Top Firewalls with IDS for Networks in USA

- Top Firewalls with IDS for Networks in USA
- Top Firewalls with IDS for Networks in USA: A Detailed Guide
- More information of interest
- What are the top firewalls with IDS for enterprise networks in the USA?
- How do integrated IDS features enhance network security in firewalls?
- What criteria should be considered when selecting a firewall with IDS for US-based networks?
- Are there any open-source firewall options with IDS suitable for US networks?
Top Firewalls with IDS for Networks in USA, in today's increasingly complex cybersecurity landscape, American organizations require robust protection mechanisms to safeguard their network infrastructures. The integration of Intrusion Detection Systems (IDS) with firewalls has become a critical strategy for defending against sophisticated threats. This article explores the , examining solutions that combine deep packet inspection, real-time monitoring, and automated response capabilities.
These advanced security appliances provide comprehensive threat visibility while maintaining regulatory compliance, making them essential components for enterprises operating across various sectors. We analyze key features, deployment considerations, and performance metrics to help security professionals make informed decisions about their network defense strategies.
You may also be interested in reading: Best Cloud Hosting for E-Commerce Platforms
Top Firewalls with IDS for Networks in USA
When evaluating the Top Firewalls with IDS for Networks in USA, it is essential to consider factors such as detection accuracy, ease of integration, scalability, and compliance with U.S. regulatory standards like NIST and FIPS. These solutions are designed to protect against sophisticated threats while ensuring minimal false positives and seamless network performance. Key features often include real-time monitoring, automated threat response, and comprehensive reporting capabilities tailored for enterprise and government use.
Key Features of Leading Firewalls with IDS
Leading firewalls with IDS offer advanced features such as deep packet inspection, behavioral analysis, and signature-based detection to identify and mitigate threats. Integration with threat intelligence feeds enhances their ability to recognize emerging attacks, while customizable policies allow organizations to align security measures with specific network architectures and compliance requirements in the USA.
Performance and Scalability Considerations
Performance metrics, including throughput, latency, and concurrent connection handling, are critical for selecting a firewall with IDS. Scalability ensures the solution can grow with network demands, supporting everything from small businesses to large enterprises without compromising security efficacy or operational efficiency.
Regulatory Compliance and Standards
Compliance with U.S. standards such as NIST, FIPS, and sector-specific regulations (e.g., HIPAA for healthcare) is a priority. Top firewalls with IDS provide built-in compliance reporting and audit trails, facilitating adherence to legal and security frameworks required for networks operating in the USA.
Integration with Existing Infrastructure
Seamless integration with existing network components, such as SIEM systems, endpoints, and cloud services, is essential. The best solutions offer APIs, support for standard protocols, and interoperability with multi-vendor environments to ensure cohesive security management.
Vendor Support and Total Cost of Ownership
Evaluating vendor support, including updates, patches, and technical assistance, alongside licensing models and maintenance costs, helps determine the total cost of ownership. Reliable support and transparent pricing are key for long-term deployment success.
| Firewall Model | IDS Capabilities | Max Throughput | Compliance Support |
| Cisco Firepower | Next-gen IPS, Snort-based | 20 Gbps | NIST, FIPS, HIPAA |
| Palo Alto Networks | Threat Prevention, App-ID | 50 Gbps | NIST, FIPS, GDPR |
| FortiGate | FortiGuard IPS, AI-driven | 100 Gbps | NIST, FIPS, PCI DSS |
| Check Point | ThreatCloud IPS | 30 Gbps | NIST, FIPS, SOX |
| Juniper SRX | Junipers IDP, signature/anomaly | 40 Gbps | NIST, FIPS, ISO 27001 |
Top Firewalls with IDS for Networks in USA: A Detailed Guide
How do modern firewalls incorporate integrated Intrusion Detection Systems (IDS) capabilities?
