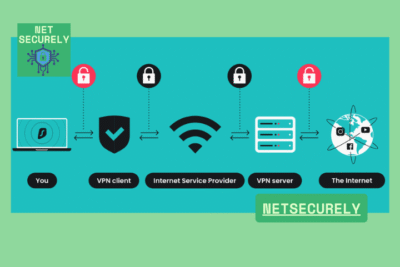
Top VPNs for Anonymous Online Surfing and Security

- Comparing the Most Effective VPN Services for Anonymous Browsing
- Comprehensive Guide to Top VPNs for Anonymous Online Surfing and Security
- Which VPN service offers the highest level of security and anonymity for online activities?
- What VPN solution most effectively conceals a user's digital identity and browsing habits?
- To what extent can VPN services provide genuine anonymity for internet users?
- Are there VPN providers capable of maintaining undetectable connections across various networks?
- More information of interest
Top VPNs for Anonymous Online Surfing and Security, in today’s digital age, safeguarding your online privacy has never been more critical. As cyber threats and data breaches become increasingly common, internet users are seeking effective solutions to protect their sensitive information and maintain anonymity. This article provides an in-depth analysis of the leading services available, focusing on the essential features that define reliable protection.

We will explore the , evaluating their encryption standards, no-log policies, speed, and overall performance. Whether for personal use or professional needs, this guide aims to help you make an informed decision to ensure a secure and private browsing experience.
You may also be interested in reading: Best Free VPNs for Anonymous Browsing in USA
Comparing the Most Effective VPN Services for Anonymous Browsing
When evaluating Top VPNs for Anonymous Online Surfing and Security, several critical factors must be considered. These include encryption standards, no-logs policies, server network size, connection speeds, and additional security features. The best services provide military-grade encryption, strict no-logs verification through independent audits, and advanced features like kill switches and DNS leak protection. Performance consistency across global servers and compatibility with various devices also play crucial roles in determining the overall effectiveness of a VPN service for maintaining anonymity and security.
Essential Security Features for Complete Anonymity
Top-tier VPN services implement multiple layers of security to ensure user anonymity. The most critical features include AES-256 encryption, which is the same standard used by government agencies. A verified no-logs policy ensures that user activity isn't recorded or stored. Additional essential features comprise automatic kill switches that disconnect internet access if the VPN connection drops, DNS leak protection, and split tunneling capabilities. Many leading services also offer obfuscated servers that disguise VPN traffic as regular internet traffic, providing an extra layer of anonymity in restrictive regions.
Performance and Speed Considerations
VPN performance directly impacts user experience, with speed being a crucial factor. The best services maintain minimal speed reduction, typically within 10-15% of the original connection speed. This is achieved through optimized server networks, modern protocols like WireGuard, and unlimited bandwidth. Server proximity and load balancing also significantly affect performance. Premium VPNs typically offer thousands of servers globally, allowing users to connect to less crowded servers for better speeds. Regular network upgrades and server maintenance ensure consistent performance for streaming, downloading, and browsing activities.
Server Network and Geographic Coverage
A comprehensive server network is vital for both accessibility and performance. Leading VPN providers maintain servers in 60+ countries, with some offering 90+ country coverage. The number of servers typically ranges from 3,000 to 8,000+ across global locations. This extensive coverage allows users to bypass geo-restrictions and access content from various regions. Additionally, having servers in privacy-friendly jurisdictions enhances security, as these locations often have stronger data protection laws. The distribution of servers across different continents also ensures reliable connection options regardless of user location.
Privacy Policies and Jurisdiction
The legal jurisdiction of a VPN provider significantly impacts user privacy. Services based in privacy-friendly countries (outside the 5/9/14 Eyes alliances) offer better protection against data requests. Comprehensive privacy policies should clearly state what data is collected, if any, and how it's handled. Independent audits and transparency reports validate these claims. The best providers undergo regular third-party audits to verify their no-logs policies and security measures. User-friendly jurisdictions combined with strong privacy policies create a foundation for trustworthy anonymous browsing.
Compatibility and Simultaneous Connections
Modern VPN services must support various devices and operating systems. The top providers offer dedicated applications for Windows, macOS, iOS, Android, and often Linux. Many also provide browser extensions and router compatibility for whole-network protection. Simultaneous connections range from 5 to unlimited devices per account, allowing users to protect all their devices with a single subscription. Cross-platform consistency ensures the same security features and performance across different devices, making comprehensive protection accessible regardless of the technology being used.
| VPN Provider | Server Count | Countries | Max Devices | Special Features |
| ExpressVPN | 3,000+ | 94 | 8 | TrustedServer technology, Lightway protocol |
| NordVPN | 5,500+ | 60 | 6 | Double VPN, Onion over VPN |
| Surfshark | 3,200+ | 100 | Unlimited | CleanWeb, MultiHop |
| Private Internet Access | 35,000+ | 84 | 10 | MACE ad blocker, Port forwarding |
| ProtonVPN | 2,900+ | 67 | 10 | Secure Core, Tor integration |
Comprehensive Guide to Top VPNs for Anonymous Online Surfing and Security
Which VPN service offers the highest level of security and anonymity for online activities?

