
Top VPNs for Business Data Encryption and Privacy

- Essential Features of Top VPNs for Business Data Encryption and Privacy
- Comprehensive Guide to Top VPNs for Business Data Encryption and Privacy
- What criteria determine the most secure VPN solution for business applications?
- Which VPN services offer the most robust data privacy protections for enterprises?
- How do leading business VPNs compare in terms of encryption strength and protocols?
- To what extent do commercial VPNs ensure comprehensive data encryption for business communications?
- More information of interest
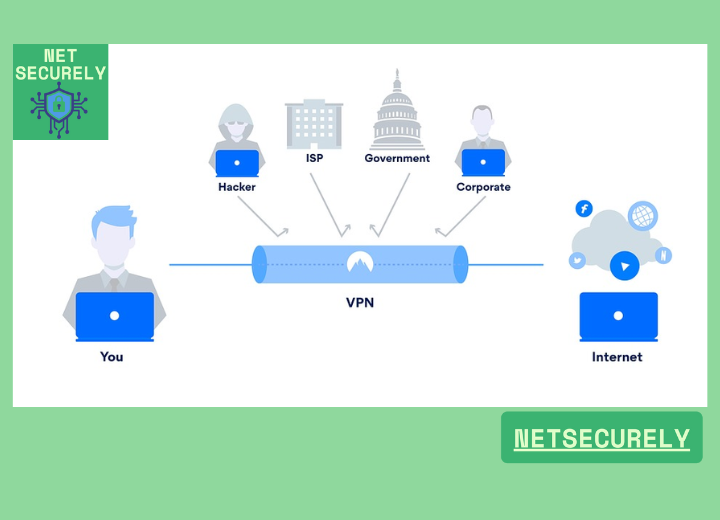
Top VPNs for Business Data Encryption and Privacy, in today’s digital landscape, securing sensitive corporate information has become a paramount concern for businesses of all sizes. As cyber threats grow increasingly sophisticated, organizations must prioritize robust data protection measures to safeguard critical assets and maintain client trust.
Among the most effective tools available are virtual private networks (VPNs), which offer encrypted connections and enhanced privacy for remote and on-site operations alike. This article explores the essential features and benefits of the , providing insights to help enterprises select the right solution for their security needs.
You may also be interested in reading: Top WordPress Hosting for Scalable Websites
Essential Features of Top VPNs for Business Data Encryption and Privacy
Core Encryption Standards in Business VPNs
Business-grade VPN services implement robust encryption protocols to secure sensitive data. The most common standards include AES-256 encryption, which is universally recognized as military-grade protection. Additionally, protocols like OpenVPN, IKEv2/IPSec, and WireGuard® provide secure tunneling mechanisms. These protocols ensure that all data transmitted between corporate networks and remote employees remains impervious to interception. Top VPNs for Business Data Encryption and Privacy typically offer customizable encryption settings, allowing organizations to balance security requirements with performance needs based on their specific industry compliance standards.
Enterprise-Grade Security Protocols
Enterprise VPN solutions distinguish themselves through advanced security features beyond basic encryption. These include kill switches that automatically block internet access if the VPN connection drops, preventing data leaks. Multi-factor authentication (MFA) adds an extra layer of access control, while split tunneling allows businesses to designate which traffic goes through the VPN. Many top-tier business VPNs also incorporate zero-trust network access frameworks, ensuring that no user or device is trusted by default, thereby minimizing potential attack vectors.
Scalability and Network Management
Scalability is critical for growing organizations. Leading business VPN providers offer centralized management consoles that allow IT administrators to deploy, configure, and monitor VPN connections across thousands of endpoints efficiently. Features like automated user provisioning and role-based access control simplify network management. These platforms typically provide detailed usage analytics and reporting tools, enabling businesses to optimize their network performance and maintain compliance with data protection regulations as they expand their operations.
Compliance and Audit Support
Business VPN providers catering to enterprises often adhere to stringent compliance certifications including GDPR, HIPAA, and SOC 2 standards. They maintain comprehensive audit logs and provide documentation necessary for regulatory compliance. These services typically offer dedicated servers for specific compliance requirements and ensure all data handling practices meet industry-specific regulations. The best providers undergo regular third-party security audits and provide transparency reports to their business clients.
