
Secure Software Firewalls for Network Defense

- Implementing Secure Software Firewalls for Network Defense
- Secure Software Firewalls for Network Defense: A Comprehensive Guide
- Which firewall solutions are commonly implemented by the Department of Defense for network defense purposes?
- How do software-based firewalls differ from hardware-based network firewalls in terms of deployment and functionality?
- What are the three primary classifications of firewalls used in modern networking environments?
- More information of interest
Secure Software Firewalls for Network Defense, in today's interconnected digital landscape, robust network security mechanisms are essential to protect sensitive data and systems from evolving cyber threats. A critical component of modern cybersecurity strategies is the implementation of .
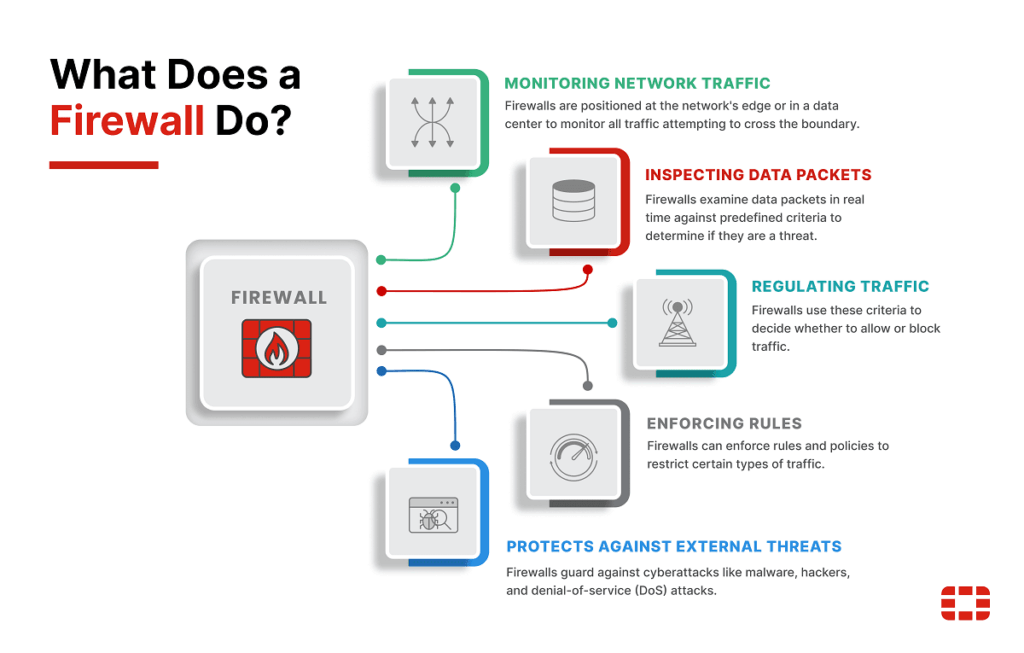
These solutions provide dynamic, application-layer filtering and monitoring capabilities that go beyond traditional hardware-based approaches. By enabling granular control over inbound and outbound traffic, they help organizations prevent unauthorized access, detect anomalies, and mitigate potential breaches in real time. As cyberattacks grow in sophistication, deploying advanced becomes indispensable for maintaining resilient and proactive security postures across diverse IT environments.
You may be interested in reading: Best VPNs for Corporate Network Security USA
Implementing Secure Software Firewalls for Network Defense
Secure Software Firewalls for Network Defense are critical components in modern cybersecurity infrastructure, providing granular control over network traffic and protecting systems from unauthorized access. These software-based solutions operate at various levels of the network stack, offering customizable security policies that can be tailored to specific organizational needs. Unlike hardware firewalls, software firewalls provide flexibility in deployment and can be implemented on individual endpoints, servers, or virtual environments, making them essential for distributed networks and cloud-based infrastructures.
Core Functionality and Architecture
Secure software firewalls operate by examining data packets against predefined security rules, determining whether to allow or block traffic based on source/destination IP addresses, ports, and protocols. Modern implementations include stateful inspection capabilities that track active connections and context-aware filtering that evaluates application-layer data.
The architecture typically consists of a rule management interface, packet filtering engine, and logging/reporting modules, all designed to work cohesively while maintaining system performance and stability.
