Top VPNs for Enterprise Data Protection in USA

- Top VPN Solutions for Enterprise Data Protection in USA
- Comprehensive Analysis of Top VPNs for Enterprise Data Protection in USA
- What characteristics define the most secure VPN solution for enterprise-level business operations?
- Which enterprise VPN services offer the strongest data privacy protections for US-based organizations?
- How does an enterprise VPN differ from consumer-grade VPN services in terms of data protection capabilities?
- More information of interest
- What are the key criteria for selecting a VPN for enterprise data protection in the USA?
- How do enterprise VPNs ensure compliance with US data protection regulations?
- What distinguishes top-tier enterprise VPNs from consumer-grade options?
- Can enterprise VPNs protect against advanced cyber threats targeting US businesses?
VPNs for Enterprise Data Protection, in today's interconnected digital landscape, enterprises operating within the United States face unprecedented cybersecurity challenges. With sensitive corporate data increasingly vulnerable to sophisticated cyber threats, robust security measures are no longer optional but essential.
A critical component of any comprehensive enterprise security strategy is the implementation of reliable virtual private networks. This analysis focuses on identifying the most effective solutions tailored for the American corporate environment. We will evaluate key features, performance metrics, and enterprise-specific functionalities to provide a clear overview of the , empowering businesses to safeguard their critical digital assets.
You may be interested in reading: Secure Software Firewalls for Network Defense
Top VPN Solutions for Enterprise Data Protection in USA
Essential Criteria for Selecting Enterprise VPNs
When evaluating Top VPNs for Enterprise Data Protection in USA, organizations must prioritize military-grade encryption protocols, zero-log policies, and robust authentication mechanisms. Enterprises should verify SOC 2 compliance, independent security audits, and jurisdiction outside Five Eyes alliance. Scalability features including centralized management consoles and simultaneous connection capabilities are equally critical for large-scale deployments.
Leading VPN Providers for US Enterprises
NordLayer and Perimeter 81 emerge as top contenders for enterprise VPN solutions, offering dedicated servers across major US business hubs. These providers deliver enterprise-grade features including dedicated IP addresses, advanced threat prevention, and seamless integration with existing security infrastructure. Palo Alto Networks Prisma Access provides additional security layers through its cloud-delivered security framework.
Security Protocols and Encryption Standards
Top-tier enterprise VPNs implement AES-256 encryption alongside protocols like WireGuard® and OpenVPN. Multi-factor authentication, kill switch functionality, and split tunneling are standard features. Enterprises should prioritize providers offering custom security configurations and regular protocol updates to address emerging threats in the US cybersecurity landscape.
Implementation and Management Considerations
Successful deployment of Top VPNs for Enterprise Data Protection in USA requires thorough network assessment and stakeholder alignment. Enterprises must establish clear BYOD policies, employee training protocols, and ongoing monitoring procedures. Centralized administration portals with role-based access control significantly streamline management across multiple locations and departments.
Compliance and Regulatory Requirements
US enterprises must ensure VPN solutions comply with HIPAA, GDPR, CCPA, and industry-specific regulations. Providers should offer detailed audit trails, data residency options, and breach notification systems. Enterprises operating globally require VPNs with international server locations that maintain consistent security standards across jurisdictions.
| VPN Provider | Enterprise Features | US Server Locations | Security Certifications |
| NordLayer | Centralized management, Team billing | 15+ cities | SOC 2 Type 2, ISO 27001 |
| Perimeter 81 | Zero Trust architecture, SIEM integration | 12+ locations | SOC 2, GDPR compliant |
| Palo Alto Prisma | Cloud-delivered security, CASB integration | 20+ nodes | FedRAMP Moderate, ISO 27001 |
| Cisco Secure Connect | SD-WAN integration, Umbrella security | 18+ data centers | FIPS 140-2 validated |
Comprehensive Analysis of Top VPNs for Enterprise Data Protection in USA
What characteristics define the most secure VPN solution for enterprise-level business operations?

The most secure enterprise VPN solution is characterized by end-to-end encryption using protocols like WireGuard or OpenVPN, zero-trust architecture with strict access controls, multi-factor authentication, comprehensive audit logging, split tunneling capabilities, and integration with existing security infrastructure such as SIEM systems and firewalls; it must also offer centralized management, scalable performance for high user loads, and robust redundancy to ensure uninterrupted business operations while maintaining compliance with industry regulations like GDPR or HIPAA, with providers like Top VPNs for Enterprise Data Protection in USA typically excelling in these areas through dedicated private servers and advanced threat protection features.