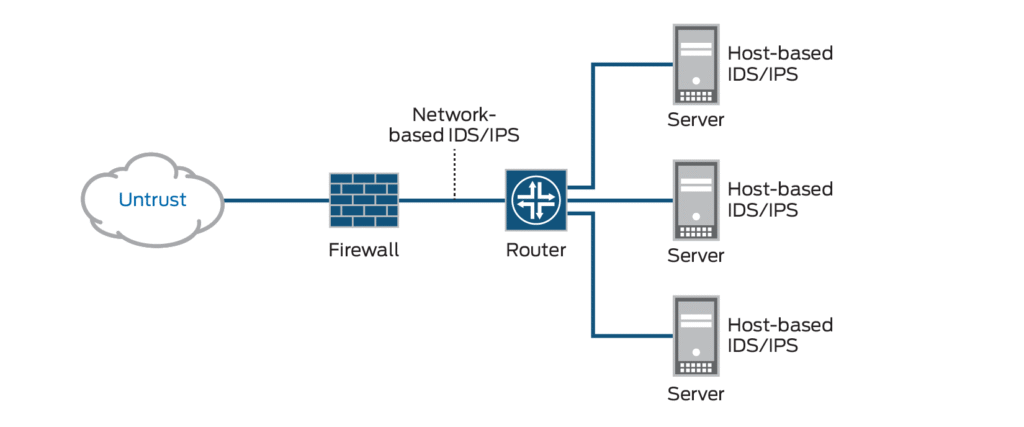
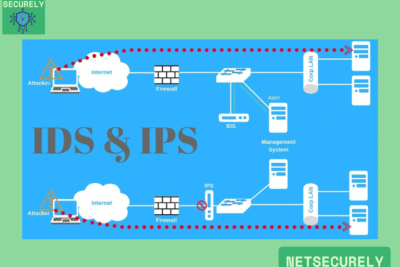
Modern firewalls incorporate integrated Intrusion Detection Systems (IDS) capabilities by embedding deep packet inspection (DPI) engines that analyze network traffic in real-time, comparing it against a database of known attack signatures and behavioral anomalies to identify potential threats; these systems utilize machine learning algorithms and heuristic analysis to detect zero-day exploits and sophisticated attacks, while also enabling automated responses such as blocking malicious IP addresses or terminating suspicious sessions to enhance network security without requiring separate hardware or software installations.
Signature-Based Detection Integration
Signature-based detection in modern firewalls involves scanning network packets for predefined patterns or signatures associated with known threats, such as malware or exploit codes; this method relies on regularly updated databases from security vendors to ensure accuracy, and when a match is found, the firewall can log the event, alert administrators, or automatically block the traffic, providing a foundational layer of protection against well-documented attacks while integrating seamlessly with other security features.
Anomaly-Based Behavioral Analysis
Anomaly-based behavioral analysis in integrated IDS firewalls monitors network traffic for deviations from established baselines of normal activity, using statistical models and machine learning to identify unusual patterns that may indicate novel threats or insider attacks; this approach allows for the detection of zero-day exploits and sophisticated attacks that lack known signatures, with the firewall capable of dynamically adjusting policies or triggering alerts based on real-time behavioral insights, enhancing proactive defense mechanisms.
Automated Response and Threat Mitigation
Automated response capabilities in firewalls with integrated IDS enable immediate actions upon threat detection, such as quarantining affected devices, blocking IP addresses, or terminating connections to prevent damage; these responses are configurable through policies that balance security and operational continuity, often incorporating feedback loops to refine accuracy over time, and are critical for reducing the window of exposure in fast-moving cyber incidents, making them a key feature in Top Firewalls with IDS for Networks in USA.
| Feature | Description | Benefit |
|---|---|---|
| Real-Time Monitoring | Continuously analyzes traffic for threats | Immediate threat detection and response |
| Signature Updates | Regular database refreshes from vendors | Protection against latest known threats |
| Behavioral Baselines | Establishes normal network activity patterns | Detects anomalies and unknown attacks |
| Automated Blocking | Instantly blocks malicious IPs or sessions | Reduces manual intervention and risk |
Which Intrusion Detection Systems are considered most effective for network security in the United States?