Deployment Strategies and Best Practices
Effective deployment involves strategic placement at network perimeter points, between network segments, and on critical servers. Best practices include implementing the principle of least privilege, where only essential traffic is permitted, and regularly updating rule sets to address emerging threats. Organizations should segment networks and apply zone-based policies, ensuring that even if one segment is compromised, the firewall prevents lateral movement across the network.
Advanced Threat Prevention Features
Modern secure software firewalls incorporate advanced features such as intrusion prevention systems (IPS), deep packet inspection (DPI), and threat intelligence integration. These capabilities enable real-time detection and blocking of sophisticated attacks, including zero-day exploits and advanced persistent threats. Many solutions also offer sandboxing functionality to analyze suspicious files in isolated environments before they reach critical systems.
Performance Optimization and Management
Optimizing firewall performance requires careful configuration tuning, regular rule base audits to remove redundant rules, and implementing efficient logging practices. Centralized management consoles allow administrators to maintain consistent policies across multiple firewalls, while automated reporting tools provide visibility into traffic patterns and security events. Performance monitoring should include tracking CPU/memory usage and network latency impacts.
Integration with Security Ecosystems
Secure software firewalls achieve maximum effectiveness when integrated with other security components such as SIEM systems, endpoint protection platforms, and threat intelligence feeds. This integration enables coordinated responses to security incidents and provides comprehensive visibility across the entire security infrastructure. API-based integrations allow for automated policy updates and real-time threat response coordination.
| Firewall Type | Deployment Scope | Key Features | Use Cases |
| Host-based | Individual endpoints | Application control, process monitoring | Workstation protection, BYOD security |
| Network-based | Network segments | Traffic filtering, VPN support | Perimeter defense, inter-zone security |
| Cloud-native | Cloud environments | Scalability, API integration | Cloud workload protection, SaaS security |
| Virtual | Virtualized infrastructure | Hypervisor integration, micro-segmentation | Data center security, VM protection |
Secure Software Firewalls for Network Defense: A Comprehensive Guide
Which firewall solutions are commonly implemented by the Department of Defense for network defense purposes?

The Department of Defense primarily utilizes Palo Alto Networks firewalls, particularly the PA-Series models, which offer advanced threat prevention and deep packet inspection capabilities, alongside Cisco firewalls such as the ASA and Firepower series for their robust security features and integration with existing network infrastructure.
Additionally, Fortinet FortiGate solutions are widely deployed for their high-performance throughput and comprehensive security fabric, while specialized Secure Software Firewalls for Network Defense are also employed to protect specific assets and segments within DoD networks, ensuring compliance with strict security protocols like the DoDIN APL (Approved Products List) and alignment with frameworks such as Zero Trust architecture.
Primary Hardware Firewall Solutions
The DoD relies heavily on hardware-based firewall solutions from leading vendors to safeguard its extensive network infrastructure. Palo Alto Networks PA-Series firewalls are extensively used for their App-ID and Threat Prevention capabilities, enabling granular control and real-time threat mitigation. Cisco Firepower and ASA devices are also common, providing integrated intrusion prevention and advanced malware protection. These solutions are selected for their ability to handle high-volume traffic while enforcing strict access policies aligned with DoD security standards, ensuring robust perimeter defense and segmentation within military networks.
Deployment Strategies and Configurations
Deployment of firewalls within the DoD involves a layered defense strategy, incorporating both perimeter and internal segmentation firewalls to minimize attack surfaces. Configurations are rigorously designed to enforce least privilege access and adhere to the Zero Trust model, with rulesets based on mission requirements and security classifications. Regular updates and continuous monitoring are mandated, often integrated with Security Information and Event Management (SIEM) systems for comprehensive visibility and rapid incident response, ensuring alignment with DoD Instruction 8510.01 for risk management.
