Top Hardware Firewalls for Reliable Networks

- Key Considerations for Selecting Top Hardware Firewalls for Reliable Networks
- Top Hardware Firewalls for Reliable Networks: A Detailed Guide
- Which hardware firewall models are considered optimal for ensuring network reliability in enterprise environments?
- What criteria determine the top-rated hardware firewall solution globally for network security applications?
- How do hardware firewalls compare to software-based alternatives in terms of performance and security effectiveness?
- More information of interest
- What are the key features to consider when selecting a hardware firewall?
- Which hardware firewalls are recommended for enterprise-level networks?
- How do hardware firewalls enhance network security compared to software firewalls?
- What maintenance and monitoring practices are essential for hardware firewalls?
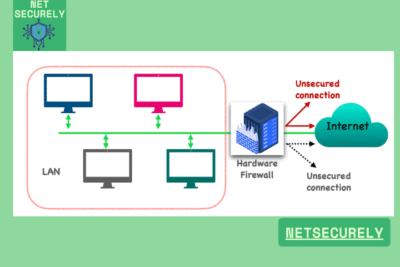
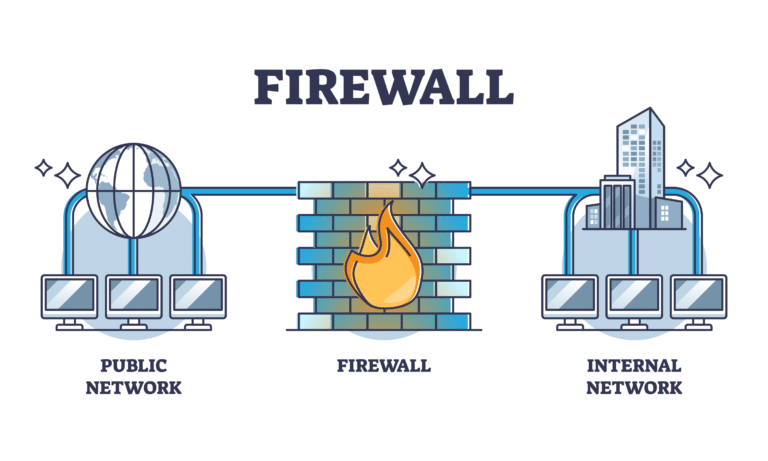
In today's interconnected digital landscape, safeguarding network integrity is paramount for organizations of all sizes. The deployment of robust security infrastructure is essential to defend against evolving cyber threats and unauthorized access. Among the foundational components of a comprehensive defense strategy are the , which provide dedicated, high-performance filtering at the network perimeter.
These purpose-built appliances offer superior throughput, advanced threat detection, and granular control over traffic, ensuring uninterrupted operations and data protection. Investing in proven hardware firewall solutions is a critical step toward maintaining a secure, resilient, and trustworthy network environment.
Key Considerations for Selecting Top Hardware Firewalls for Reliable Networks
When evaluating Top Hardware Firewalls for Reliable Networks, several critical factors must be considered to ensure optimal performance and security. These include throughput capacity, threat prevention capabilities, scalability, management features, and total cost of ownership. Enterprise-grade firewalls should provide deep packet inspection, intrusion prevention systems (IPS), VPN support, and centralized management options. Additionally, compatibility with existing network infrastructure and vendor support services are vital for maintaining network reliability and security posture.
Performance and Throughput Specifications
Performance is a cornerstone of Top Hardware Firewalls for Reliable Networks. Throughput metrics—including firewall throughput, IPS throughput, and VPN throughput—directly impact network efficiency. High-end models typically offer multi-gigabit throughput with minimal latency, ensuring uninterrupted business operations. Enterprises should match firewall specifications to their network traffic volume, considering future growth and peak usage scenarios to avoid bottlenecks.
Security Features and Threat Prevention
Modern Top Hardware Firewalls for Reliable Networks incorporate advanced security features such as application control, antivirus/antimalware scanning, sandboxing, and SSL/SSH inspection. Integrated intrusion prevention systems (IPS) and real-time threat intelligence feeds help block emerging threats. These capabilities work in tandem to create layered defense mechanisms, crucial for protecting against sophisticated cyberattacks and ensuring regulatory compliance.