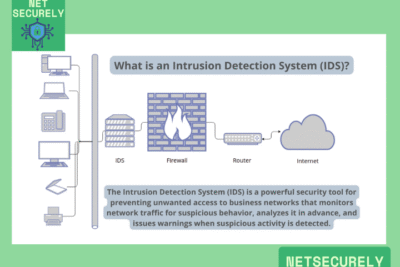
In the United States, the most effective intrusion detection systems typically include Snort, an open-source network-based IDS renowned for its flexibility and extensive rule sets; Suricata, which offers high-performance multi-threading and robust protocol analysis; and commercial solutions like Cisco's Firepower Next-Generation Intrusion Prevention System (NGIPS), which integrates advanced threat intelligence and behavioral analytics. Additionally, Palo Alto Networks' Threat Prevention and Check Point's Intrusion Prevention System (IPS) are widely adopted for their deep integration with next-generation firewalls, providing comprehensive visibility and automated responses. These systems are often considered top-tier due to their ability to detect anomalies, signature-based threats, and zero-day exploits, with many organizations opting for a hybrid approach combining both network-based (NIDS) and host-based (HIDS) solutions like OSSEC or Security Onion for layered defense. Among the Top Firewalls with IDS for Networks in USA, these platforms stand out for their scalability, real-time monitoring, and compliance with standards like NIST frameworks.
Snort as a Leading Open-Source IDS
Snort is highly regarded for its open-source nature, allowing extensive customization and community-driven rule sets that adapt to emerging threats. It functions as a lightweight network intrusion detection and prevention system, capable of performing real-time traffic analysis and packet logging. Snort's effectiveness stems from its signature-based detection, protocol analysis, and content matching, making it a staple in many U.S. organizational networks for its cost-efficiency and reliability in identifying known vulnerabilities.
Commercial IDS Solutions: Cisco Firepower and Palo Alto Networks
Commercial IDS solutions like Cisco Firepower NGIPS and Palo Alto Networks' Threat Prevention are prioritized for their integration with broader security architectures, offering advanced features such as encrypted traffic analysis, sandboxing, and AI-driven threat intelligence. These systems provide centralized management, detailed reporting, and automated response mechanisms, aligning with compliance requirements and reducing the burden on security teams. Their ability to correlate events across networks and endpoints makes them effective for large-scale deployments in the U.S.
Hybrid and Next-Generation IDS Approaches
Modern effective IDS strategies often combine network-based and host-based systems, leveraging tools like Suricata for high-speed network monitoring and OSSEC for endpoint visibility. This hybrid approach enhances detection accuracy by cross-referencing data from multiple layers, addressing both perimeter and internal threats. Next-generation IDS solutions emphasize behavioral analytics and machine learning to identify zero-day attacks, reducing false positives and improving proactive defense measures in complex U.S. network environments.
| System | Type | Key Feature | Common Use Case |
|---|---|---|---|
| Snort | Open-Source NIDS | Customizable rule sets | SMBs and educational institutions |
| Suricata | Open-Source NIDS | Multi-threading performance | High-traffic enterprise networks |
| Cisco Firepower | Commercial NGIPS | Integrated threat intelligence | Large corporations and government |
| Palo Alto Threat Prevention | Commercial IDS/IPS | Deep learning analytics | Financial and healthcare sectors |
Does Palo Alto Networks offer IDS or IPS functionality within their firewall solutions?
Palo Alto Networks Next-Generation Firewalls incorporate both Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) functionalities through their advanced threat prevention capabilities, which include a robust intrusion prevention engine that analyzes network traffic for known vulnerabilities, malware, and attack patterns using regularly updated signatures and behavioral analytics; this integrated approach allows organizations to either monitor and log suspicious activities (IDS mode) or actively block potential threats in real-time (IPS mode) based on customized security policies, making their firewalls a comprehensive solution for network security that aligns with modern threat landscapes.
How Palo Alto Networks Implements IDS and IPS
Palo Alto Networks integrates IDS and IPS functionalities directly into their Next-Generation Firewalls through the Threat Prevention subscription service, which leverages a combination of signature-based detection, protocol analysis, and behavioral heuristics to identify and mitigate threats; the system uses regularly updated threat intelligence from Unit 42 research to ensure coverage against emerging vulnerabilities, and administrators can fine-tune policies to operate in either detection-only or prevention mode based on their security posture requirements, providing flexibility without compromising on depth of inspection or performance.
Key Features of Palo Alto Networks IDS/IPS Capabilities
The IDS and IPS features in Palo Alto Networks firewalls include application-aware inspection, which allows the system to enforce security policies based on specific applications rather than just ports and protocols, alongside SSL decryption for encrypted traffic analysis, custom signature creation for tailored threat detection, and automated response actions through dynamic policy enforcement; these features are complemented by detailed logging and reporting tools within the Panorama management platform, enabling comprehensive visibility and control over network threats, and positioning these solutions among the Top Firewalls with IDS for Networks in USA due to their scalability and advanced threat coverage.