Compliance and Certification Requirements
All firewall solutions implemented by the DoD must meet stringent compliance and certification standards, including inclusion on the DoDIN APL and validation against Common Criteria and FIPS 140-2 for cryptographic modules. These firewalls are configured to support STIGs (Security Technical Implementation Guides) to harden devices against vulnerabilities, and they must facilitate auditing and logging in accordance with DoD Directive 8140.01. This ensures that every deployed firewall not only provides robust security but also aligns with federal regulations and DoD-specific cybersecurity policies.
| Firewall Vendor | Common Models | Key Features | DoD Compliance |
|---|---|---|---|
| Palo Alto Networks | PA-5200, PA-3200 Series | App-ID, Threat Prevention, WildFire | DoDIN APL, FIPS 140-2 |
| Cisco | Firepower 4100, ASA 5500-X | IPS, AMP, VPN Support | Common Criteria, STIGs |
| Fortinet | FortiGate 6000, 4000 Series | High Throughput, Security Fabric | DoDIN APL, FIPS 140-2 |
How do software-based firewalls differ from hardware-based network firewalls in terms of deployment and functionality?

Software-based firewalls are deployed as applications on individual endpoints or servers, utilizing the host's resources to filter traffic based on predefined rules, offering granular control at the device level but potentially impacting system performance, while hardware-based network firewalls are standalone physical devices positioned at network perimeters, operating independently to inspect and filter all incoming and outgoing traffic without consuming host resources, providing broader network-wide protection with dedicated processing power for higher throughput and lower latency.
Deployment Methodologies
Software-based firewalls are installed directly on individual devices such as workstations, servers, or mobile endpoints, integrating with the operating system to monitor and control traffic at the application level, allowing for customized policies per device but requiring maintenance on each installation, whereas hardware-based firewalls are deployed as dedicated appliances at strategic network chokepoints like between routers and switches, functioning as autonomous gateways that filter all traffic traversing network segments without relying on endpoint resources, making them ideal for perimeter defense and centralized management.
Functional Capabilities and Performance
In terms of functionality, software firewalls excel at providing application-layer filtering and user-specific rules, enabling deep packet inspection for processes on the host, which is crucial for defending against malware or unauthorized data exfiltration, but they may suffer from performance overhead on the host system; hardware firewalls, by contrast, specialize in high-speed packet filtering, stateful inspection, and handling large volumes of traffic with dedicated processors, offering superior throughput and latency for entire networks without affecting endpoint performance, though they may lack granular user-application visibility without additional integration.
Resource Utilization and Scalability
Software firewalls consume CPU, memory, and storage resources from their host devices, which can lead to performance degradation on older or resource-constrained systems, and scaling requires deploying and configuring the firewall on each new device individually, whereas hardware firewalls operate with their own dedicated resources, ensuring consistent performance unaffected by endpoint loads, and they scale more efficiently for growing networks by upgrading appliance capacity or adding additional units, though at a higher initial cost and with more complex infrastructure changes.
| Aspect | Software-Based Firewall | Hardware-Based Firewall |
|---|---|---|
| Deployment Location | Installed on endpoints/servers | Physical device at network edge |
| Resource Dependency | Uses host system resources | Dedicated processing/memory |
| Traffic Scope | Device-level traffic only | Network-wide traffic inspection |
| Performance Impact | Potential system slowdown | No endpoint performance loss |
| Scalability Approach | Per-device installation | Appliance upgrade or addition |
| Key Use Case | Secure Software Firewalls for Network Defense on specific hosts | Enterprise perimeter protection |
What are the three primary classifications of firewalls used in modern networking environments?
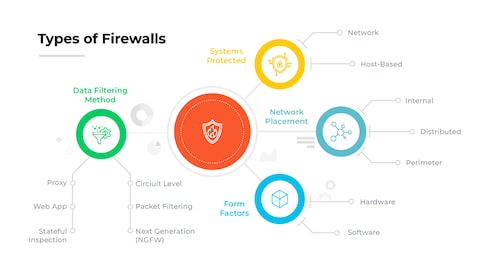
The three primary classifications of firewalls used in modern networking environments are packet-filtering firewalls, stateful inspection firewalls, and application-layer firewalls. Packet-filtering firewalls operate at the network layer by examining individual packets based on predefined rules such as source and destination IP addresses, ports, and protocols, providing basic but efficient traffic control. Stateful inspection firewalls, which function at the network and transport layers, track the state of active connections and make decisions based on the context of the traffic, offering enhanced security by monitoring sessions rather than isolated packets.