Scalability and Network Integration
Scalability ensures that Top Hardware Firewalls for Reliable Networks can adapt to evolving business needs. Features like modular expansion slots, support for high-availability configurations, and virtual system capabilities allow seamless growth. Compatibility with existing network architectures—including SD-WAN, cloud environments, and hybrid setups—is essential for maintaining operational continuity and avoiding costly infrastructure overhauls.
Management and Monitoring Capabilities
Effective management is critical for maintaining Top Hardware Firewalls for Reliable Networks. Centralized management platforms provide unified control over multiple devices, simplifying policy enforcement and monitoring. Features like real-time dashboards, automated reporting, and alert systems enhance visibility into network traffic and security events, enabling proactive responses to potential issues.
Vendor Support and Total Cost of Ownership
Beyond initial purchase price, Top Hardware Firewalls for Reliable Networks require evaluation of long-term costs including licensing, maintenance, and energy consumption. Vendor support—such as firmware updates, technical assistance, and hardware warranties—directly impacts firewall reliability and lifespan. Enterprises should assess service level agreements (SLAs) and vendor reputation to ensure sustained network protection.
| Firewall Model | Throughput (Max) | Threat Prevention | Scalability Options |
| Model A | 10 Gbps | IPS, Antivirus | HA Clustering |
| Model B | 20 Gbps | Sandboxing, SSL Inspection | Virtual Systems |
| Model C | 40 Gbps | Advanced Malware Protection | Modular Expansion |
Top Hardware Firewalls for Reliable Networks: A Detailed Guide
Which hardware firewall models are considered optimal for ensuring network reliability in enterprise environments?
For enterprise environments requiring robust network reliability, the optimal hardware firewall models typically include next-generation firewalls from established vendors such as Palo Alto Networks PA-Series (particularly the PA-5200 and PA-7000 series for large-scale deployments), Fortinet FortiGate series (notably the 6000 and 7000 models for high-throughput scenarios), and Cisco Firepower 4100/9300 series, which offer deep packet inspection, advanced threat protection, and high availability features; these devices are engineered with redundant power supplies, failover capabilities, and scalable architecture to minimize downtime and ensure continuous operation, making them the Top Hardware Firewalls for Reliable Networks in demanding corporate infrastructures.
Palo Alto Networks PA-Series Firewalls
Palo Alto Networks PA-Series firewalls are widely regarded as industry leaders for enterprise reliability due to their advanced threat prevention capabilities and high-availability configurations. These appliances, such as the PA-5200 and PA-7000 models, provide redundant hardware components, including hot-swappable power supplies and fans, along with seamless failover mechanisms that ensure uninterrupted network security even during hardware failures or maintenance windows. Their single-pass architecture processes traffic efficiently without compromising performance, making them ideal for mission-critical environments where zero downtime is essential.
| Model | Throughput | High Availability | Threat Prevention |
|---|---|---|---|
| PA-5260 | 20 Gbps | Active/Passive | Yes |
| PA-7080 | 120 Gbps | Active/Active | Yes |
Fortinet FortiGate Series
The Fortinet FortiGate series, especially models like the FortiGate 6000 and 7000, excels in delivering network reliability through their custom security processing units (SPUs) that offload intensive tasks like encryption and inspection from the main CPU. These firewalls support fortified hardware redundancy with multiple power supplies and NP6-based ASICs for accelerated performance, ensuring consistent throughput even under heavy load. Features such as virtual clustering and built-in SD-WAN capabilities further enhance resilience, making them a top choice for enterprises requiring scalable and fault-tolerant security infrastructure.
| Model | Throughput | Redundancy | SPU Support |
|---|---|---|---|
| FortiGate 6300F | 100 Gbps | Dual PSU | Yes |
| FortiGate 7100 | 200 Gbps | Full HA | Yes |
Cisco Firepower 4100/9300 Series
Cisco Firepower 4100 and 9300 series firewalls are engineered for enterprise-grade reliability with modular and scalable designs that support redundant management and data planes. These models integrate threat intelligence from Talos and offer clustering capabilities that allow multiple devices to operate as a single logical unit, distributing traffic and maintaining uptime during component failures. With features like Cisco SecureX integration and support for SSD failover, they provide a resilient security posture suitable for large organizations with complex network demands.
| Model | Throughput | Clustering | Modularity |
|---|---|---|---|
| Firepower 4110 | 20 Gbps | Yes | Yes |
| Firepower 9300 | 100 Gbps | Yes | Yes |
What criteria determine the top-rated hardware firewall solution globally for network security applications?

