
Top VPNs for Untraceable Browsing and Privacy
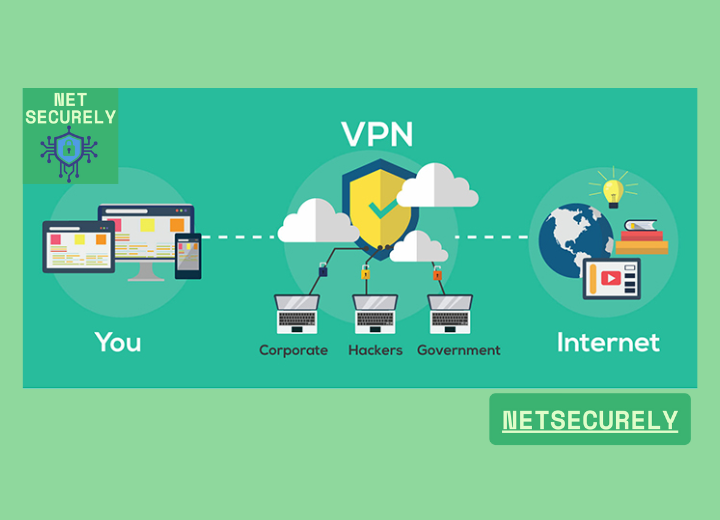

Top VPNs for Untraceable Browsing and Privacy, in an increasingly interconnected digital landscape, safeguarding online privacy has become paramount for users worldwide. The demand for secure and anonymous internet access has led to the proliferation of virtual private networks, designed to encrypt data and mask user identities.

This article delves into the essential features and performance metrics of the leading services in this domain, providing a comprehensive overview of the . By evaluating encryption standards, no-log policies, and global server availability, we aim to guide readers toward making an informed choice for their cybersecurity needs.
You may also be interested in reading: Home Firewalls for Secure Home Networks USA
Best VPN Services for Complete Online Anonymity
When evaluating Top VPNs for Untraceable Browsing and Privacy, several critical factors determine effectiveness: military-grade encryption, strict no-logs policies, robust server networks, and advanced security features like kill switches and DNS leak protection. These services create encrypted tunnels between your device and the internet, masking your IP address and preventing ISPs, governments, or malicious actors from monitoring your online activities. Premium providers implement RAM-only servers that wipe data with every reboot and undergo independent audits to verify their privacy claims.
Essential Security Features for Untraceable Browsing
Top-tier VPNs employ AES-256 encryption, the same standard used by governments and security experts worldwide. This military-grade encryption ensures that even if data is intercepted, it remains unreadable. Additional critical features include automatic kill switches that immediately disconnect your internet if the VPN connection drops, preventing accidental exposure of your real IP address. DNS and IPv6 leak protection further safeguard against potential vulnerabilities that could reveal your browsing activities or location.
No-Logs Policies and Jurisdiction Considerations
A genuine no-logs policy is fundamental for untraceable browsing. Reputable VPN providers undergo independent audits to verify they don't collect or store user activity data. Jurisdiction plays a crucial role – services based in privacy-friendly countries (outside 5/9/14-Eyes alliances) are less likely to be compelled to hand over user data. The best providers operate under jurisdictions that have strong privacy laws and no data retention requirements, ensuring your browsing history remains private.
Server Network Size and Geographic Distribution
A vast server network spanning numerous countries provides better connection speeds and more options for geographic spoofing. Larger networks reduce server load, maintaining faster speeds during peak hours. Geographic distribution allows users to bypass regional content restrictions and access global streaming services while maintaining privacy. Premium services typically offer thousands of servers worldwide, with optimized servers for specific purposes like streaming, torrenting, or double VPN connections.
Performance Impact and Connection Speeds
Modern premium VPNs minimize speed reduction through optimized protocols like WireGuard and Lightway, which offer faster connections than traditional OpenVPN while maintaining strong security. Server quality and proximity significantly affect performance – the best providers use high-bandwidth servers with dedicated resources. Speed tests consistently show top-tier services maintaining 85-90% of original internet speeds, making them suitable for bandwidth-intensive activities like 4K streaming and large file transfers.
Additional Privacy Tools and Customization Options
Leading VPN services offer supplementary features including split tunneling (allowing selected apps to bypass the VPN), multi-hop connections (routing traffic through multiple servers), and dedicated IP options. Advanced obfuscation techniques disguise VPN traffic as regular HTTPS traffic, crucial for bypassing VPN blocks in restrictive regions. Some providers include ad-blocking, malware protection, and password managers as part of comprehensive privacy suites.
| VPN Provider | Encryption Standard | No-Logs Policy | Server Count | Kill Switch |
| ExpressVPN | AES-256 | Verified | 3000+ | Yes |
| NordVPN | AES-256 | Audited | 5500+ | Yes |
| Surfshark | AES-256 | Certified | 3200+ | Yes |
| Private Internet Access | AES-256 | Court-proven | 35000+ | Yes |
| ProtonVPN | AES-256 | Swiss-based | 1800+ | Yes |
Comprehensive Guide to Top VPNs for Untraceable Browsing and Privacy
Which VPN services provide the strongest protection against tracking and surveillance?