Encryption Protocols and Authentication Methods
Enterprise VPN security fundamentally relies on advanced encryption protocols such as AES-256 for data confidentiality, coupled with secure key exchange mechanisms through protocols like IKEv2/IPsec or WireGuard, which provide both speed and resilience against attacks; additionally, multi-factor authentication (MFA) is critical, integrating biometrics, hardware tokens, or OTPs to verify user identity beyond passwords, ensuring that only authorized personnel access sensitive network resources while aligning with frameworks like NIST guidelines.
Network Architecture and Access Controls
A zero-trust network architecture is essential, where least-privilege access principles are enforced through granular policies that segment network resources and restrict users to only what they need, minimizing the attack surface; this is complemented by dynamic split tunneling, which allows selective routing of traffic to enhance performance without compromising security, and integration with SD-WAN solutions for optimized, secure connectivity across distributed enterprise environments.
Management, Compliance, and Monitoring
Centralized management platforms enable administrators to enforce consistent security policies, deploy updates, and monitor all VPN connections in real-time across the organization, while comprehensive audit logging and reporting capabilities ensure transparency and facilitate compliance with regulations such as GDPR, HIPAA, or PCI DSS; automated alerts and integration with SIEM systems further enhance threat detection and response, providing a proactive security posture.
| Feature Category | Key Elements | Enterprise Benefit |
|---|---|---|
| Encryption | AES-256, Perfect Forward Secrecy | Data confidentiality and integrity |
| Authentication | MFA, Certificate-based login | Reduced unauthorized access risk |
| Network Security | Zero-trust, Split Tunneling | Minimized attack surface |
| Compliance | GDPR, HIPAA alignment | Legal and regulatory adherence |
| Monitoring | Real-time logs, SIEM integration | Enhanced threat response |
Which enterprise VPN services offer the strongest data privacy protections for US-based organizations?

For US-based organizations seeking the strongest data privacy protections in enterprise VPN services, the top solutions prioritize end-to-end encryption, strict no-logs policies, and jurisdiction outside Five Eyes alliances, with providers like Perimeter 81, Twistlock/Palo Alto Networks, and NordLayer (from NordVPN) offering advanced features including military-grade AES-256 encryption, zero-trust network access (ZTNA) frameworks, and independent audits to verify compliance with stringent data handling standards; these services ensure robust protection against surveillance and data breaches while maintaining seamless scalability for enterprise needs, making them ideal for safeguarding sensitive corporate information in regulated industries.
Key Privacy Features to Evaluate in Enterprise VPNs
When assessing enterprise VPN services for data privacy, US organizations should prioritize features such as strict no-logs policies audited by third parties, end-to-end encryption using protocols like WireGuard or OpenVPN, and split tunneling for controlled data routing; additionally, integration with multi-factor authentication (MFA) and zero-trust architecture enhances security by ensuring that access is granted only to verified users and devices, minimizing the risk of unauthorized exposure even if credentials are compromised.
Comparison of Leading VPN Providers for US Enterprises
The following table highlights core privacy attributes of top-tier enterprise VPN services suitable for US organizations, focusing on their adherence to robust data protection standards:
| Provider | Encryption Standard | No-Logs Policy | Jurisdiction | Additional Features |
|---|---|---|---|---|
| Perimeter 81 | AES-256 | Audited | Israel | ZTNA, SOC 2 Compliance |
| Palo Alto Networks | AES-256 | Strict | USA | Integration with Prisma Access |
| NordLayer | ChaCha20 | Audited | Panama | ThreatBlock, DNS Filtering |
These providers represent the Top VPNs for Enterprise Data Protection in USA, each offering distinct advantages in privacy safeguards and regulatory alignment.
Considerations for Compliance and Data Sovereignty
US organizations must ensure their chosen VPN service complies with regulations like HIPAA, GDPR (if handling EU data), and CCPA, while also evaluating data sovereignty concerns—preferring providers that store logs in jurisdictions with strong privacy laws or offer on-premises deployment options to keep data within US borders; services with ISO 27001 certification or SOC 2 reports provide additional assurance of rigorous data handling practices, reducing legal risks and enhancing trust in privacy protections.
How does an enterprise VPN differ from consumer-grade VPN services in terms of data protection capabilities?