The top-rated hardware firewall solutions are determined by a comprehensive set of criteria including robust threat prevention capabilities such as deep packet inspection, intrusion prevention systems (IPS), and advanced malware protection, high-performance throughput with minimal latency even under heavy traffic loads, scalability to accommodate growing network demands, ease of management through intuitive interfaces and centralized control, compliance with industry standards and regulations, and proven reliability with features like high availability and failover support, ensuring uninterrupted security for critical infrastructure, which collectively define the benchmark for Top Hardware Firewalls for Reliable Networks.
Performance and Throughput Metrics
Performance is a critical factor, with top solutions delivering high throughput (measured in Gbps) for both firewall and threat inspection processes, ensuring minimal latency even during peak traffic; they typically support multi-gigabit speeds and utilize specialized processors like ASICs or FPGAs for efficient packet processing, which is essential for maintaining network agility without compromising security, making them ideal for data-intensive environments where Top Hardware Firewalls for Reliable Networks must handle substantial loads seamlessly.
| Metric | Description | Typical Value for Top Firewalls |
|---|---|---|
| Firewall Throughput | Maximum data rate with basic filtering | 10-100 Gbps |
| IPS Throughput | Throughput with intrusion prevention enabled | 5-50 Gbps |
| Latency | Delay introduced by the firewall | < 10 microseconds |
Security Features and Threat Prevention
Advanced security features are paramount, including deep packet inspection (DPI), intrusion prevention systems (IPS), application control, and sandboxing for unknown threats; these solutions integrate real-time threat intelligence feeds and employ machine learning to detect and mitigate zero-day attacks, providing comprehensive protection against evolving cyber threats while ensuring compliance with security policies, which solidifies their status as a foundational component in safeguarding network integrity.
| Feature | Function | Importance Level |
|---|---|---|
| IPS/IDS | Detects and blocks intrusions | Critical |
| Application Control | Manages app-specific traffic | High |
| Threat Intelligence | Uses global data for blocking | Essential |
Scalability and Management
Scalability ensures the firewall can grow with network demands, supporting features like clustering for high availability, virtualization for segmenting security policies, and centralized management through platforms that allow unified control over multiple devices; ease of management via graphical interfaces, APIs for automation, and detailed logging and reporting capabilities reduces operational overhead and enhances responsiveness to security incidents, which is vital for maintaining long-term network resilience and adaptability.
| Aspect | Description | Benefit |
|---|---|---|
| High Availability | Redundant configurations for uptime | Minimizes downtime |
| Centralized Management | Single console for multiple firewalls | Simplifies administration |
| API Support | Enables automation and integration | Enhances efficiency |
How do hardware firewalls compare to software-based alternatives in terms of performance and security effectiveness?

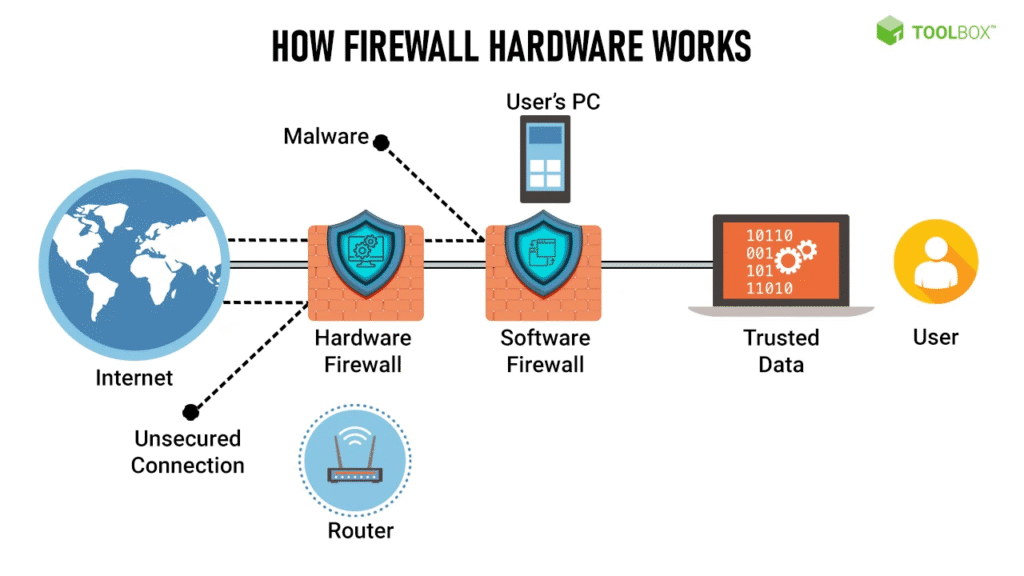
Hardware firewalls and software-based firewalls differ significantly in performance and security effectiveness; hardware firewalls operate as dedicated physical appliances, providing robust throughput with minimal latency by offloading processing from host systems, and they typically offer stronger perimeter defense through specialized chipsets and deep packet inspection, whereas software firewalls run on general-purpose operating systems, which may introduce performance overhead due to resource sharing and potential vulnerabilities in the underlying OS, though they excel in granular application-level control and adaptability for individual endpoints, making hardware solutions like the Top Hardware Firewalls for Reliable Networks preferable for high-traffic environments where isolation and throughput are critical, while software alternatives are more suited for flexible, host-specific security policies.