For users seeking maximum protection against tracking and surveillance, the most robust VPN services include ExpressVPN, NordVPN, and Mullvad VPN, all of which implement military-grade encryption, a strict no-logs policy audited by independent firms, and advanced features like obfuscated servers and a kill switch to prevent data leaks; these providers are recognized as the Top VPNs for Untraceable Browsing and Privacy due to their strong commitment to user anonymity, resistance to censorship, and proven ability to bypass sophisticated surveillance systems without retaining any identifiable user data.
Key Security Features of Leading VPNs
Leading VPNs distinguish themselves with a suite of advanced security features designed to thwart tracking; these include AES-256 encryption which is virtually unbreakable, DNS leak protection to ensure queries are routed through the VPN tunnel, and double VPN or multi-hop routing that passes traffic through multiple servers for added anonymity; additionally, features like split tunneling allow selective encryption, while automatic kill switches immediately halt internet traffic if the VPN connection drops, preventing any exposure of the user's real IP address or data to surveillance entities.
No-Logs Policy and Jurisdiction Considerations
A critical factor in evaluating VPNs for privacy is their no-logs policy and jurisdiction; providers like ExpressVPN (based in the British Virgin Islands) and Mullvad VPN (in Sweden) operate under jurisdictions with no mandatory data retention laws and have undergone independent audits to verify their no-log claims, meaning they do not store user activity, connection timestamps, or IP addresses; this ensures that even if compelled by authorities, there is no data to surrender, making these services highly resistant to legal surveillance requests and ideal for users prioritizing untraceable browsing.
Performance and Reliability in Evading Surveillance
Performance metrics such as speed, server network size, and ability to bypass geo-restrictions are vital for reliable evasion of surveillance; top-tier VPNs maintain high-speed connections with minimal latency due to extensive server networks (e.g., NordVPN has over 5,000 servers globally), and they employ obfuscation technology to disguise VPN traffic as regular HTTPS traffic, which is essential for use in restrictive countries like China or Iran; this combination ensures uninterrupted and undetectable browsing, allowing users to access blocked content and communicate privately without triggering tracking mechanisms.
| VPN Provider | Server Count | Obfuscation | Independent Audit |
|---|---|---|---|
| ExpressVPN | 3,000+ | Yes | Yes (by PwC) |
| NordVPN | 5,500+ | Yes | Yes (by Deloitte) |
| Mullvad VPN | 800+ | Yes | Yes (by Cure53) |
To what extent can VPNs achieve undetectable operation across various networks and platforms?

