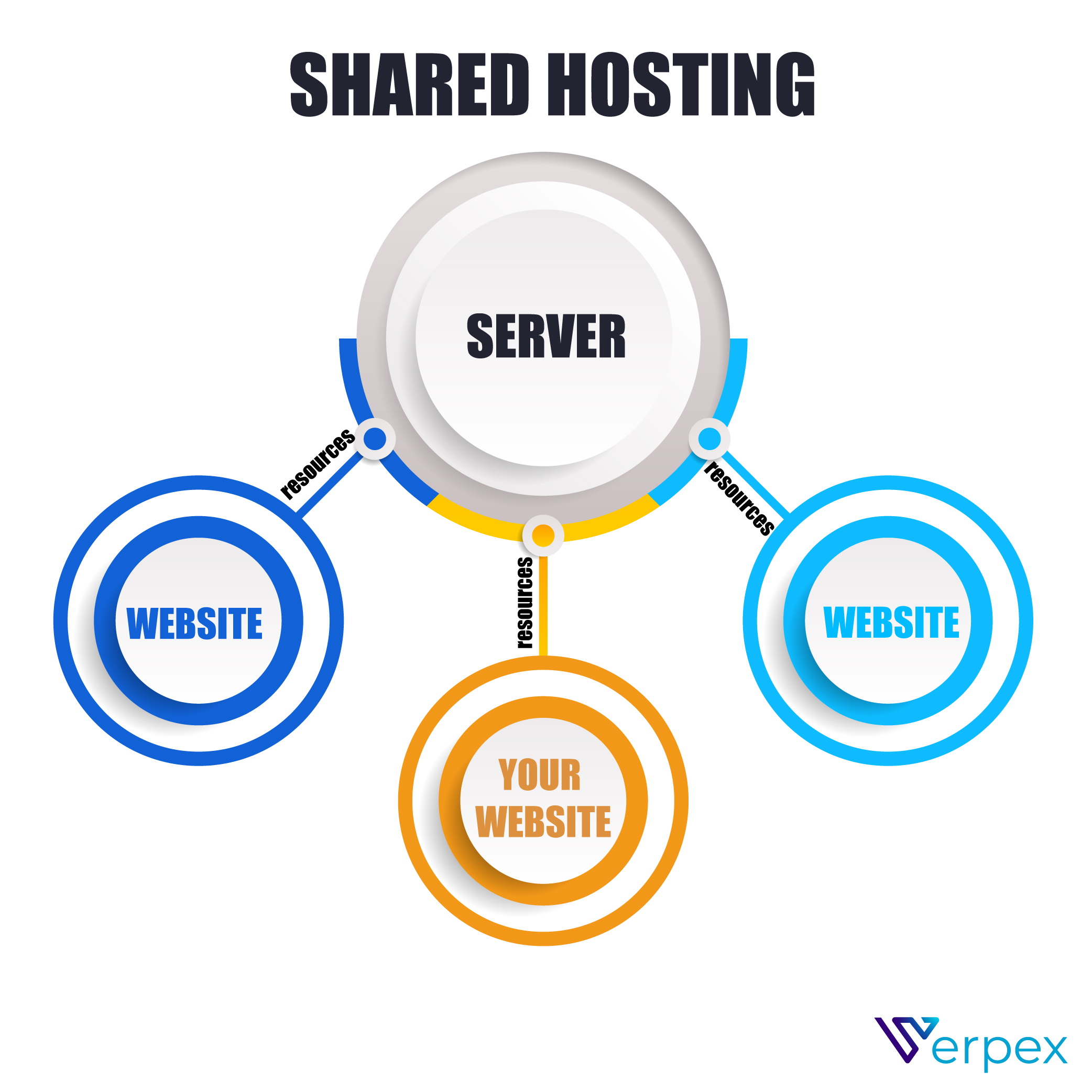
Small businesses using shared web hosting environments should consider multiple security vulnerabilities, including cross-site contamination where malware from other sites on the same server can spread, shared resource limitations leading to potential denial-of-service attacks affecting all users, inadequate isolation between client accounts allowing unauthorized access to sensitive data, and outdated software on the server that exposes all hosted sites to known exploits; additionally, weak access controls and insufficient encryption for data transmission further heighten risks, making it essential to prioritize Secure Shared Hosting for Small Businesses with proactive security measures and regular monitoring to mitigate these threats.
Cross-Site Contamination Risks
In shared hosting, cross-site contamination is a critical vulnerability where a compromised website on the same server can infect others through shared resources, such as directories or databases; attackers may exploit weak permissions or malicious scripts to spread malware, leading to data breaches or service disruptions for all tenants, underscoring the need for robust isolation and monitoring in Secure Shared Hosting for Small Businesses.
Inadequate Access Controls and Permissions
Weak access controls in shared environments often result from improper file permissions or misconfigured user roles, allowing unauthorized users to view, modify, or delete sensitive data from other accounts; this risk is exacerbated if hosting providers do not enforce strict segregation, making it vital for businesses to regularly audit permissions and implement strong authentication mechanisms to protect their assets.
| Common Access Control Issues | Potential Impact | Mitigation Strategies |
|---|---|---|
| Overly permissive file permissions (e.g., 777) | Unauthorized data access or alteration | Set strict permissions (e.g., 755 for directories, 644 for files) |
| Shared database users with broad privileges | Cross-account data leakage | Use unique database credentials and limit privileges |
| Default or weak admin passwords | Full server compromise | Enforce strong, unique passwords and multi-factor authentication |
Outdated Software and Patch Management
Shared hosting servers often run outdated software, including operating systems, control panels (e.g., cPanel), or applications (e.g., PHP, MySQL), which contain known vulnerabilities that attackers can exploit to gain access to multiple sites; since businesses rely on the provider for updates, delays in patching can leave all tenants exposed, highlighting the importance of choosing a host with a rigorous and timely patch management policy.
More information of interest
Our secure shared hosting for small businesses includes multiple layers of protection, such as firewalls, malware scanning, and DDoS mitigation. We also provide SSL certificates to encrypt data and ensure secure transactions, along with regular security updates to keep your site safe from vulnerabilities.
We maintain strict data privacy through isolated environments and access controls, ensuring that your business information remains confidential. Our hosting infrastructure includes encrypted backups and compliance with data protection regulations to safeguard sensitive customer and business data.
Can I scale my hosting plan as my business grows?
Yes, our shared hosting plans are designed with scalability in mind, allowing you to upgrade resources such as storage, bandwidth, and processing power seamlessly. This ensures your hosting can grow alongside your business without downtime or migration hassles.
What support is available if I encounter security issues?
Our 24/7 technical support team is trained to handle security-related concerns promptly, providing assistance with issues like malware removal, breach investigations, and preventative measures. We also offer a knowledge base with guides on best security practices for small businesses.





Deja una respuesta