Performance Comparison: Hardware vs. Software Firewalls
Hardware firewalls generally deliver superior performance due to their dedicated processing units and optimized architecture for network traffic handling, which minimizes latency and maximizes throughput even under heavy loads, whereas software firewalls rely on the host system's CPU and memory, often causing resource contention and reduced efficiency, especially in high-demand scenarios; this makes hardware solutions ideal for enterprise networks requiring consistent, high-speed filtering without compromising other operations.
Security Effectiveness: Isolation and Control
In terms of security effectiveness, hardware firewalls provide stronger isolation from threats by operating independently of endpoint devices, reducing the risk of compromise through OS vulnerabilities, and they often include advanced features like integrated intrusion prevention and granular rule sets for comprehensive perimeter defense, while software firewalls offer deeper application-layer visibility and control on individual devices, allowing for tailored policies but potentially exposing them to attacks if the host is compromised.
Deployment Scenarios and Use Cases
The choice between hardware and software firewalls depends largely on the deployment context; hardware firewalls, including the Top Hardware Firewalls for Reliable Networks, are best suited for protecting entire networks at the perimeter or between segments, offering scalability and centralized management for large organizations, whereas software firewalls are more effective for securing individual servers, endpoints, or mobile devices, providing portability and customized protection based on specific application needs, as illustrated in the table below comparing key aspects.
| Aspect | Hardware Firewalls | Software Firewalls |
|---|---|---|
| Performance Impact | Minimal, dedicated resources | Variable, host-dependent |
| Security Scope | Network-wide perimeter defense | Device-specific application control |
| Deployment Flexibility | Fixed physical appliance | Installable on various OS platforms |
| Typical Use Case | Enterprise network infrastructure | Individual endpoints or cloud instances |
More information of interest
What are the key features to consider when selecting a hardware firewall?
When selecting a hardware firewall, key features to prioritize include throughput capacity, which determines data processing speed, security capabilities such as intrusion prevention and deep packet inspection, scalability to accommodate network growth, and centralized management options for efficient administration and monitoring.
Which hardware firewalls are recommended for enterprise-level networks?
For enterprise-level networks, top recommended hardware firewalls include models from Cisco (such as the ASA series), Fortinet FortiGate series, Palo Alto Networks PA-Series, and Check Point appliances, known for their advanced threat protection, high availability, and robust performance under heavy traffic loads.
How do hardware firewalls enhance network security compared to software firewalls?
Hardware firewalls enhance network security by operating as dedicated appliances that filter traffic before it reaches internal devices, providing perimeter defense, reducing resource consumption on individual systems, and offering superior throughput and specialized threat mitigation features that software firewalls may lack.
What maintenance and monitoring practices are essential for hardware firewalls?
Essential maintenance and monitoring practices include regularly updating firmware to patch vulnerabilities, configuring and reviewing logs for suspicious activity, performing periodic audits of firewall rules, and ensuring redundancy setups like high availability to minimize downtime and maintain continuous protection.





Deja una respuesta