Performance and Reliability Metrics
Enterprise VPN performance is measured through several key metrics: uptime guarantees (typically 99.9% or higher), server network size, and throughput speeds. Business-grade providers maintain global server networks with optimized routing to minimize latency. They often offer dedicated IP addresses and bandwidth allocations to ensure consistent performance. Load balancing across multiple servers prevents network congestion, while quality of service (QoS) features prioritize business-critical applications.
| VPN Provider | Encryption Standard | Business Features | Compliance Certifications |
| NordLayer | AES-256 | Centralized Management, ThreatBlock | SOC 2, ISO 27001 |
| Perimeter 81 | AES-256 | Zero Trust Architecture, Cloud Integration | GDPR, HIPAA Compliant |
| ExpressVPN Business | AES-256 | Dedicated Account Manager, Team Management | ISO 27001 Certified |
| Cisco AnyConnect</td | AES-256 | Endpoint Security, Advanced Malware Protection | Multiple Industry Certifications |
Comprehensive Guide to Top VPNs for Business Data Encryption and Privacy
What criteria determine the most secure VPN solution for business applications?
The most secure VPN solution for business applications is determined by several key criteria, including robust encryption protocols such as AES-256, which ensures data confidentiality; strict no-logs policies verified through independent audits to guarantee user privacy; multi-factor authentication (MFA) and role-based access controls to prevent unauthorized entry; network security features like a kill switch and DNS leak protection to maintain connection integrity; scalability to accommodate organizational growth without compromising performance; compliance with industry standards such as GDPR, HIPAA, or SOC 2 for legal and regulatory adherence; and reliable performance with high-speed servers and minimal latency to support business operations seamlessly, making it essential to evaluate providers that specialize in Top VPNs for Business Data Encryption and Privacy.
Encryption Standards and Protocols
Encryption standards and protocols form the foundation of a secure VPN, with AES-256 encryption being the industry benchmark for protecting data in transit and at rest; additionally, support for modern protocols like WireGuard, OpenVPN, or IKEv2/IPsec ensures a balance between security and performance, as these protocols offer strong encryption while minimizing latency and maximizing compatibility across devices and networks, which is critical for maintaining both security and usability in business environments.
| Protocol | Encryption Strength | Best Use Case |
|---|---|---|
| OpenVPN | AES-256 | High security, general business use |
| WireGuard | ChaCha20 | Speed-focused applications |
| IKEv2/IPsec | AES-256 | Mobile device stability |
Authentication and Access Control Mechanisms
Authentication and access control mechanisms are vital for ensuring that only authorized users can access the VPN and internal resources, with multi-factor authentication (MFA) adding an extra layer of security by requiring multiple verification methods, such as passwords and biometrics, while role-based access control (RBAC) allows administrators to define and enforce permissions based on user roles, ensuring that employees only have access to the data and systems necessary for their job functions, thereby reducing the risk of internal threats or data breaches.
Compliance and Auditing Requirements
Compliance and auditing requirements are critical for businesses operating in regulated industries, as a secure VPN must adhere to standards such as GDPR, HIPAA, or SOC 2 to protect sensitive data and avoid legal penalties; independent third-party audits and certifications validate the VPN provider's security claims, including their no-logs policy and data handling practices, providing assurance that the solution meets rigorous security and privacy benchmarks required for business applications.
Which VPN services offer the most robust data privacy protections for enterprises?

For enterprises seeking the most robust data privacy protections, several VPN services stand out due to their advanced security features, strict no-logs policies, and enterprise-grade infrastructure, with providers like NordLayer, Perimeter 81, and Cisco AnyConnect Secure Mobility Client offering comprehensive solutions that include AES-256 encryption, secure protocols like WireGuard or OpenVPN, dedicated servers, and compliance with standards such as GDPR and ISO 27001, ensuring that business data remains confidential and protected against unauthorized access, making them among the Top VPNs for Business Data Encryption and Privacy.