When evaluating VPN services for maximum security and anonymity, Mullvad VPN consistently ranks among the top choices due to its stringent no-logs policy, anonymous account system using randomly generated numbers instead of email registration, full RAM-only server infrastructure that prevents data persistence, and open-source applications that allow independent security audits; combined with WireGuard protocol implementation and its headquarters in privacy-friendly Sweden (outside 14-Eyes alliance), it provides one of the most robust privacy frameworks available, though users should note that absolute anonymity depends on combining VPN usage with other privacy practices like Tor browsing and disciplined operational security. Among the Top VPNs for Anonymous Online Surfing and Security, Mullvad stands out for refusing even to collect email addresses or personal identifiers.
Critical Security Features in High-Anonymity VPNs
The highest security standards in VPN services incorporate multiple advanced features including military-grade 256-bit AES encryption, a strict no-logs policy independently audited and verified, DNS leak protection, and kill switch functionality that immediately halts internet traffic if the VPN connection drops. These services typically operate using modern protocols like WireGuard or OpenVPN that balance speed with impenetrable security, while also utilizing RAM-only servers (diskless infrastructure) that physically cannot store user data permanently. The most secure providers often incorporate multi-hop connections (routing traffic through multiple servers) and obfuscated servers designed to bypass VPN blocking in restrictive regions.
Jurisdiction and Legal Protection Factors
A VPN provider's jurisdiction significantly impacts its ability to protect user data, with services based in countries outside intelligence-sharing alliances (like 14-Eyes countries) generally offering stronger legal protection against data requests. The ideal jurisdictions have privacy-friendly laws that don’t mandate data retention and lack broad surveillance agreements with other nations; countries like Panama (NordVPN), British Virgin Islands (ExpressVPN), and Sweden (Mullvad VPN) are frequently preferred for their strong privacy statutes. Providers operating under these jurisdictions typically publish transparency reports detailing how they handle legal requests, and the most secure services have undergone independent audits to verify their no-log claims and infrastructure security.
Performance Comparison of Leading Privacy-Focused VPNs
| VPN Service | Encryption Protocol | No-Logs Audit | Jurisdiction | Unique Anonymity Feature |
|---|---|---|---|---|
| Mullvad VPN | WireGuard/OpenVPN | Yes (2020, 2023) | Sweden | Account number system (no email) |
| ProtonVPN | WireGuard/OpenVPN | Yes (2022) | Switzerland | Secure Core servers |
| IVPN | WireGuard/OpenVPN | Yes (2023) | Gibraltar | Multi-hop configurations |
| NordVPN | NordLynx (WireGuard) | Yes (2023) | Panama | Double VPN encryption |
What VPN solution most effectively conceals a user's digital identity and browsing habits?
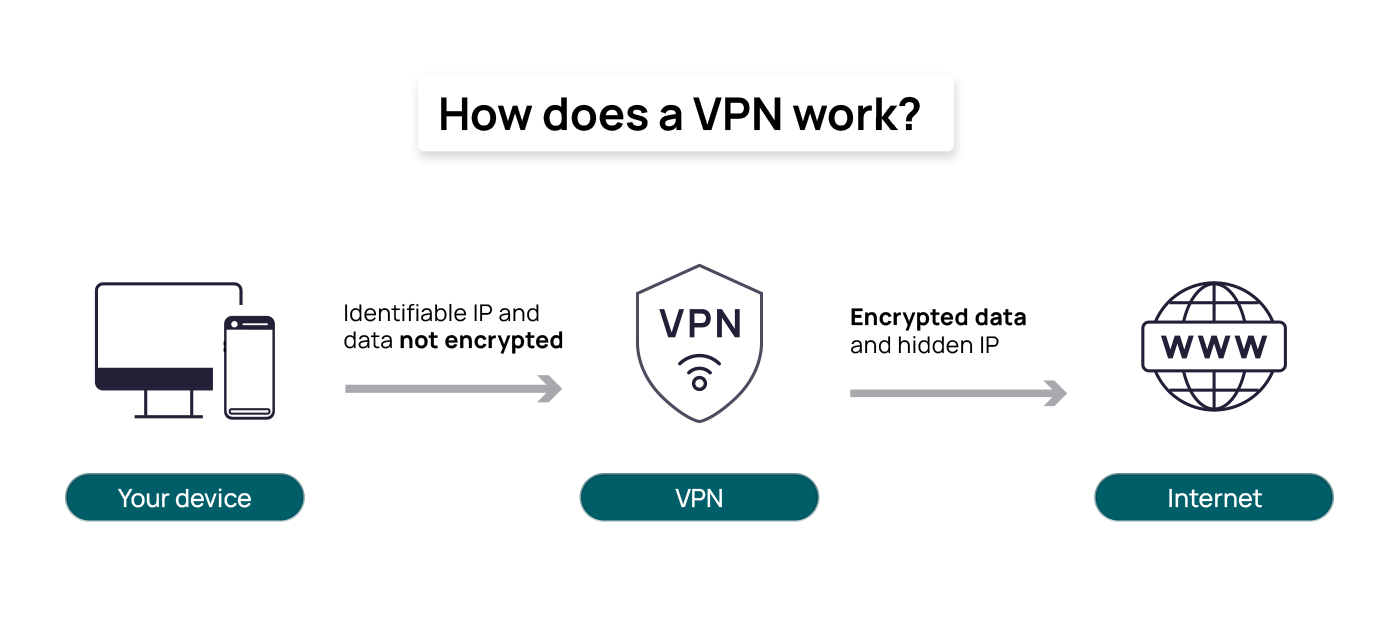
The most effective VPN solution for concealing digital identity and browsing habits combines advanced encryption protocols like OpenVPN or WireGuard, a strict no-logs policy audited by independent third parties, and features such as a kill switch, DNS/IPv6 leak protection, and obfuscated servers to bypass deep packet inspection. Providers like Mullvad VPN and ProtonVPN excel in these areas by operating under jurisdictions with strong privacy laws, accepting anonymous payment methods like cryptocurrency, and implementing RAM-only servers that wipe data upon reboot, ensuring no residual traces of user activity remain.