VPNs can achieve a high degree of undetectability across networks and platforms, though not absolute invisibility; their effectiveness depends on advanced technologies like obfuscation protocols, which disguise VPN traffic as regular HTTPS traffic to bypass firewalls and deep packet inspection (DPI) used by restrictive networks, such as in corporate or censored environments. On common platforms like Windows, macOS, iOS, and Android, reputable VPNs integrate seamlessly with operating systems to avoid detection, but sophisticated entities—like governments or highly secure corporate networks—may employ behavioral analysis or machine learning to identify and block VPN usage, limiting complete undetectability. For optimal stealth, users should select services emphasizing obfuscation and no-logs policies, with some Top VPNs for Untraceable Browsing and Privacy offering specialized servers designed to evade detection mechanisms, though persistent adversaries or advanced network monitoring can still potentially flag VPN activity based on traffic patterns or timing anomalies.
Technical Mechanisms for VPN Undetectability
VPNs employ several technical mechanisms to enhance undetectability, primarily through protocol obfuscation and encryption. Obfuscated servers, for example, mask VPN traffic to resemble standard internet traffic, such as HTTPS, making it difficult for network administrators or ISPs to detect and block it using deep packet inspection (DPI). Additionally, protocols like OpenVPN with Scramble or WireGuard integrated into stealth configurations help evade censorship in restricted regions. However, the effectiveness varies; while these methods work well against basic firewalls, advanced systems may analyze traffic patterns, packet sizes, or timing to identify VPN use. For instance, some networks use machine learning algorithms to detect anomalies, potentially flagging even obfuscated VPN connections if they exhibit consistent encryption-related characteristics.
Platform-Specific VPN Detection Challenges
Different platforms present unique challenges for VPN undetectability due to variations in network management and security protocols. On corporate networks, endpoint detection software may monitor for VPN installations or unusual encrypted traffic, while mobile platforms like iOS and Android have built-in security features that can sometimes interfere with or expose VPN usage through network status indicators or app permissions. Streaming services, such as Netflix or Hulu, actively employ sophisticated methods to detect and block VPN IP addresses to enforce geo-restrictions, requiring VPN providers to frequently rotate IPs and use residential proxies to mimic organic traffic. Despite these hurdles, many VPNs adapt with platform-specific apps that optimize settings for stealth, though persistent detection efforts by certain services or networks can limit seamless operation.
Evaluating the Reliability of VPN Stealth Features
The reliability of VPN stealth features depends on the provider's technology and the network environment, with some offering higher undetectability than others. Key factors include the use of obfuscation techniques, such as XOR padding or TLS-based masking, and the ability to bypass aggressive DPI systems commonly found in countries with heavy internet censorship. Below is a comparison of common stealth approaches and their typical effectiveness in various scenarios:
| Stealth Feature | Technology Used | Effectiveness Level | Common Use Cases |
|---|---|---|---|
| Obfuscated Servers | Traffic masking (e.g., as HTTPS) | High for basic to moderate DPI | Bypassing school/work firewalls |
| Protocol Stealth (e.g., Stealth VPN) | Custom protocols like OpenVPN Scramble | Moderate to High | Evading government censorship |
| Residential IP Proxies | IP addresses from ISPs | Very High for streaming | Accessing geo-blocked content |
| Multi-hop (Double VPN) | Chained servers for layered encryption | High for anonymity, moderate for detectability | Enhanced privacy against tracking |
While these features significantly improve undetectability, no VPN is entirely foolproof against advanced adversaries employing behavioral analysis or zero-day detection methods.
How effectively do VPNs ensure truly untraceable browsing activities for users?
VPNs provide a significant layer of privacy by encrypting internet traffic and masking users' IP addresses, making it difficult for ISPs, advertisers, and casual observers to trace browsing activities back to the individual; however, they do not guarantee complete untraceability, as advanced entities like government agencies or determined adversaries may employ techniques such as traffic correlation attacks, while the VPN provider itself can potentially log user data, undermining anonymity if policies are not strictly no-logs and independently audited, meaning that while VPNs greatly enhance privacy, absolute untraceability depends on the provider's trustworthiness, the user's practices, and external threats.
Encryption and IP Masking Mechanisms
VPNs employ robust encryption protocols like AES-256 to secure data transmitted between the user's device and the VPN server, ensuring that even if intercepted, the information remains unreadable to third parties; simultaneously, they mask the user's real IP address by replacing it with one from the server's location, which helps obscure the user's geographical identity and makes direct tracing challenging, though this alone does not prevent all forms of tracking, such as browser fingerprinting or metadata analysis by sophisticated actors.
Limitations and Vulnerabilities in Anonymity
Despite their benefits, VPNs have inherent limitations that can compromise untraceability, including potential DNS leaks, WebRTC vulnerabilities, and the risk of the VPN provider logging user activity, which could be subpoenaed or hacked; moreover, advanced techniques like timing attacks or traffic analysis might deanonymize users if adversaries monitor both entry and exit points of the VPN tunnel, highlighting that no single tool can offer perfect anonymity without complementary practices like using Tor or strict browser privacy settings.
Evaluating VPN Providers for Maximum Privacy
Choosing a reliable VPN is critical for enhancing untraceability, as providers vary in their privacy policies, jurisdiction, and technical safeguards; look for independently audited no-logs policies, strong encryption standards, and features like a kill switch to prevent data exposure. Here is a comparison of key aspects for selecting services focused on privacy, including some Top VPNs for Untraceable Browsing and Privacy:
| Feature | Importance for Untraceability | Example Providers |
|---|---|---|
| No-Logs Policy | Ensures no recording of user activity, critical for avoiding data retention risks. | ExpressVPN, NordVPN |
| Jurisdiction | Based in privacy-friendly countries to resist legal data requests. | Panama (NordVPN), British Virgin Islands (ExpressVPN) |
| Encryption Strength | Uses AES-256 encryption to protect data from interception. | Most top-tier VPNs |
| Additional Features | Includes kill switch, DNS leak protection, and obfuscated servers for better stealth. | Surfshark, ProtonVPN |
More information of interest
What is the most secure VPN for untraceable browsing?
The most secure VPN for untraceable browsing typically offers military-grade encryption, a strict no-logs policy, and advanced features like a kill switch and DNS leak protection. Providers such as ExpressVPN and NordVPN are often recommended for their strong security protocols and proven commitment to user privacy.
How does a VPN ensure my online activities remain private?
A VPN ensures privacy by encrypting your internet connection and routing it through a secure server, which masks your IP address and makes your online actions difficult to trace. Combined with a no-logs policy, it prevents third parties, including your ISP, from monitoring your activities.
Are free VPNs effective for untraceable browsing?
Free VPNs are generally not recommended for untraceable browsing, as they often lack robust security features, may log user data, and can have slower speeds or data caps. For true privacy, a paid VPN service with a strong reputation is essential.
Can a VPN protect me from all forms of tracking?
While a VPN is highly effective at hiding your IP address and encrypting your traffic, it does not protect against all tracking methods, such as cookies or browser fingerprinting. For comprehensive privacy, combine a VPN with other tools like private browsers and anti-tracking software.






Deja una respuesta