Key Security Features for Enterprise VPNs
Enterprise VPNs prioritize advanced security features to safeguard sensitive data, including AES-256 encryption, which is the industry standard for securing communications, along with support for multiple protocols such as OpenVPN, WireGuard, and IKEv2/IPsec to ensure flexibility and high performance. Additionally, features like kill switches, DNS leak protection, and multi-factor authentication (MFA) are critical for maintaining privacy, as they prevent data exposure even if the VPN connection drops, while dedicated IP addresses and private servers further enhance security by reducing the risk of sharing resources with other users, making these elements essential for any enterprise-focused VPN service.
No-Logs Policies and Data Jurisdiction
A strict no-logs policy is fundamental for enterprise VPNs, as it ensures that the provider does not store any user activity or connection data, which is crucial for compliance with regulations like GDPR or HIPAA. The jurisdiction of the VPN provider also plays a significant role; services based in privacy-friendly countries, such as those outside the Five Eyes alliance, are preferred to avoid data retention laws. Enterprises should verify that their chosen VPN undergoes independent audits to confirm their no-logs claims, as this provides an extra layer of trust and transparency, ensuring that sensitive business information is never recorded or accessible to third parties.
Performance and Scalability for Business Use
Enterprise VPNs must balance robust security with high performance and scalability to support large teams and data-intensive applications. This includes offering unlimited bandwidth, high-speed servers optimized for low latency, and the ability to handle multiple simultaneous connections without degradation. Scalability features such as centralized management consoles, user role permissions, and SD-WAN integration allow businesses to efficiently manage their network across various locations and devices. The table below summarizes key performance aspects for top enterprise VPN providers:
| Provider | Max Connections | Server Locations | Bandwidth | Management Tools |
|---|---|---|---|---|
| NordLayer | Unlimited | 60+ countries | Unlimited | Centralized admin panel |
| Perimeter 81 | Unlimited | 50+ countries | Unlimited | Cloud-based management |
| Cisco AnyConnect | Depends on license | Global | Unlimited | Enterprise management suite |
How do leading business VPNs compare in terms of encryption strength and protocols?
Leading business VPNs generally employ military-grade encryption standards, with most utilizing AES-256 bit encryption—the same standard adopted by governments and security experts worldwide—while supporting multiple protocols including OpenVPN, IKEv2/IPsec, and WireGuard, though implementation varies with some providers like Cisco Meraki favoring proprietary protocols for enterprise integration, whereas others such as Perimeter 81 and Palo Alto Networks prioritize open standards for broader compatibility; performance differences emerge in protocol selection where WireGuard offers superior speed for modern applications while IPsec provides stronger compatibility with legacy systems, and all leading solutions maintain strict no-logs policies though their encryption key management approaches differ significantly between cloud-based and on-premises deployments.
Encryption Standards Comparison
Top business VPN providers universally implement AES-256 encryption as their baseline standard, though key exchange mechanisms and perfect forward secrecy implementations create meaningful differentiation; some enterprise solutions like Zscaler add supplemental encryption layers for specific data types while maintaining FIPS 140-2 compliance across all connections, ensuring that even the Top VPNs for Business Data Encryption and Privacy maintain consistent cryptographic integrity regardless of deployment scale or geographic distribution.
Protocol Performance and Compatibility
Protocol support varies significantly with OpenVPN remaining the universal standard for cross-platform compatibility while WireGuard emerges as the performance leader for modern deployments; enterprises must balance these against legacy requirements where IPsec/IKEv2 maintains dominance in site-to-site configurations, and leading providers typically offer protocol customization based on specific use cases:
| Protocol | Use Case | Enterprise Adoption |
|---|---|---|
| OpenVPN | Remote access & mobility | Universal |
| WireGuard | High-speed cloud access | Growing |
| IPsec/IKEv2 | Site-to-site tunnels | Established |
| SSL VPN | Web application access | Selective |
Enterprise Security Features Beyond Encryption
Beyond core encryption protocols, leading business VPNs distinguish themselves through additional security layers including integrated threat prevention, granular access controls, and automated compliance auditing; features like split tunneling with application-level control, identity-aware networking, and real-time traffic inspection become critical differentiators in enterprise environments where encryption represents just one component of a comprehensive security architecture.
To what extent do commercial VPNs ensure comprehensive data encryption for business communications?