Comparison of Palo Alto Networks IPS with Traditional Systems
Palo Alto Networks' IPS functionality surpasses traditional standalone systems by offering deeply integrated, context-aware prevention that correlates threat data with user identity, application usage, and content type to reduce false positives and increase accuracy; unlike legacy IPS solutions that often operate as separate network appliances, Palo Alto's implementation is woven into the firewall's single-pass architecture, ensuring efficient processing without significant latency. The table below highlights some key distinctions:
| Aspect | Palo Alto Networks IPS | Traditional IPS |
|---|---|---|
| Integration | Built into NGFW with unified policy management | Often a separate appliance or software |
| Traffic Inspection | Application and user-aware with SSL decryption | Primarily signature-based on ports/protocols |
| Threat Intelligence | Dynamic updates from Unit 42 global research | Relies on generic vendor signatures |
| Performance Impact | Low due to single-pass processing | Can introduce higher latency |
More information of interest
What are the top firewalls with IDS for enterprise networks in the USA?
Palo Alto Networks, Cisco Firepower, Fortinet FortiGate, and Check Point Quantum are widely regarded as the leading enterprise firewalls with integrated Intrusion Detection System (IDS) capabilities in the USA. These solutions offer advanced threat detection, deep packet inspection, and real-time monitoring, making them ideal for securing large-scale networks against sophisticated cyber threats.
How do integrated IDS features enhance network security in firewalls?
Integrated IDS features enhance network security by providing real-time monitoring, anomaly detection, and automated threat response. These systems analyze network traffic for suspicious patterns, known attack signatures, and behavioral anomalies, allowing organizations to proactively identify and mitigate potential breaches before they cause significant damage.
What criteria should be considered when selecting a firewall with IDS for US-based networks?
Key criteria include compliance with US regulations (such as NIST or CMMC), scalability, threat intelligence updates, performance under load, and integration with existing security infrastructure. Additionally, consider vendor support, total cost of ownership, and the ability to handle encrypted traffic without compromising network speed.
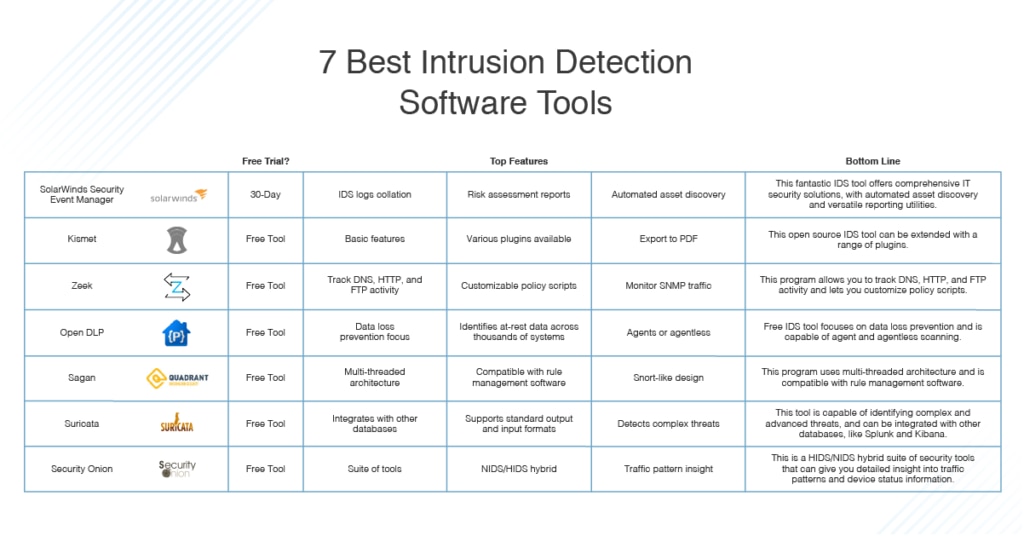
Are there any open-source firewall options with IDS suitable for US networks?
Yes, pfSense and OPNsense are popular open-source firewall platforms that support IDS functionality through integrations with tools like Suricata or Snort. While they may require more manual configuration and expertise, they offer robust security features and are suitable for organizations with budget constraints or specific customization needs.




Deja una respuesta