Application-layer firewalls, also known as proxy firewalls, operate at the application layer to inspect and filter traffic based on specific applications or services, providing deep packet inspection and the ability to enforce advanced security policies; these are a key component of secure software firewalls for network defense, as they can understand and control complex application behaviors.
Packet-Filtering Firewalls
Packet-filtering firewalls are the most fundamental type, operating at Layer 3 (Network Layer) and sometimes Layer 4 (Transport Layer) of the OSI model. They examine each packet's header information, such as source IP, destination IP, protocol type (e.g., TCP, UDP), and port numbers, and compare it against a set of predefined rules to allow or block traffic.
While efficient and low-latency due to their simplicity, they lack context awareness, making them vulnerable to certain attacks like IP spoofing or those exploiting allowed ports. They are commonly implemented in routers and are suitable for basic perimeter defense where high performance is prioritized over deep inspection.
| Key Feature | Description |
|---|---|
| Operating Layer | Network Layer (L3) and Transport Layer (L4) |
| Inspection Basis | Packet headers (IP addresses, ports, protocols) |
| Advantages | High speed, low resource usage |
| Limitations | No state tracking, vulnerable to advanced threats |
Stateful Inspection Firewalls
Stateful inspection firewalls enhance security by operating at Layer 3 and Layer 4 while maintaining awareness of the state of active connections. Unlike packet filters, they track the context of traffic, such as whether a packet is part of an established session, by storing connection information in a state table. This allows them to make more intelligent decisions, such as dynamically allowing response traffic for outgoing requests without needing explicit rules for return packets. They provide better protection against certain attacks like unauthorized access attempts masquerading as legitimate traffic, though they still do not inspect application-layer data deeply.
| Key Feature | Description |
|---|---|
| Operating Layer | Network and Transport Layers (L3-L4) |
| Inspection Basis | Packet headers and connection state (state table) |
| Advantages | Context-aware, better security than packet filters |
| Limitations | Limited application-layer insight |
Application-Layer Firewalls
Application-layer firewalls, also known as proxy firewalls, operate at Layer 7 (Application Layer) of the OSI model. They perform deep packet inspection by analyzing the actual content of the traffic, such as HTTP requests or FTP commands, to enforce granular security policies based on applications or services. By acting as an intermediary between end-users and servers, they can filter malicious content, prevent data leakage, and provide detailed logging. While offering the highest level of security, they introduce more latency and require greater computational resources, making them ideal for environments where application-specific threats are a concern.
| Key Feature | Description |
|---|---|
| Operating Layer | Application Layer (L7) |
| Inspection Basis | Full packet payload and application data |
| Advantages | Granular control, advanced threat prevention |
| Limitations | Higher latency, resource-intensive |
More information of interest
What is a secure software firewall and how does it enhance network defense?
A secure software firewall is a program that monitors and controls incoming and outgoing network traffic based on predetermined security rules, providing a critical layer of protection against unauthorized access and cyber threats by filtering data packets at the application or operating system level.
What are the key features to look for in a secure software firewall?
Essential features include real-time monitoring, customizable rule sets, intrusion detection and prevention capabilities, application-level filtering, and regular security updates to defend against evolving threats and ensure robust network security.
How does a software firewall differ from a hardware firewall?
While both provide network security, a software firewall is installed directly on individual devices, offering granular control over application traffic, whereas a hardware firewall is a physical device that protects the entire network at the perimeter, with software firewalls providing an additional defense layer for endpoints.
Can a software firewall alone provide complete network security?
No, a software firewall is a critical component but should be part of a layered security strategy that includes antivirus software, regular patching, employee training, and other measures to address diverse threats and vulnerabilities comprehensively.

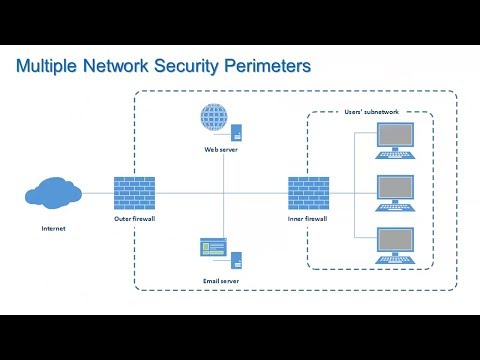





Deja una respuesta