Key Features of an Effective VPN for Identity Protection
An effective VPN must prioritize strong encryption standards, such as AES-256, alongside a verified no-logs policy to ensure no user data is stored or shared. Additional critical features include a kill switch to halt internet traffic if the VPN connection drops, DNS leak protection to prevent exposure of browsing queries, and obfuscated servers that mask VPN traffic as regular HTTPS traffic, making it undetectable to ISPs or network administrators. These elements collectively form the foundation of Top VPNs for Anonymous Online Surfing and Security, providing users with robust anonymity against surveillance and tracking.
Jurisdiction and Privacy Laws Impacting VPN Effectiveness
The jurisdiction under which a VPN operates significantly influences its ability to protect user privacy; providers based in countries outside Five Eyes, Nine Eyes, or Fourteen Eyes alliances, such as Panama or Switzerland, are preferable as they face fewer data retention laws and legal pressures to share user information. For instance, a VPN headquartered in a privacy-friendly region can legally enforce a strict no-logs policy, whereas those in jurisdictions like the United States or United Kingdom may be compelled to collect and hand over data, undermining user anonymity. This legal aspect is crucial for ensuring that a VPN can truly conceal digital identity without external interference.
| Jurisdiction | Privacy Implications | Example VPNs |
|---|---|---|
| Panama | No data retention laws, outside surveillance alliances | NordVPN |
| Switzerland | Strong privacy protections, independent of EU/US laws | ProtonVPN |
| United States | Subject to data requests and Five Eyes membership | Many US-based providers |
Advanced Technologies for Browsing Habit Concealment
Advanced technologies such as MultiHop (double VPN) routes, which channel traffic through multiple servers to obscure the original IP address, and split tunneling, allowing users to select which apps use the VPN, enhance browsing habit concealment. Additionally, obfuscation techniques that disguise VPN traffic as normal internet traffic help bypass firewalls and ISP throttling, while RAM-only servers ensure all data is volatile and erased upon reboot, leaving no physical storage traces. These technologies work in tandem to make user activity virtually untraceable, which is a hallmark of Top VPNs for Anonymous Online Surfing and Security.
To what extent can VPN services provide genuine anonymity for internet users?
/images/2025/04/03/anonymity-and-vpns-2025.png)
VPN services provide a significant layer of privacy but fall short of guaranteeing complete anonymity, as they primarily mask the user's IP address and encrypt internet traffic between the device and the VPN server, preventing ISPs and local network observers from monitoring activities; however, true anonymity depends on the VPN provider's policies—particularly their logging practices, jurisdiction, and transparency—since providers with data retention requirements or vulnerable infrastructure can potentially link activities to users, especially if combined with other identifying data like cookies, device fingerprints, or metadata leaks, meaning that while VPNs are powerful tools for enhancing privacy and security, they are not foolproof and should be complemented with additional measures like Tor, secure browsers, and disciplined online behavior to approach genuine anonymity.