Commercial VPNs provide a significant level of data encryption for business communications by employing industry-standard protocols such as AES-256 encryption, which is considered virtually unbreakable and is widely used to secure data in transit between corporate networks and remote employees. These services create encrypted tunnels that shield sensitive information from interception, ensuring that emails, file transfers, and internal communications remain confidential. However, the extent of comprehensive encryption can vary based on the provider’s implementation, including factors like perfect forward secrecy, DNS leak protection, and adherence to a strict no-logs policy. While most reputable commercial VPNs offer robust encryption suitable for general business needs, organizations handling highly sensitive data must additionally verify independent audits, jurisdiction-related risks, and endpoint security measures to ensure full protection against sophisticated threats.
Encryption Protocols and Standards in Business VPNs
Business-oriented commercial VPNs typically utilize advanced encryption protocols such as OpenVPN, WireGuard, or IKEv2/IPsec, combined with AES-256 bit encryption, to create a secure tunnel for data transmission. These standards are designed to protect against eavesdropping and man-in-the-middle attacks, ensuring that all communication between remote employees and corporate servers remains confidential. The strength of encryption largely depends on the VPN provider’s configuration, including key exchange mechanisms and the implementation of perfect forward secrecy, which prevents compromised keys from decrypting past sessions. It is crucial for businesses to select providers that transparently disclose their encryption methodologies and undergo independent security audits to validate their claims. Among the Top VPNs for Business Data Encryption and Privacy, those offering customizable protocol options and adherence to global standards like NIST guidelines are generally preferred for comprehensive protection.
Limitations and Vulnerabilities in VPN Encryption
Despite strong encryption standards, commercial VPNs are not impervious to vulnerabilities, which can undermine the security of business communications. Issues such as DNS leaks, IPv6 leakage, or inadequate protection against advanced threats like quantum computing attacks may expose sensitive data. Additionally, some VPN providers might retain logs or operate under jurisdictions that mandate data sharing with authorities, potentially compromising confidentiality. Businesses must assess these risks by evaluating the provider’s no-logs policy, leak protection features, and compliance with regulations like GDPR or HIPAA. The table below highlights common encryption vulnerabilities and mitigation strategies for commercial VPNs:
| Vulnerability | Description | Mitigation Strategy |
|---|---|---|
| DNS Leaks | Unencrypted DNS requests bypassing VPN tunnel | Use VPNs with built-in DNS leak protection |
| Weak Protocol Implementation | Outdated or misconfigured encryption protocols | Select providers supporting modern protocols like WireGuard |
| Jurisdictional Risks | Data sovereignty issues due to provider's location | Choose VPNs based in privacy-friendly jurisdictions |
Evaluating VPN Providers for Business Use
When selecting a commercial VPN for business communications, organizations should conduct thorough evaluations based on encryption robustness, privacy policies, and additional security features. Key criteria include independent audits, transparency reports, and support for multi-factor authentication to enhance access control. It is also advisable to prioritize providers offering dedicated IP addresses, centralized management consoles, and scalable solutions tailored to enterprise needs. The Top VPNs for Business Data Encryption and Privacy often distinguish themselves through features like kill switches, split tunneling, and integration with existing security infrastructure, ensuring seamless and comprehensive protection for all organizational communications.
More information of interest
What are the key features to look for in a business VPN for data encryption?
When selecting a business VPN, prioritize features such as end-to-end encryption, a strict no-logs policy, support for multiple protocols (like OpenVPN or WireGuard), and the ability to handle high-volume traffic without compromising speed or security.
How does a business VPN enhance privacy and security for remote teams?
A business VPN enhances privacy by creating a secure tunnel for all data transmitted between remote employees and company servers, shielding sensitive information from unauthorized access and ensuring compliance with data protection regulations like GDPR or HIPAA.
Can a business VPN protect against data breaches and cyber threats?
Yes, a robust business VPN mitigates risks by employing military-grade encryption to safeguard data in transit, coupled with features like automatic kill switches and DNS leak protection to prevent exposure during unexpected connection drops or attacks.
What factors determine the cost of implementing a business VPN solution?
The cost of a business VPN depends on factors such as the number of users, required server locations, level of technical support, and additional features like dedicated IP addresses or integration with existing security infrastructure.






Deja una respuesta