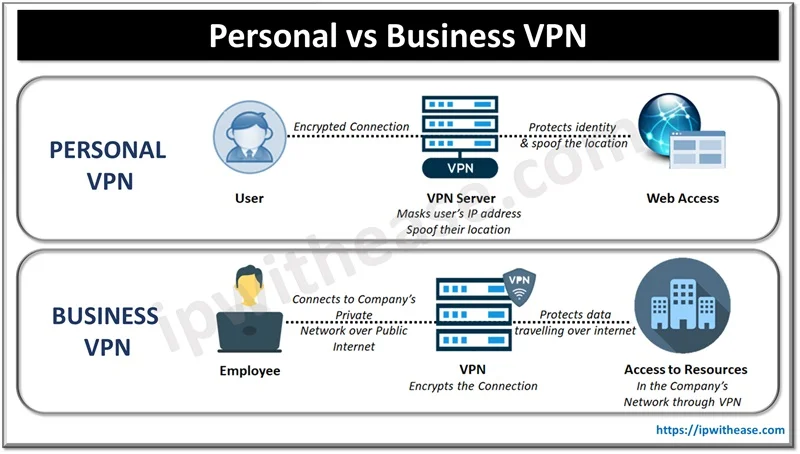
Enterprise VPNs provide fundamentally superior data protection capabilities compared to consumer-grade services through dedicated infrastructure, customized encryption protocols, and comprehensive security frameworks that include end-to-end encryption, granular access controls, and advanced threat protection integrated with existing enterprise security systems, whereas consumer VPNs primarily offer basic tunneling with standardized encryption for general privacy without organizational-level security management or compliance adherence.
Encryption Standards and Protocol Implementation
Enterprise VPNs implement military-grade encryption standards such as AES-256 alongside customizable protocol options including IPsec/IKEv2 or WireGuard, with dedicated hardware security modules for key management, whereas consumer services typically offer limited protocol choices with standardized encryption that lacks customization for specific organizational security policies or regulatory requirements, making enterprise solutions essential for handling sensitive corporate data under compliance frameworks like GDPR or HIPAA.
Network Security and Threat Management
Enterprise VPNs incorporate integrated security features such as intrusion prevention systems, malware scanning, and advanced firewalls that operate within the encrypted tunnel, providing layered protection against sophisticated threats, while consumer VPNs generally lack these enterprise-grade security integrations and primarily focus on basic IP masking without proactive threat management capabilities, leaving corporate networks vulnerable without additional security infrastructure.
| Feature | Enterprise VPN | Consumer VPN |
|---|---|---|
| Threat Protection | Integrated IPS/IDS | Basic or none |
| Malware Scanning | Real-time encrypted traffic | Not available |
| Firewall Capabilities | Advanced application control | Basic port blocking |
Compliance and Data Governance
Enterprise VPN solutions are designed with compliance automation and detailed audit trails that meet strict regulatory requirements for data sovereignty and access logging, providing organizations with demonstrable compliance through comprehensive reporting tools, whereas consumer VPN services operate with minimal logging policies that lack the granularity and retention periods necessary for legal or regulatory scrutiny, making them unsuitable for enterprises handling protected data categories; this is particularly crucial when evaluating Top VPNs for Enterprise Data Protection in USA where regulations like CCPA and sector-specific requirements mandate rigorous data handling protocols.
More information of interest
What are the key criteria for selecting a VPN for enterprise data protection in the USA?
When selecting a VPN for enterprise data protection in the USA, key criteria include robust encryption standards (such as AES-256), strict no-logs policies, secure tunneling protocols like OpenVPN or WireGuard, and compliance with regulations such as GDPR or HIPAA if applicable. Additionally, features like multi-factor authentication, dedicated IP options, and reliable customer support are essential for safeguarding sensitive business data.
How do enterprise VPNs ensure compliance with US data protection regulations?
Enterprise VPNs ensure compliance with US data protection regulations by implementing end-to-end encryption, adhering to frameworks like NIST guidelines, and maintaining transparent data handling practices. Providers often undergo third-party audits and offer features such as data loss prevention (DLP) integration and customizable logging policies to meet specific regulatory requirements, including those from sector-specific laws like CCPA or sector-agnostic standards.
What distinguishes top-tier enterprise VPNs from consumer-grade options?
Top-tier enterprise VPNs distinguish themselves through scalable architecture, centralized management consoles, and advanced security features like threat detection and granular access controls. Unlike consumer-grade options, they offer dedicated servers, SLA-backed uptime guarantees, and integration capabilities with existing IT infrastructure, ensuring seamless and secure operations for organizations of all sizes.
Can enterprise VPNs protect against advanced cyber threats targeting US businesses?
Yes, enterprise VPNs can protect against advanced cyber threats by incorporating intrusion prevention systems (IPS), malware blocking, and real-time monitoring. Many top providers also offer zero-trust network access (ZTNA) principles and regular security updates to mitigate risks such as ransomware, phishing, or data breaches, making them a critical component of a layered defense strategy.






Deja una respuesta