Technical Limitations of VPN Anonymity
VPNs encrypt user data and route it through remote servers, hiding the original IP address from websites and ISPs, but they do not conceal all identifying information; for instance, DNS leaks, WebRTC vulnerabilities, or browser fingerprinting can still expose user details, and if the VPN connection drops unexpectedly without a kill switch, the real IP may be revealed temporarily, underscoring that technical flaws can compromise anonymity even with reputable services, which is why users must choose providers with robust leak protection features and regularly test their connections for vulnerabilities.
Legal and Logging Policies Impacting Anonymity
The degree of anonymity offered by a VPN is heavily influenced by the provider's jurisdiction and logging policies; services based in countries with strict data retention laws or within surveillance alliances like the Five Eyes may be compelled to collect and hand over user data, whereas no-logs policies—audited and verified—provide stronger assurances, though not absolute, as some metadata might still be retained for operational purposes, making it crucial to select providers with transparent, independent audits and a commitment to privacy, such as those often listed among Top VPNs for Anonymous Online Surfing and Security, to minimize risks of exposure.
Behavioral and External Factors Affecting Anonymity
| Factor | Description | Impact on Anonymity |
|---|---|---|
| User Logins | Accessing personal accounts (e.g., email, social media) while using a VPN | Directly links activity to identity, negating anonymity |
| Malware or Tracking Scripts | Presence of malicious software or cookies on the device | Can bypass VPN encryption and reveal user information |
| Payment Methods | Using credit cards or identifiable details for VPN subscription | Creates a paper trail associating the user with the service |
Are there VPN providers capable of maintaining undetectable connections across various networks?

Yes, there are VPN providers capable of maintaining undetectable connections across various networks by utilizing advanced obfuscation techniques that disguise VPN traffic as regular HTTPS traffic, implementing proprietary protocols like WireGuard or OpenVPN with stealth options, and employing constantly updated methods to bypass deep packet inspection (DPI) and network restrictions imposed by ISPs, governments, or corporate firewalls; these providers often operate with RAM-only servers, strict no-logs policies, and anti-censorship features to ensure reliable access even in highly restrictive environments, making them essential tools for privacy-conscious users and those in regions with heavy internet surveillance.
Advanced Obfuscation Techniques for VPN Undetectability
VPN providers use advanced obfuscation techniques to make VPN traffic appear as normal internet traffic, such as HTTPS, which helps evade detection by network administrators or restrictive firewalls; methods include scrambling packet headers, using XOR encryption, or integrating with Shadowsocks proxies to bypass deep packet inspection (DPI), ensuring that even in heavily monitored networks, the connection remains隐蔽 and functional for users seeking privacy or access to restricted content, with some services specializing in these features as part of their core offering for secure browsing.
Protocols and Features Ensuring Stealth Across Networks
To maintain undetectable connections, VPN providers leverage protocols like WireGuard, OpenVPN with obfuscation, or proprietary options such as NordLynx, combined with features like automatic server switching, kill switches, and multi-hop connections that route traffic through multiple servers to obscure the origin; these elements work together to provide robust security and anonymity, with many services offering dedicated stealth modes designed for use in countries with stringent internet controls, making them a key component for reliable and secure online activities without detection.
Evaluating Top VPNs for Anonymous Online Surfing and Security
When evaluating Top VPNs for Anonymous Online Surfing and Security, key criteria include their ability to maintain undetectable connections through obfuscation, no-logs policies, server network size, and performance speed; below is a comparison table of features that contribute to stealth and reliability across various networks.
| VPN Provider | Obfuscation Support | No-Logs Policy | Server Count | Stealth Mode |
|---|---|---|---|---|
| ExpressVPN | Yes | Audited | 3000+ | Lightway Protocol |
| NordVPN | Yes | Audited | 5000+ | Obfuscated Servers |
| Surfshark | Yes | Audited | 3200+ | Camouflage Mode |
These providers are renowned for their effectiveness in bypassing restrictions and ensuring user anonymity, with strong encryption and regular updates to counter new detection methods.
More information of interest
What defines the best VPNs for anonymous online surfing and security?
The best VPNs for anonymous online surfing and security are defined by their strict no-logs policy, robust encryption standards, and a proven ability to conceal users' IP addresses and online activities from surveillance, hackers, and data collection.
How do VPNs ensure user anonymity and protect against tracking?
VPNs ensure user anonymity by routing internet traffic through encrypted servers, which masks the user's real IP address and location, making it difficult for ISPs, advertisers, or malicious actors to track online behavior or identify the user.
Are free VPNs a reliable option for secure and anonymous browsing?
Free VPNs are generally not a reliable option for secure and anonymous browsing, as they often lack strong encryption, may log user data, and could pose privacy risks due to limited security features or even data selling practices.
What additional security features should I look for in a top VPN service?
In addition to standard encryption, look for a kill switch to prevent data leaks if the connection drops, DNS leak protection, and support for secure protocols like WireGuard or OpenVPN, which enhance overall security and anonymity.






Deja una respuesta